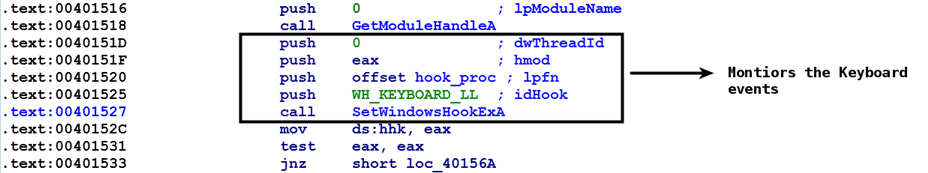
Another common keylogger technique is where it installs a function (called hook procedure) to monitor keyboard events (such as key press). In this method, the malicious program registers a function (hook procedure) that will be notified when a keyboard event is triggered, and that function can log the keystrokes to a file or send them over the network. The malicious program uses the SetWindowsHookEx() API to specify what type of event to monitor (such as the keyboard, mouse, and so on) and the hook procedure that should be notified when a specific type of event occurs. The hook procedure can be contained within a DLL or the current module. In the following screenshot, the malware sample registers a hook procedure for the low-level keyboard event by calling SetWindowsHookEx() with the WH_KEYBOARD_LL parameter (malware may also use WH_KEYBOARD). The second parameter, offset hook_proc, is the address of the hook procedure. When the keyboard event occurs, this function will be notified. Examining this function will give an idea of how and where the keylogger logs keystrokes. The third parameter is the handle to the module (such as DLL or the current module) that contains the hook procedure. The fourth parameter, 0, specifies that the hook procedure is to be associated with all existing threads in the same desktop: