An Evil Access Point (evil AP) attack is a type of wireless MitM attack. In this attack, we are attempting to have a target device or devices connect to a wireless access point we have set up that masquerades as a legitimate access point. Our target, thinking that this is a legitimate network, connects to it. The traffic to and from the client is sniffed while it is forwarded to the legitimate access point downstream. Any traffic that comes from the legitimate access point is also routed through our AP that we have set up and, again, we have the ability to sniff that traffic.
The following diagram illustrates this attack. On the left is our target's laptop. In the middle is our NetHunter platform. To the right is a legitimate access point with a connection to the internet. When the target connects to our NetHunter platform, we are able to sniff the traffic before it is forwarded to the legitimate access point. Any traffic from the access point is also sniffed and then forwarded to the client:
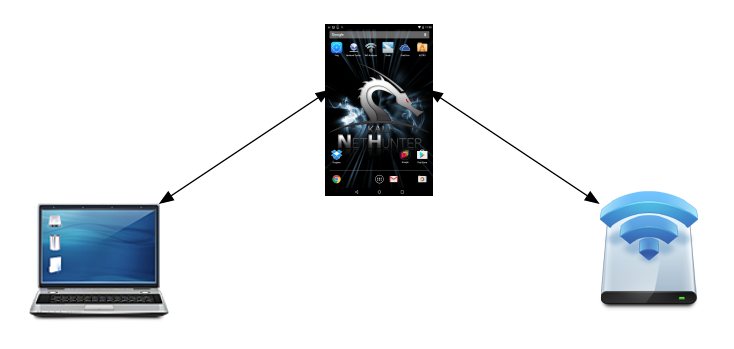
This is simply a variation on the MitM attacks we have discussed in the past. What makes this different is that we do not need to know anything about the client or what network they are on, since we will be controlling the network they use. This is an attack that often occurs in public areas that make use of free wireless internet, such as airports, coffee shops, and hotels.
