Import Hashing is another technique that can be used to identify related samples and the samples used by the same threat actor groups. Import hash (or imphash) is a technique in which hash values are calculated based on the library/imported function (API) names and their particular order within the executable. If the files were compiled from the same source and in the same manner, those files would tend to have the same imphash value. During your malware investigation, if you come across samples that have the same imphash values, it means that they have the same import address table and are probably related.
When you load an executable into pestudio, it calculates the imphash as shown here:
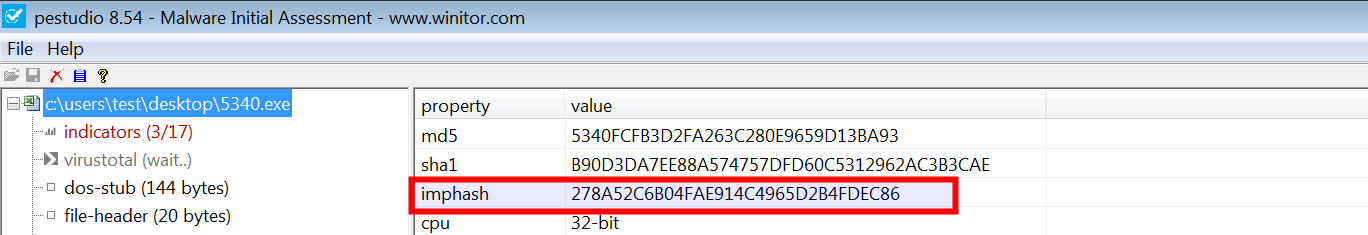
In Python, imphash can be generated using the pefile module. The following Python script takes the sample as input and calculates its imphash:
import pefile
import sys
pe = pefile.PE(sys.argv[1])
print pe.get_imphash()
The output as a result of running the preceding script against a malware sample is shown here:
$ python get_imphash.py 5340.exe
278a52c6b04fae914c4965d2b4fdec86
To demonstrate the use of import hashing, let's take the example of two samples from the same threat actor group. In the following output, the samples have different cryptographic hash values (MD5), but the impash of these samples are identical; this indicates that they were probably compiled from the same source and in the same manner:
$ md5sum *
3e69945e5865ccc861f69b24bc1166b6 maxe.exe
1f92ff8711716ca795fbd81c477e45f5 sent.exe
$ python get_imphash.py samples/maxe.exe
b722c33458882a1ab65a13e99efe357e
$ python get_imphash.py samples/sent.exe
b722c33458882a1ab65a13e99efe357e
