How Email Works
You might already have a strong working knowledge of how email works. If you don’t, this section provides a common base of knowledge, which allows you to get the most from this chapter.
Different types of devices and methods generate emails. Most commonly, a user composes a message on his or her computer and then sends it to his or her mail server (though more and more commonly, the computer is a tablet or smartphone). At this point, the user’s computer is finished with the job, but the mail server still has to deliver the message. A mail server is like an electronic post office: It sends and receives electronic mail. Most of the time, the mail server is separate from the computer where the mail was composed.
The sender’s mail server forwards the message through the organization’s network and/or the Internet to the recipient’s mail server. The message then resides on that second mail server and is available to the recipient.
The software program used to compose and read email messages is the email client. Depending on how the recipient’s email client is configured, copies of the message may exist in a number of places. The recipient’s and sender’s computers, another electronic device such as a smartphone or a tablet, and the mail server or servers and their backups may all hold copies of the message. In addition, any of the servers that relay the message from the sender to the recipient may retain a copy of the email message. This is shown in FIGURE 7-1.
The number of relay “hops” may be only one if the sender and recipient are on the same network. Transmitting a message to a remotely located recipient might require many hops.
A forensic investigation of email might reveal information such as the following:
Email messages related to the investigation
Email addresses related to the investigation
Sender and recipient information
Information about those copied on the email
Content of the communications
Internet Protocol (IP) addresses
Date and time information
User information
Attachments
Passwords
Application logs that show evidence of spoofing
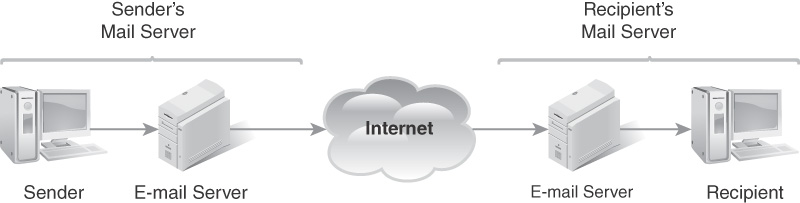
FIGURE 7-1
Delivering email.
It is also important to keep in mind that the content of email can be very important even in non–computer crime cases. Given how common email communications are, it should not surprise you to find that criminals often communicate via email. Some crimes, like cyberstalking, usually include an email element. Other crimes, such as drug trafficking and terrorism, can also utilize email communication.
In financial crimes, such as insider trading, as well as in discrimination lawsuits, email is often a critical piece of evidence. Keep in mind that the sender and perhaps even the recipient may have deleted the email, but it could still reside on an email server or in the backup media for that server.
