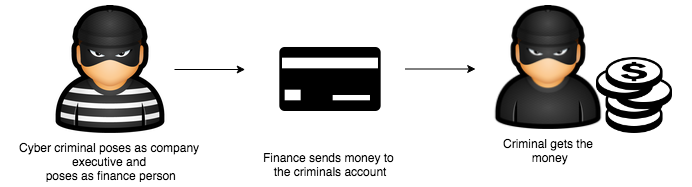
According to a recent report, at least 75 percent of companies are the target of impersonation attempts each year. There are several variations of impersonation; the most popular ones are the following:
- Executive impersonation: These are cases where the impersonator either takes over an executive account, such as a CEO or CFO of the company. The impersonator may also try to spook emails from the executive by putting minute variations in the email IDs, such as janedoe@xyz.com being changed to jandoe@xyz.com. The content of these emails will deal with sensitive issues needing immediate action, such as a wire transfer that needs to be mailed urgently. Employees usually ignore the falsification of the email ID and carry out the activity.
- Vendor impersonation: This is another type of fraud, where the impersonator spooks email IDs of legitimate vendors and sends out emails about changes in payment information. The emails will have a new banking address where future emails need to be sent.
- Customer impersonation: Some impersonators spoof the customer's account just to collect confidential or valuable information that can be used in future fraud.
- Identity theft: This is a popular form of impersonation, done at times for financial advantage, and sometimes to facilitate a criminal activity, such as for identity cloning and medical identity theft. Identity theft helps in facilitating other crimes such as immigration fraud, attacking payment systems for terrorism, phishing, and espionage.
- Industrial espionage: Industrial espionage is known to happen in industrial companies, software and automobiles, where planned acts of sabotage are carried out by competitors or by the government to gather information and competitive intelligence. Industrial espionage is facilitated by impersonators gathering information from dissatisfied employees, via the use of malware, or by performing a distributed denial of service: