OllyDbg makes it easy to modify just about any live data, such as registers and flags. It also enables you to assemble and patch code directly into a program. You can modify instructions or memory by highlighting a region, right-clicking that region, and selecting Binary ▶ Edit. This will pop up a window for you to add any opcodes or data. (OllyDbg also has special functions to fill with 00 entries, or NOP instructions.)
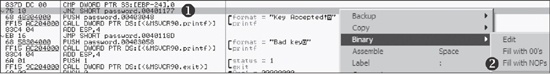
Figure 9-13 shows a section of code from a
password-protected piece of malware that requires that a special key be input in order to configure
the malware. We see an important check and conditional jump (JNZ)
at ❶ decide if the key is accepted. If the jump is
taken, Bad key will be printed; otherwise, it will print Key Accepted!. A simple way to force the program to go the keyaccepted
route is to apply a patch. As shown in Figure 9-13, highlight the
conditional jump instruction, right-click, and select Binary ▶ Fill
with NOPs, as at ❷. This will change the
JNZ instruction to NOPs, and the program will think that a key
has been accepted.
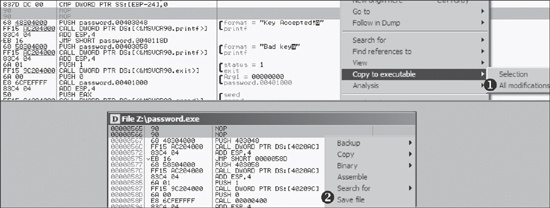
Note that the patch is in live memory only for this instance of the process. We can take the patching a step further by copying the change out to an executable. This is a two-step process, as outlined in Figure 9-14.
To apply this change, right-click the disassembler window where you patched the code and select Copy to Executable ▶ All Modifications as shown at ❶. This will copy all changes you have made in live memory and pop up a new window, as shown at the bottom of Figure 9-14. Select Save File, as shown at ❷, to save it to disk.
Notice that Figure 9-14 contains the same code
as Figure 9-13, except the JNZ
instruction has been replaced by two NOP instructions. This procedure would permanently store NOPs
at that location in the executable on disk, meaning that any key will be accepted by the malware
permanently. This technique can be useful when you wish to permanently modify a piece of malware in
order to make it easier to analyze.