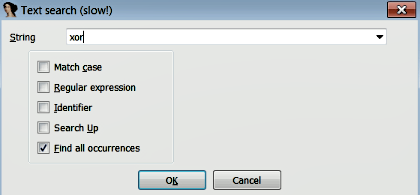
To identify XOR encoding, load the binary in IDA and search for the XOR instruction by selecting Search | text. In the dialog that appears, enter xor and select Find all occurrences as shown here:
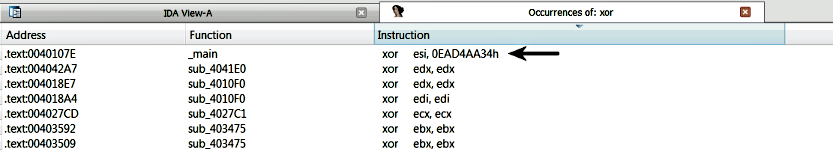
When you click on OK, you will be presented with all the occurrences of XOR. It is very common to see the XOR operation where the operands are the same registers, such as xor eax,eax or xor ebx,ebx. These instructions are used by the compiler to zero out register values, and you can ignore these instructions. To identify XOR encoding, look for (a) XOR of a register (or memory reference) with a constant value such as the one shown here, or (b) look for XOR of a register (or memory reference) with a different register (or memory reference). You can navigate to the code by double-clicking on the entry:
The following are some of the tools you can use to determine the XOR key. In addition to using XOR encoding, attackers may also use ROL, ROT or SHIFT operations to encode data. XORSearch and Balbuzard mentioned here also support ROL, ROT, and Shift operations in addition to XOR. CyberChef supports almost all types of encoding, encryption, and compression algorithms:
- CyberChef: https://gchq.github.io/CyberChef/
- XORSearch by Didier Stevens: https://blog.didierstevens.com/programs/xorsearch/
- Balbuzard: https://bitbucket.org/decalage/balbuzard/wiki/Home
- unXOR: https://github.com/tomchop/unxor/#unxor
- brxor.py: https://github.com/REMnux/distro/blob/v6/brxor.py
- NoMoreXOR.py: https://github.com/hiddenillusion/NoMoreXOR
