The ldrmodules plugin compares module information from the three PEB lists (in the process memory) with the information from a data structure residing in the kernel memory known as VADs (Virtual Address Descriptors). The memory manager uses VADs to keep track of whichvirtual addresses in the process memory that are reserved (or free). The VAD is a binary tree structure that stores information about the virtually contiguous memory regions in the process memory. For each process, the memory manager maintains a set of VADs and each VAD node describes a virtually contiguous memory region. If the process memory region contains a memory-mapped file (such as an executable, DLL), then the VAD node stores information about its base address, file path, and memory protection. The following example should help you understand this concept. In the following screenshot, one of the VAD nodes in the kernel space is describing information about where the process executable (explorer.exe) is loaded, its full path, and memory protection. Similarly, other VAD nodes will describe process memory ranges, including the ones that contain mapped executable images such as DLLs:
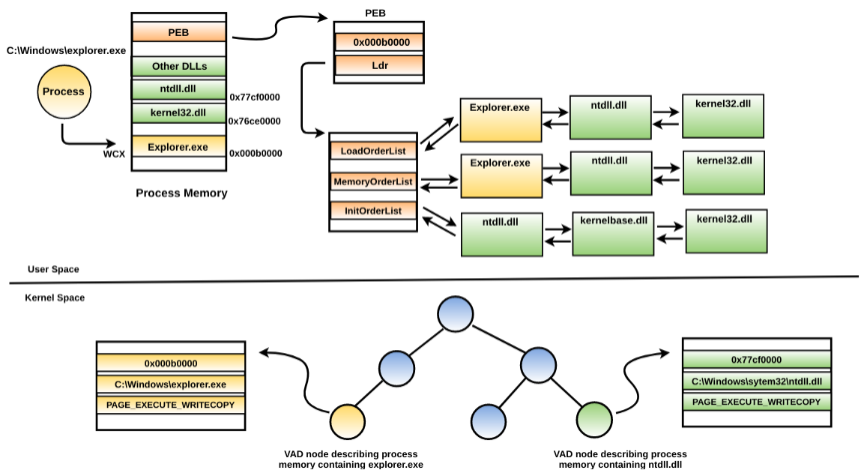
To get the module's information, the ldrmodules plugin enumerates all the VAD nodes that contain mapped executable images and compares the results with the three PEB lists to identify any discrepancies. The following is the module listing of a process from a memory image infected with the TDSS rootkit (which we saw earlier). You can see that the ldrmodules plugin was able to identify a malicious DLL called TDSSoiqh.dll, which hides from all the three PEB lists (InLoad, InInit, and InMem). The InInit value is set to False for svchost.exe, which is expected for an executable, as mentioned earlier:
$ python vol.py -f tdl3.vmem --profile=WinXPSP3x86 ldrmodules -p 880
Volatility Foundation Volatility Framework 2.6
Pid Process Base InLoad InInit InMem MappedPath
--- ----------- -------- ----- ------- ----- ----------------------------
880 svchost.exe 0x10000000 False False False \WINDOWS\system32\TDSSoiqh.dll
880 svchost.exe 0x01000000 True False True \WINDOWS\system32\svchost.exe
880 svchost.exe 0x76d30000 True True True \WINDOWS\system32\wmi.dll
880 svchost.exe 0x76f60000 True True True \WINDOWS\system32\wldap32.dll
[REMOVED]
