Nikto is a basic web server security scanner. It scans and detects the vulnerabilities on web applications usually caused by misconfigurations on the server, default and insecure files, and outdated server applications. As Nikto is purely built on LibWhisker2, it supports out-of-the-box cross-platform deployment, SSL, host authentication methods (NTLM/Basic), proxies, and several IDS-evasion techniques. It also supports sub-domain enumeration, application security checks (XSS, SQL injection, and so on), and is capable of guessing authorization credentials using a dictionary-based password attack.
To use nikto, you can navigate to the Applications menu | 03 – Web Application Analysis | Web Vulnerability Scanner | nikto, or in your Terminal simply type the following:
# nikto
By default, as previously seen with other applications, simply running the command will display the different options that we have available. To scan a target, enter nikto -h <target> -p <port>, where <target> is the domain or IP address of your target website and <port> is the port that the service is running on. For this scan, nikto will be targeted at a local VM known as the OSWAP BWA (available at https://sourceforge.net/projects/owaspbwa/files/). OWASP BWA is a collection of deliberately vulnerable web applications in one VMware-based virtual machine:
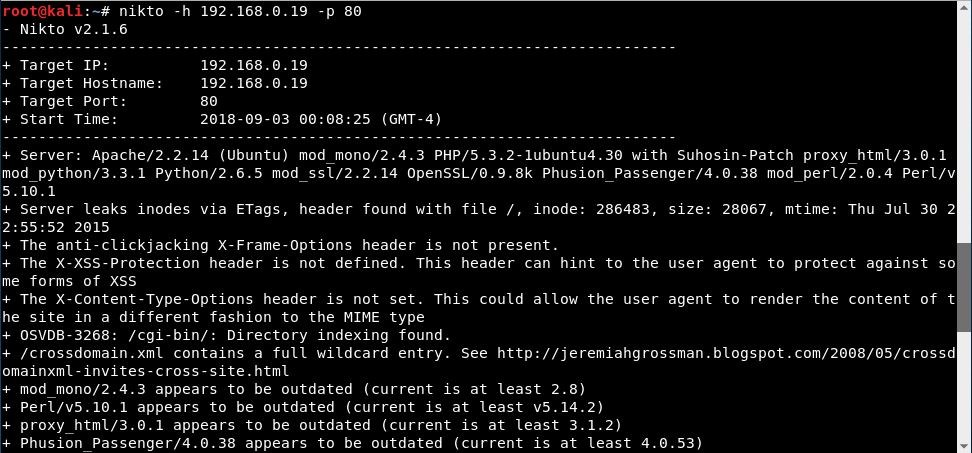
Reading through the snippet of results in the screen capture, in the first few lines, nikto tells us the IP address of the target and the hostname. After the basic target information, nikto displays the web server that's running and its version, Apache 2.2.14, on a Ubuntu system with some modules that were loaded, for example mod_perl/2.0.4 and OpenSSL/0.9.8k. Continuing down, we see some useful information, such as the path to the CGI folder (/cgi-bin/), and that some of the modules loaded are outdated:
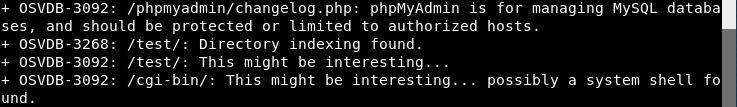
Further down in the results, nikto displays OSVDB codes. OSVDB is the abbreviation for Open Source Vulnerability Database. This was an initiative started by professionals in the security industry officially in 2004 and was a database that stored technical information on security vulnerabilities (a vast majority being web application-related). Unfortunately, the service shut down in April 2016 due to lack of support and contributions, however, the team over at http://cve.mitre.org have compiled a reference map that references the OSVDB to CVE entries (http://cve.mitre.org/data/refs/refmap/source-OSVDB.html).
This can be used to get more details on the OSVDB codes that nikto has provided:
Nikto has the functionality to identify web application vulnerabilities, such as information disclosure, injection (XSS/Script/HTML), remote file retrieval (server-wide), command execution, and software identification. In addition to the basic scanning demonstrated, Nikto allows the penetration tester to tailor scans to their particular target. The following are some of the options that can be utilized for scanning:
- Using the -T command-line switch with individual test numbers will tailor the testing to specific types
- By using –t, you can set the timeout value for each test response
- -D V controls the display output
- -o and -F define the scan report to be written in a particular format
- There are other advanced options, such as –mutate (to guess subdomains, files, directories, and usernames), -evasion (to bypass the IDS filter), and -Single (for single test mode), which you can use to assess your target in depth
