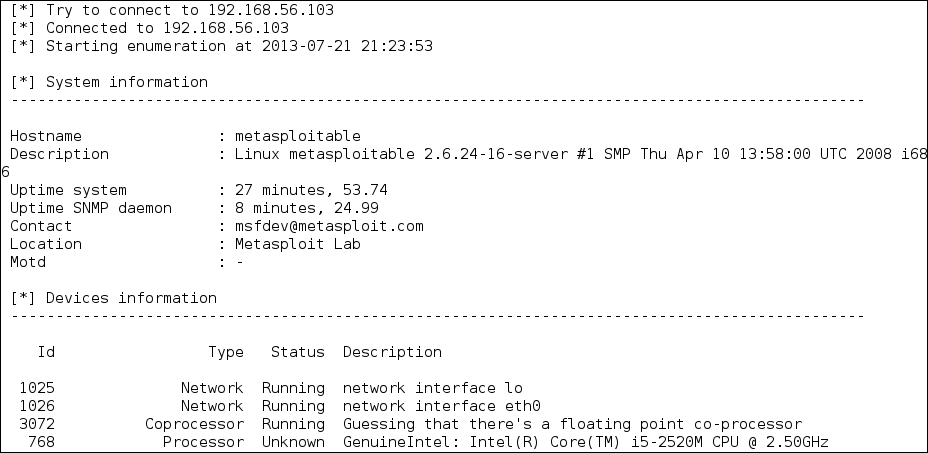
This section will cover the tools that can be used to check for the Simple Network Monitoring Protocol (SNMP). Even though the information from a SNMP device may not look important, as pen-testers, we have seen misconfigured SNMP devices, which allows us to read the configuration, get important information, and even have modify the configuration.
We suggest you also check the SNMP devices when you encounter a penetration testing job; you may be surprised with what you find.
The onesixtyone tool can be used as a SNMP scanner to find whether the SNMP string exists on a device. The difference with respect to other SNMP scanners is that this tool sends all the SNMP requests as fast as it can (10 milliseconds apart). Then it waits for the responses and logs them. If the device is available, it will send responses containing the SNMP string.
To access onesixtyone, go to the console and type onesixtyone.
By default, Metasploitable 2 does not have the SNMP daemon installed. To install it, just type the following command after you are connected to the Internet:
apt-get install snmpd
Then, you need to change the configuration file, /etc/default/snmpd:
sudo vi /etc/default/snmpd
In the SNMPDOPTIONS line, remove the localhost address (127.0.0.1) and restart SNMPD:
sudo /etc/init.d/snmpd restart
Beware that you need to isolate the Metasploitable 2 machine from the network connected outside. If not, you will get attacked easily.
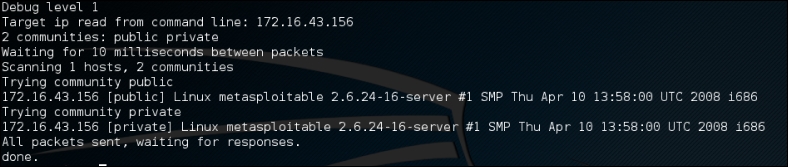
Let's try onesixtyone to find the SNMP strings used by a device located at 192.168.1.1. The following is the appropriate command:
onesixtyone 172.16.43.156
The following is the scanning result:
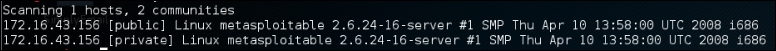
The SNMP strings found are public and private.
If we want the scanning to be more verbose, we can give the -d option:
onesixtyone -d 172.16.43.156
The result is as follows: