There are several ways to begin debugging malware with OllyDbg. You can load executables and even DLLs directly. If malware is already running on your system, you can attach to the process and debug that way. OllyDbg provides a flexible system to run malware with command-line options or to execute specific functionality within a DLL.
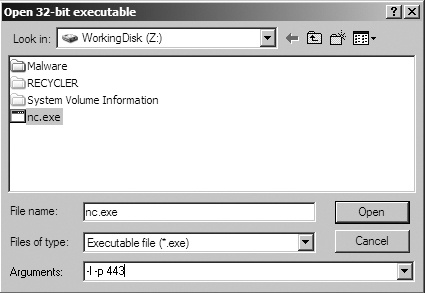
The easiest way to debug malware is to select File ▶ Open, and then browse to the executable you wish to load, as shown in Figure 9-1. If the program you are debugging requires arguments, specify them in the Arguments field of the Open dialog. (During loading is the only time you can pass command-line arguments to OllyDbg.)
Once you’ve opened an executable, OllyDbg will load the binary using its own loader. This works similarly to the way that the Windows OS loads a file.
By default, OllyDbg will pause at the software developer’s entry point, known as
WinMain, if its location can be determined. Otherwise, it will
break at the entry point as defined in the PE header. You can change these startup options by
selecting from OllyDbg’s Debugging Options menu (Options ▶
Debugging Options). For example, to break immediately before any code executes, select
System Breakpoint as the startup option.
Note
OllyDbg 2.0 has more breaking capabilities than version 1.1. For example, it can be set to pause at the start of a TLS callback. TLS callbacks can allow malware to execute before OllyDbg pauses execution. In Chapter 16, we discuss how TLS callbacks can be used for anti-debugging and how to protect yourself from them.
In addition to opening an executable directly, you can attach OllyDbg to a running process. You’ll find this feature useful when you want to debug running malware.
To attach OllyDbg to a process, select File ▶ Attach. This will bring up a menu in which you can select the process to which you want to attach. (You’ll need to know the process ID if there is more than one process with the same name.) Next, select the process and choose Attach from the menu. OllyDbg should break in and pause the program and all threads.
Once you are attached with OllyDbg, the current executing thread’s code will be paused and displayed on your screen. However, you might have paused while it was executing an instruction from within a system DLL. You don’t want to debug Windows libraries, so when this happens, the easiest way to get to the main code is to set a breakpoint on access to the entire code section. This will cause the program to break execution the next time the code section is accessed. We will explain setting breakpoints like these later in this chapter.