This module will perform a sweep of target IP addresses attempting to locate usernames associated with the Server Message Block (SMB). This service is used by applications for access to file shares, printers, or for communication between devices on the network. Using one of the Metasploit auxiliary scanners, we can determine possible usernames.
First, search Metasploit for scanners by typing the following:
msf> search SMB
We can then see the number of different scanners available to scan for open SMB services:
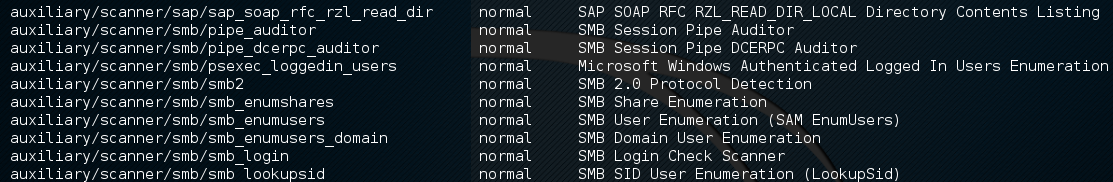
To use the scanner, type the following:
msf> use auxiliary/scanner/smb/smb_enumershares
Set the RHOSTS parameter to the network range, in this case 192.168.0.1/24, by entering the following:
msf> set RHOSTS 192.168.0.1/24
Then, type this:
msf> run
The results of the scan indicate that there is an SMB service running with the METASPLOITABLE username:
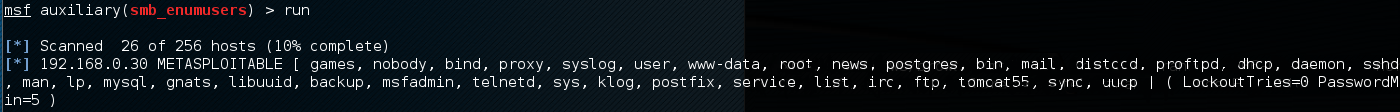
This may indicate open shares or other network services that can be attacked. The METASPLOIT username can also provide us with a starting point when we start cracking user credentials and passwords.
