In addition to being able to load and attach to executables, OllyDbg can also debug DLLs.
However, since DLLs cannot be executed directly, OllyDbg uses a dummy program called
loaddll.exe to load them. This technique is extremely useful, because malware
often comes packaged as a DLL, with most of its code contained inside its DllMain function (the initialization function called when a DLL is loaded into a
process). By default, OllyDbg breaks at the DLL entry point (DllMain) once the DLL is loaded.
In order to call exported functions with arguments inside the debugged DLL, you first need to
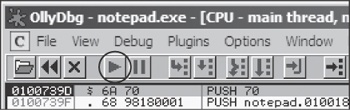
load the DLL with OllyDbg. Then, once it pauses at the DLL entry point, click the play button to run
DllMain and any other initialization the DLL requires, as shown
in Figure 9-9. Next, OllyDbg will pause, and you can call specific
exports with arguments and debug them by selecting Debug ▶ Call DLL
Export from the main menu.
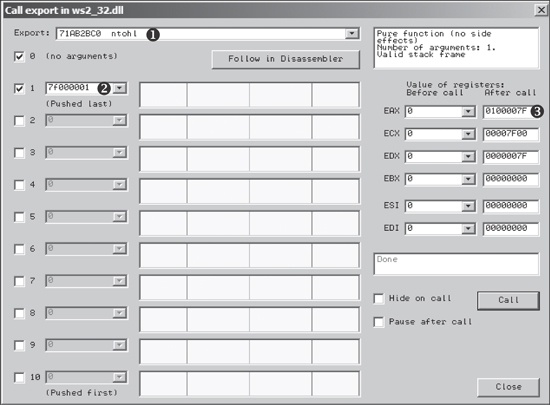
For example, in Figure 9-10, we have loaded
ws2_32.dll into OllyDbg and called the ntohl
function at ❶, which converts a 32-bit number from
network to host byte order. On the left, we can add any arguments we need. Here, we add one
argument, which is 127.0.0.1 (0x7F000001) in network byte order
at ❷. The boxes on the left are checked only where we
are supplying arguments.
You can quickly view the assembly instructions for ntohl by clicking the Follow in Disassembler button.
The Hide on call checkbox on the bottom right can be used to hide this window after you perform a
call. The Pause after call checkbox is useful for pausing execution immediately after the export is
called, which can be a useful alternative to using breakpoints.
Once you have set up your arguments and any registers, click the Call button at the bottom right to force the call to take place. The OllyDbg window should then show the value of all registers before and after the call.
To debug this exported function, be sure to set any breakpoints before clicking Call, or check the Pause after call checkbox. In Figure 9-10, you see the result of the function stored in EAX, which is 127.0.0.1 (0x0100007F) in host byte order shown at ❸.