The tool that we will use in the NetHunter platform is the Mana Wireless Toolkit. Navigate from the NetHunter icon to Mana Wireless Toolkit. The first page that you are brought to is the hostapd-karma.conf screen.
This allows us to configure our evil AP wireless access point:
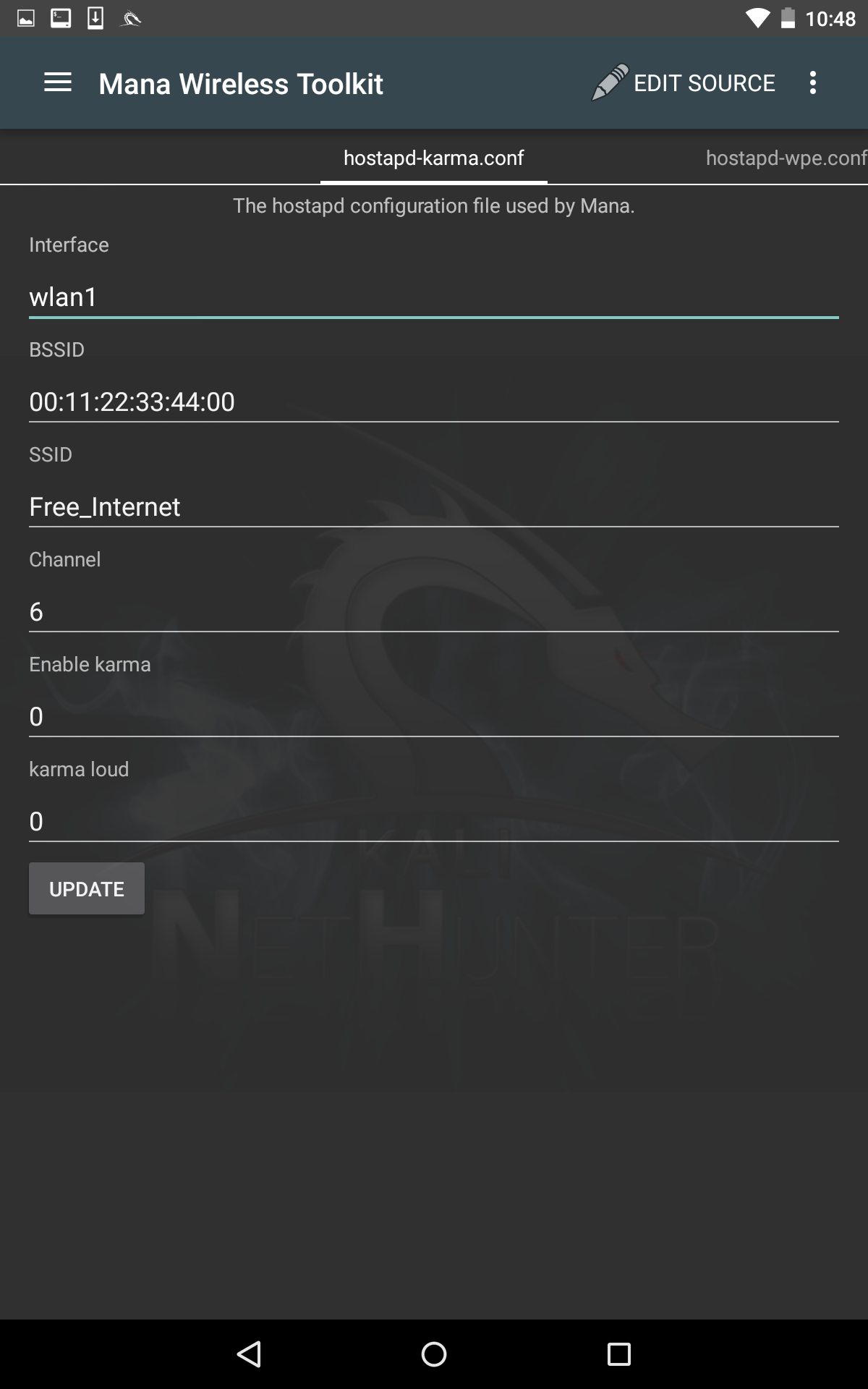
The first consideration is that you will need to ensure you have two wireless interfaces available. The Android wireless interface, most likely WLAN0, will need to be connected to an access point with internet connectivity. This can be controlled by you, or could simply be the free wireless internet available at our location. The WLAN1 interface will be our external antenna, which will provide the fake access point. Next, you can configure the BSSID to a MAC that mimics an actual access point's. In addition, we can also configure the SSID to broadcast any access-point identification. The other settings involve attacking using the Karma exploit. This is a variation on the evil AP. (For more information, see https://insights.sei.cmu.edu/cert/2015/08/instant-karma-might-still-get-you.html.) We can leave those as default. In this scenario, we will keep the default settings and navigate to the three vertical dots and hit Start mana.
This will start the fake access point:
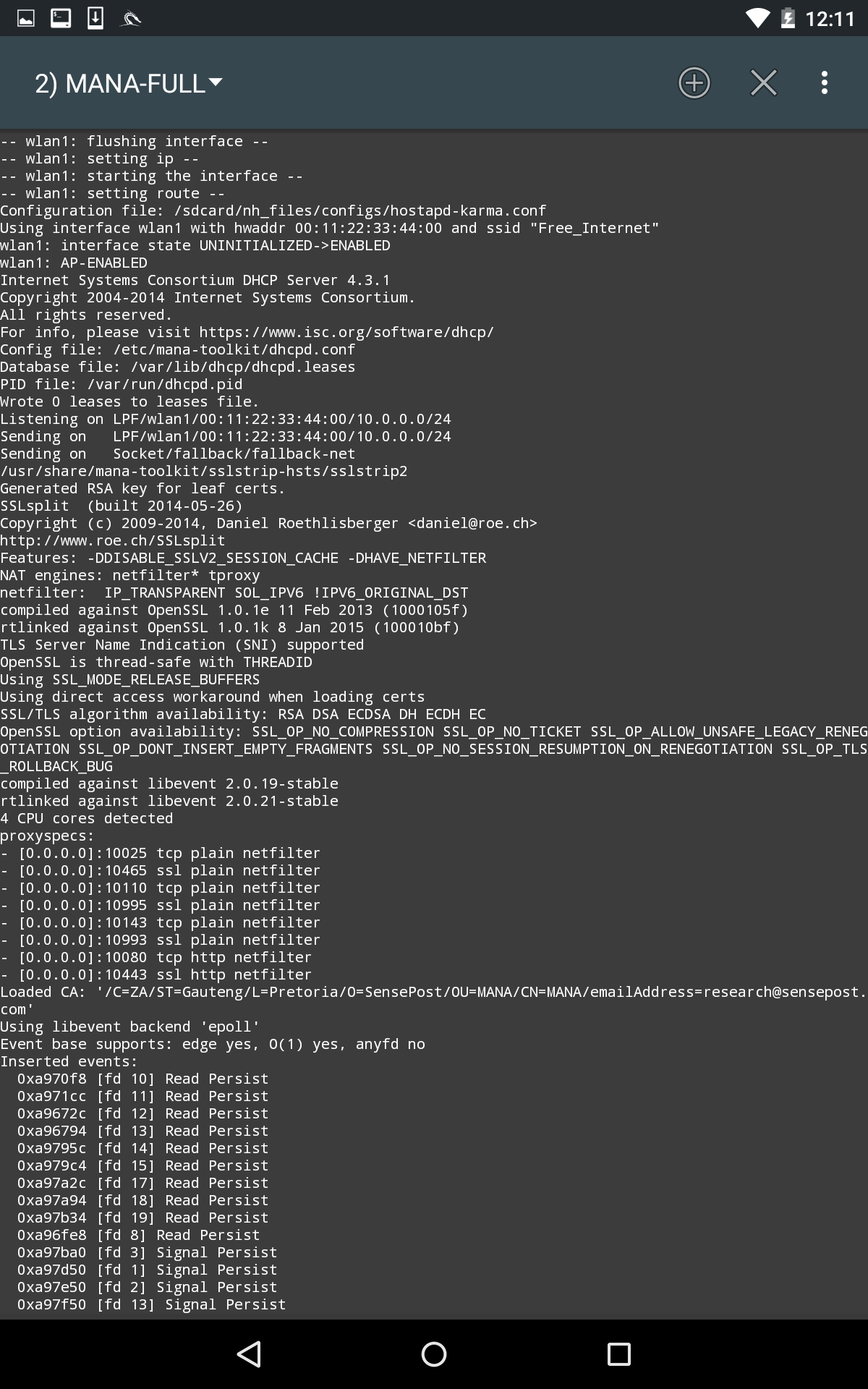
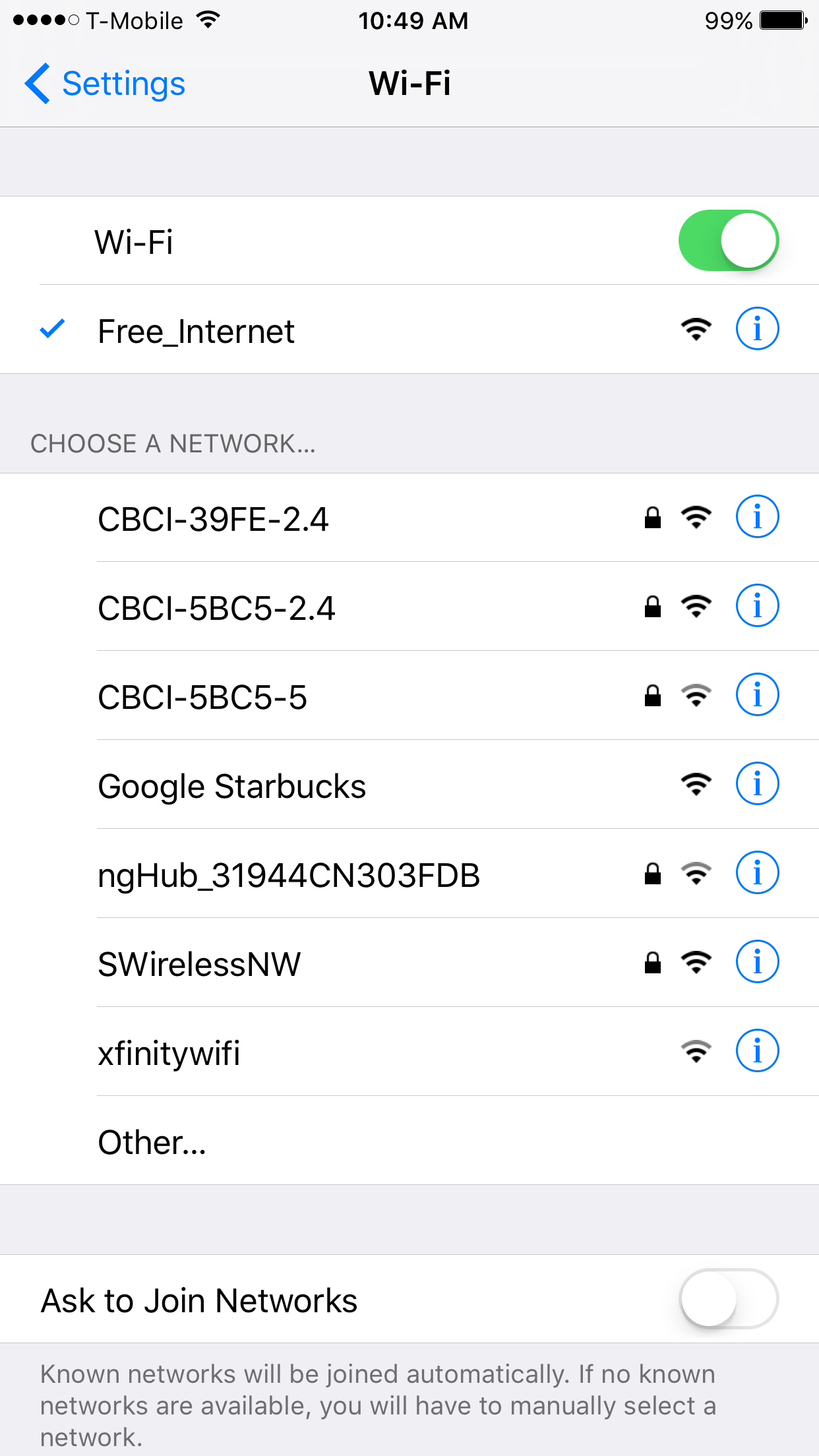
In the previous screenshot, we can see the Mana evil AP flushing out cached information and setting up a new access point. If we shift over to a device, we can see the wireless access point, Free_Internet. Also, we are able to connect without any authentication:
Now, in another Terminal on the NetHunter platform, we configure our packet capture by configuring a tcpdump capture utilizing the following command:
# tcpdump -I wlan1
This produces the following:
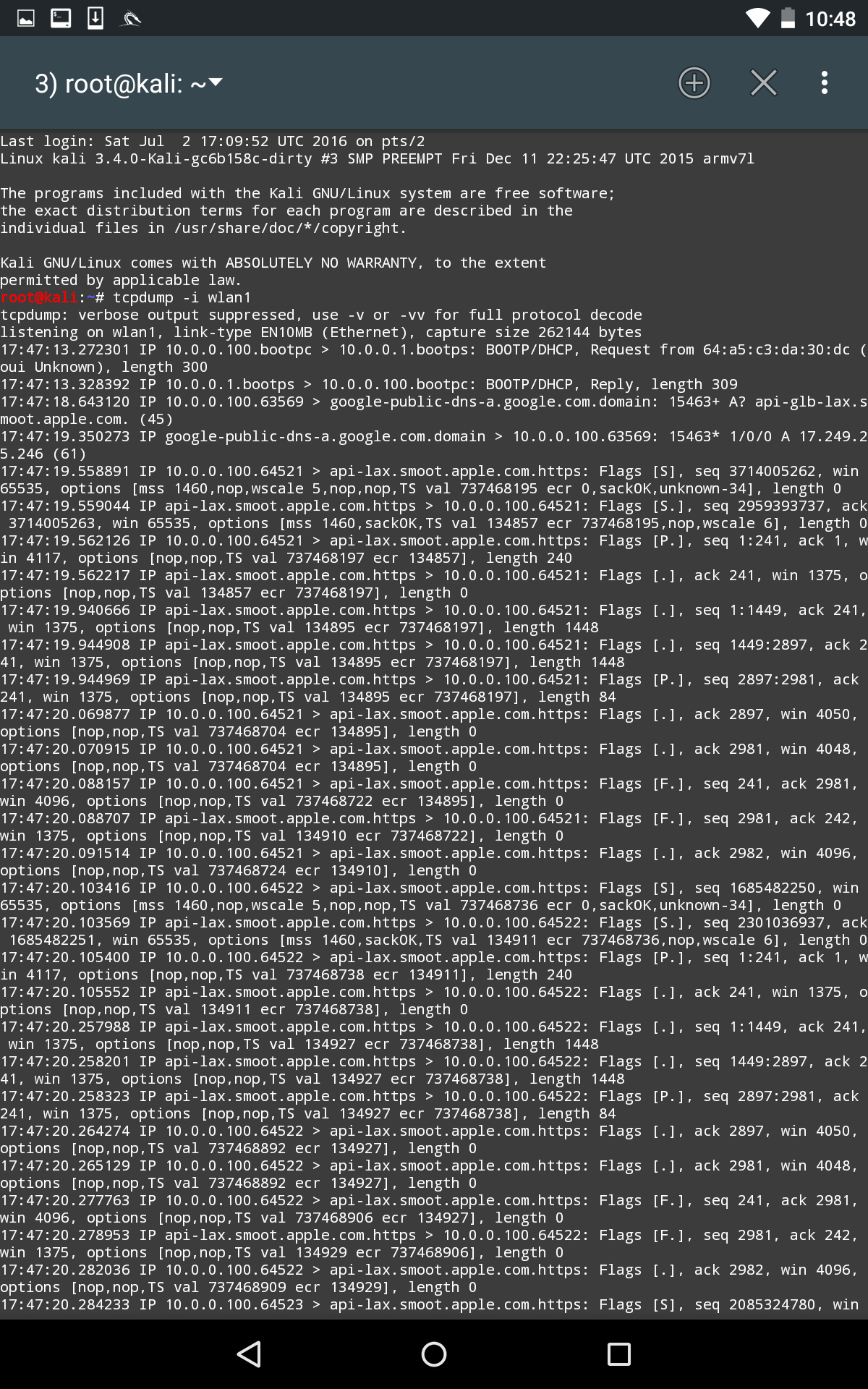
As the device that is connected receives and transmits frames, we are able to sniff that traffic. An additional option that is available is to capture the traffic in the form of a .pcap file and then offload it to view it in Wireshark.
This is a useful attack in public areas of a target organization. Another key aspect to this attack is that more than one target device can connect. It is important to note, though, that if several devices do connect, there is the possibility that the traffic will be noticeably slower to the target. Another technique that can be used leverages this tool and a vulnerability found in a number of mobile devices. Many mobile devices are automatically configured to connect to any previously connected-to network. This automatic connection does not look at the MAC address of a wireless access point, but rather the SSID that is being broadcast. In this scenario, we can call our Mana evil AP a common SSID found at locations. As people pass by, their mobile devices will automatically connect, and as long as they are in range, they are routing their traffic through our device.
