Detours is a library developed by Microsoft Research in 1999. It was originally intended as a way to easily instrument and extend existing OS and application functionality. The Detours library makes it possible for a developer to make application modifications simply.
Malware authors like Detours, too, and they use the Detours library to perform import table modification, attach DLLs to existing program files, and add function hooks to running processes.
Malware authors most commonly use Detours to add new DLLs to existing binaries on disk. The
malware modifies the PE structure and creates a section named .detour, which is typically placed between the export table and any debug symbols. The
.detour section contains the original PE header with a new import
address table. The malware author then uses Detours to modify the PE header to point to the new
import table, by using the setdll tool provided with the Detours
library.
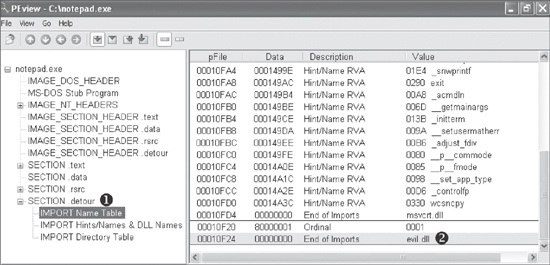
Figure 12-4 shows a PEview of Detours being used to
trojanize notepad.exe. Notice in the .detour
section at ❶ that the new import table contains
evil.dll, seen at ❷.
Evil.dll will now be loaded whenever Notepad is launched. Notepad will continue
to operate as usual, and most users would have no idea that the malicious DLL was executed.
Instead of using the official Microsoft Detours library, malware authors have been known to
use alternative and custom methods to add a .detour section. The
use of these methods for detour addition should not impact your ability to analyze the
malware.