The hping3 tool is a command-line network-packet generator and analyzer tool. The capability to create custom network packets allows hping3 to be used for TCP/IP and security testing, such as port scanning, firewall-rule testing, and network-performance testing.
The following are several other uses of hping3, according to the developer:
- Testing firewall rules
- Testing IDS
- Exploiting known vulnerabilities in the TCP/IP stack
To access hping3, go to the console and type hping3.
You can give commands to hping3 in several ways, via the command line, interactive shell, or script.
Without any given command-line options, hping3 will send a null TCP packet to port 0.
In order to change to a different protocol, you can use the following options in the command line to define the protocol:
|
No. |
Short option |
Long option |
Description |
|
1 |
-0 |
--raw-ip |
This sends raw IP packets |
|
2 |
-1 |
--icmp |
This sends ICMP packets |
|
3 |
-2 |
--udp |
This sends UDP packets |
|
4 |
-8 |
--scan |
This indicates the use of scan mode |
|
5 |
-9 |
--listen |
This indicates the use of listen mode |
When using the TCP protocol, we can use the TCP packet without any flags (this is the default behavior) or we can give one of the following flag options:
|
No. |
Option |
Flag name |
|
1 |
-S |
syn |
|
2 |
-A |
ack |
|
3 |
-R |
rst |
|
4 |
-F |
fin |
|
5 |
-P |
psh |
|
6 |
-U |
urg |
|
7 |
-X |
xmas: flags fin, urg, psh set |
|
8 |
-Y |
ymas |
Let's use hping3 for several cases, as follows.
Send one ICMP echo request packet to a 192.168.56.101 machine. The options used are -1 (for the ICMP protocol) and -c 1 (to set the count to one packet):
hping3 -1 172.16.43.156 -c 1
The following is the output of this command:
# hping3 -1 172.16.43.156 -c 1
HPING 172.16.43.156 (eth0 172.16.43.156): icmp mode set, 28 headers + 0 data bytes
len=46 ip=172.16.43.156 ttl=64 id=63534 icmp_seq=0 rtt=2.5 ms
--- 172.16.43.156 hping statistic ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 2.5/2.5/2.5 ms
From the preceding output, we can identify that the target machine is alive, because it has replied to our ICMP echo request.
To verify this, we captured the traffic using tcpdump and the following screenshot shows the packets:
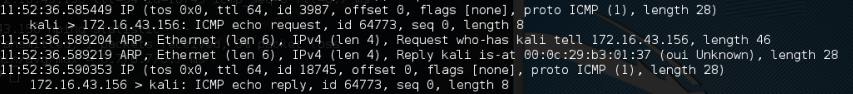
We can see that the target has responded with an ICMP echo reply packet.
Besides giving the options in the command line, you can also use hping3 interactively. Open the console and type hping3. You will then see a prompt where you can type your Tcl commands.
For the preceding example, the following is the corresponding Tcl script:
hping3> hping send {ip(daddr=172.16.43.156)+icmp(type=8,code=0)}
Open a command-line window and give the following command to get a response from the target server:
hping recv eth0
After that, open another command-line window to input the sending request.
The following screenshot shows the response received:
You can also use hping3 to check for a firewall rule. Let's suppose you have the following firewall rules:
- Accept any TCP packets directed to port 22 (SSH)
- Accept any TCP packets related to an established connection
- Drop any other packets
To check these rules, you can give the following command in hping3, in order to send an ICMP echo request packet:
hping3 -1 172.16.43.156 -c 1
The following code is the result:
# hping3 -1 172.16.43.156 -c 1 HPING 172.16.43.156 (eth0 172.16.43.156): icmp mode set, 28 headers + 0 data bytes --- 172.16.43.156 hping statistic --- 1 packets transmitted, 0 packets received, 100% packet loss round-trip min/avg/max = 0.0/0.0/0.0 ms
We can see that the target machine has not responded to our ping probe.
Send a TCP packet with the SYN flag set to port 22, and we will get the result shown in the following screenshot:
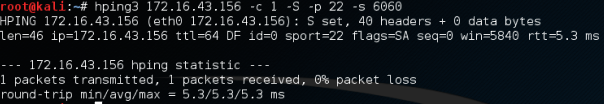
From the preceding screenshot, we can see that the target machine's firewall allows our SYN packet to reach port 22.
Let's check whether the UDP packet is allowed to reach port 22:
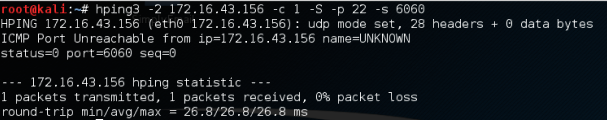
From the preceding screenshot, we can see that the target machine's firewall does not allow our UDP packet to reach port 22.
There are other things that you can do with hping3, but, in this chapter, we'll only discuss a small subset of its capabilities. If you want to learn more, you can consult the hping3 documentation site at http://wiki.hping.org.
