The Google Hacking Database (GHDB) can be found at https://www.exploit-db.com/google-hacking-database/ and allows users to use customized advanced queries that may reveal unusual information, which would otherwise not be displayed in a typical results listing on https://www.google.com/.
The GHDB was originally developed by Johnny Long, creator of Hackers for Charity, but is now maintained and hosted by Offensive Security, the makers of Kali Linux. The GHDB uses Googledorks which are Google operators used in search strings such as inurl, filetype, allintext, site, cache, and also operators such as +, -, *, and so on. When used correctly, Googledorks can sometimes reveals interesting and even sensitive information such as error messages, vulnerable servers and websites, sensitive files, and login pages. Of course, most of this information is not readily available via ordinary Google searches, which leads to the use of Google as an information gathering and hacking database tool.
The GHDB is simple enough to use. It allows the user to choose from various categories than typing in phrases and Googledorks. Lower down on the page, it lists many of the categories with search queries, as well as links to the queries leading to a Google search, thus making it very easy even for beginners to use.
As an example, I've chosen Vulnerable Servers from the category list, simply entered apache in the search field, and clicked on SEARCH:
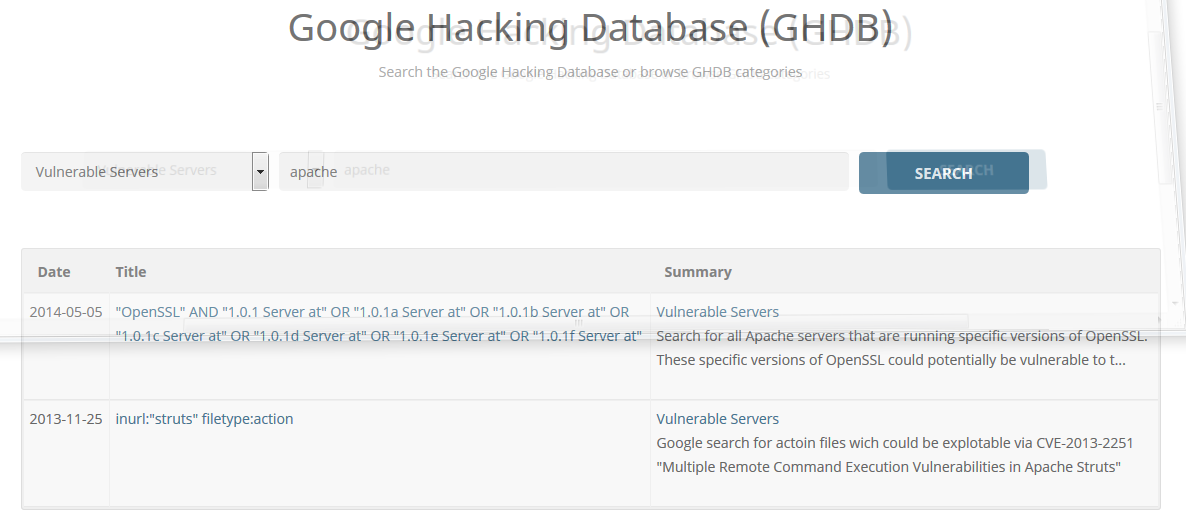
The results listed can be either clicked on or copied and pasted into Google to try and gather more information.
The following screenshot shows the results of the search in Google. Note that there are 16,600 results, but not all results will yield interesting information about vulnerable servers:
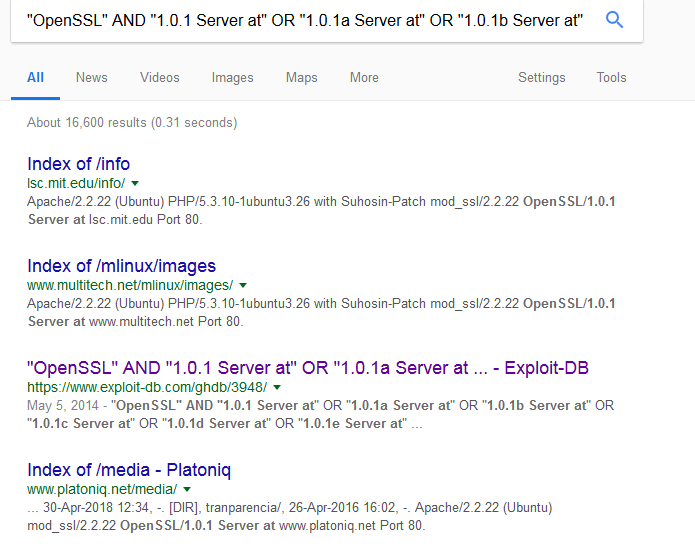
For ethical and legal purposes, you should only use the GHDB for information gathering purposes as it pertains to the laws of your state and country.
