Process hollowing, or Hollow Process Injection, is a code injection technique in which the executable section of the legitimate process in the memory, is replaced with a malicious executable. This technique allows an attacker to disguise his malware as a legitimate process and execute malicious code. The advantage of this technique is that the path of the process being hollowed out will still point to the legitimate path, and, by executing within the context of a legitimate process, the malware can bypass firewalls and host intrusion prevention systems. For example, if the svchost.exe process is hollowed out, the path will still point to the legitimate executable path (C:\Windows\system32\svchost.exe), but, only in the memory, the executable section of svchost.exe is replaced with the malicious code; this allows an attacker to remain undetected from live forensic tools.
The following steps describe the hollow process injection performed by the malware sample (Skeeyah). In the following description, the malware process extracts the malicious executable to be injected from its resource section before performing these steps:
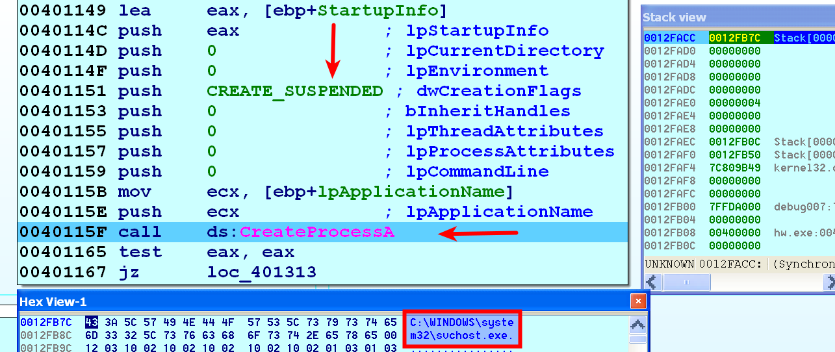
- The malware process starts a legitimate process in the suspended mode. As a result, the executable section of the legitimate process is loaded into the memory, and the process environment block (PEB) structure in the memory identifies the full path to the legitimate process. PEB's ImageBaseAddress (Peb.ImageBaseAddress) field contains the address where the legitimate process executable is loaded. In the following screenshot, the malware starts the legitimate svchost.exe process in suspended mode, and the svchost.exe, in this case, is loaded into the address 0x01000000:
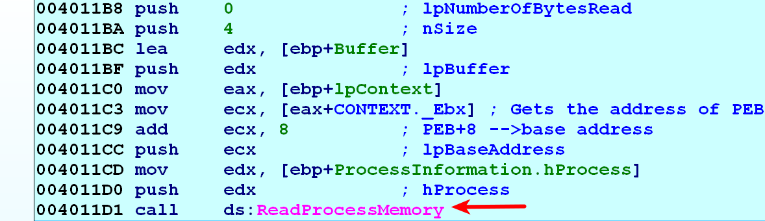
- The malware determines the address of the PEB structure so that it can read the PEB.ImageBaseAddress field to determine the base address of the process executable (svchost.exe). To determine the address of the PEB structure, it calls GetThreadContext(). The GetThreadContext() retrieves the context of a specified thread, and it takes two arguments: the 1st argument is the handle to the thread, and the 2nd argument is a pointer to the structure, named CONTEXT. In this case, the malware passes the handle to the suspended thread as the 1st argument to GetThreadContext(), and the pointer to the CONTEXT structure as the 2nd argument. After this API call, the CONTEXT structure is populated with the context of the suspended thread. This structure contains the register states of the suspended thread. The malware then reads the CONTEXT._Ebx field, which contains the pointer to the PEB data structure. Once the address of the PEB is determined, it then reads the PEB.ImageBaseAddress to determine the base address of the process executable (in other words, 0x01000000):
Another method to determine the pointer to PEB is using the NtQueryInformationProcess() function; details are available at https://msdn.microsoft.com/en-us/library/windows/desktop/ms684280(v=vs.85).aspx.
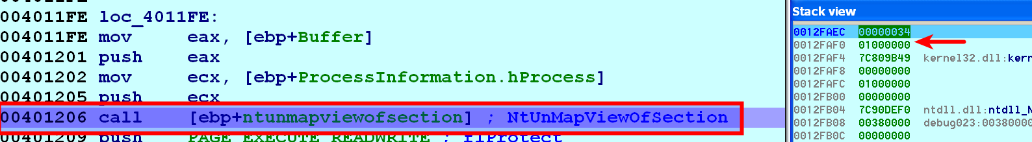
- Once the address of the target process executable in memory is determined, it then deallocates the executable section of the legitimate process (svchost.exe) using the NtUnMapViewofSection() API. In the following screenshot, the 1st argument is the handle (0x34) to the svchost.exe process, and the 2nd argument is the base address of the process executable (0x01000000) to deallocate:
- After the process executable section is hollowed out, it allocates a new memory segment in the legitimate process (svchost.exe), with read, write, and execute permission. The new memory segment can be allocated in the same address (where the process executable resided before hollowing) or in a different region. In the following screenshot, the malware uses VirutalAllocEX() to allocate memory in a different region (in this case, at 0x00400000):
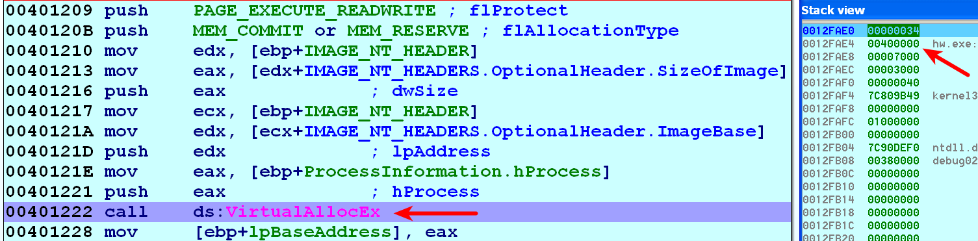
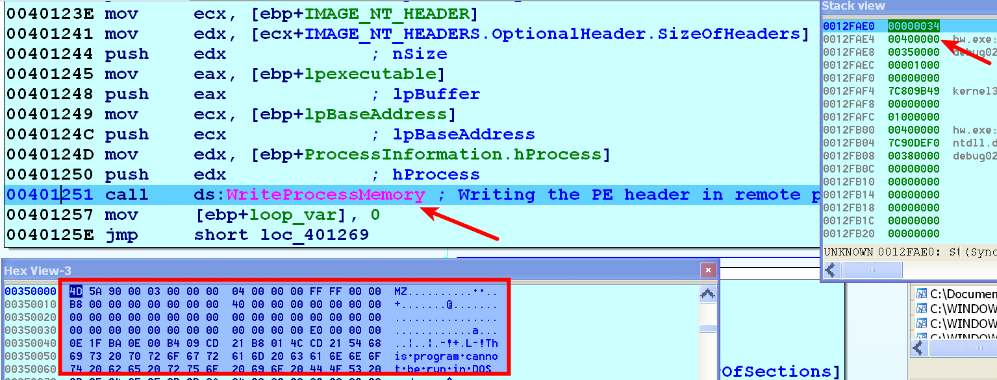
- It then copies the malicious executable and its sections, using WriteProcessMemory(), into the newly allocated memory address at 0x00400000:
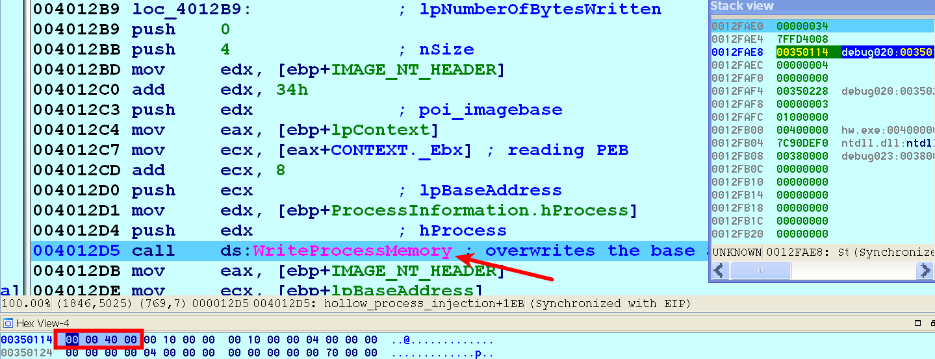
- The malware then overwrites the PEB.ImageBaseAdress of the legitimate process with the newly allocated address. The following screenshot shows the malware overwriting the PEB.ImageBaseAdress of svchost.exe with the new address (0x00400000); this changes the base address of svchost.exe in PEB from 0x1000000 to 0x00400000 (this address now contains the injected executable):
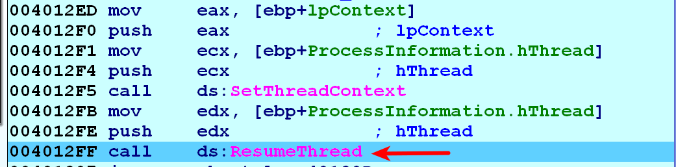
- The malware then changes the start address of the suspended thread to point to the address of entry point of the injected executable. This is done by setting the CONTEXT._Eax value and calling SetThreadContext(). At this point, the thread of the suspended process points to the injected code. It then resumes the suspended thread using ResumeThread(). After this, the resumed thread starts executing the injected code: