As you would expect, machine code contains information about the inner workings of the program. For example, in our program, the machine code included the instructions to print on the screen, but it would be painful for a human to try to understand the machine code (which is stored as a sequence of bytes).
A disassembler/debugger (like IDA Pro or x64dbg) is a program that translates machine code into a low-level code called assembly code (assembly language program), which can be read and analyzed to determine the workings of a program. The following screenshot shows the machine code (a sequence of bytes in the .text section) translated into the assembly instructions representing 13 executable instructions (push ebp, mov ebp,esp, and so on). These translated instructions are called assembly language instructions.
You can see that the assembly instructions are much easier to read than the machine code. Notice how a disassembler translated the byte 55 into a readable assembly instruction push ebp, and the next two bytes 8B EC into mov ebp,esp; and so on:
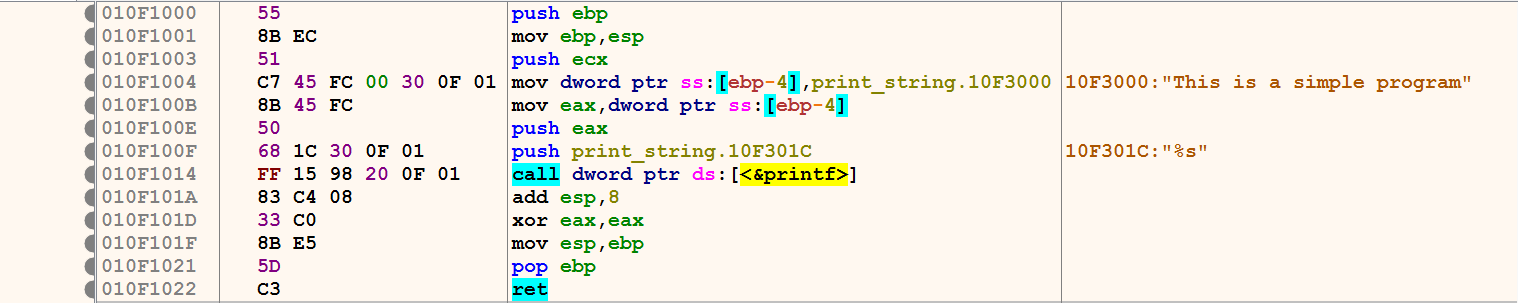
From a code analysis perspective, determining the program's functionality mainly relies on understanding these assembly instructions and how to interpret them.
In the rest of the chapter, you will learn the skills required to understand the assembly code to reverse engineer the malicious binary. In the upcoming sections, you will learn the concepts of x86 assembly language instructions that are essential to perform code analysis; x86, also known as IA-32 (32-bit), is the most popular architecture for PCs. Microsoft Windows runs on an x86 (32-bit) architecture and Intel 64 (x64) architectures. Most malware that you will encounter are compiled for x86 (32 bit) architectures and can run on both 32 bit and 64 bit Windows. At the end of the chapter, you will understand the x64 architecture and the differences between x86 and x64.
