OllyDbg has standard plug-ins and many additional ones available for download. You’ll find a decent collection of OllyDbg plug-ins that are useful for malware analysis at http://www.openrce.org/downloads/browse/OllyDbg_Plugins.
OllyDbg plug-ins come as DLLs that you place in the root OllyDbg install directory. Once in that directory, the plug-ins should be recognized automatically and added to the Plugins menu.
Note
Writing plug-ins in OllyDbg can be a tedious process. If you wish to extend the functionality of OllyDbg, we recommend writing Python scripts, as described later in the chapter, in Scriptable Debugging.
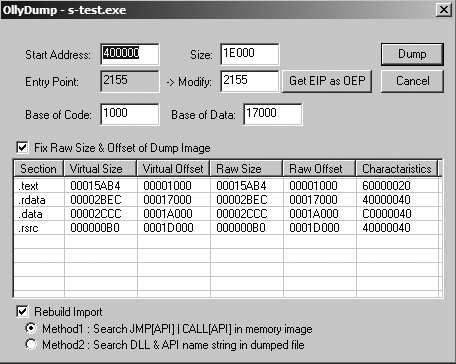
OllyDump is the most commonly used OllyDbg plug-in because it provides the ability to dump a debugged process to a PE file. OllyDump tries to reverse the process that the loader performed when it loaded the executable; however, it will use the current state of the various sections (code, data, and so on) as they exist in memory. (This plug-in is typically used for unpacking, which we’ll discuss extensively in Chapter 18.)
Figure 9-16 shows the OllyDump window. When dumping, you can manually set the entry point and the offsets of the sections, although we recommend that you let OllyDbg do this for you automatically.
The Hide Debugger plug-in employs a number of methods to hide OllyDbg from debugger detection. Many malware analysts run this plug-in all the time, just in case the malware employs anti-debugging.
This plug-in specifically protects against IsDebuggerPresent checks, FindWindow checks, unhandled
exception tricks, and the OuputDebugString exploit against
OllyDbg. (We discuss anti-debugging techniques in Chapter 16.)
The Command Line plug-in allows you to have command-line access to OllyDbg. The command line can create a WinDbg-like experience, although not many users of OllyDbg take advantage of it. (The WinDbg debugger is discussed in the next chapter.)
To activate the command-line window, select Plugins ▶ Command Line ▶ Command Line. Table 9-3 shows the list of common commands. Additional commands can be found in the help file that comes with the Command Line plug-in.
Table 9-3. Commands for the OllyDbg Command Line
Command | Function |
|---|---|
| Set software breakpoint |
| Remove breakpoint |
| Set hardware breakpoint on execution |
| Set breakpoint on each call to label |
| Pause execution |
| Run program |
| Run until address |
| Step into |
| Step over |
| Dump memory |
When debugging, you will often want to break execution at the start of an imported function in order to see the parameters being passed to that function. You can use the command line to quickly set a breakpoint at the start of an imported function.
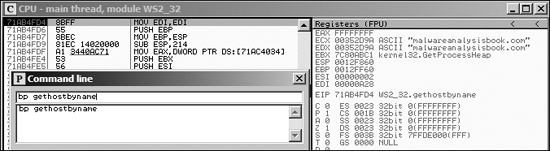
In the example in Figure 9-17, we have a piece
of malware with strings obfuscated; however, it has an import of gethostbyname. As shown in the figure, we execute the command bp
gethostbyname at the command line, which sets a breakpoint at the start of the gethostbyname function. After we set the breakpoint, we run the program,
and it breaks at the start of gethostbyname. Looking at the
parameters, we see the hostname it intends to resolve (malwareanalysisbook.com in this example).
The Bookmarks plug-in is included by default in OllyDbg. It enables you to add bookmarks of memory locations, so that you can get to them easily in the future without needing to remember the addresses.
To add a bookmark, right-click in the disassembler window and select Bookmark ▶ Insert Bookmark. To view bookmarks, select Plugins ▶ Bookmarks ▶ Bookmarks, and then click any of your bookmarks to go to that location.