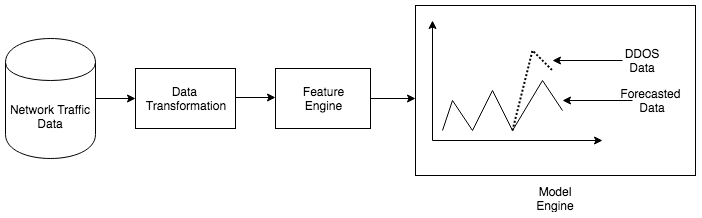
The use case undergoes the following stages:
- We start with importing our data in a pandas data frame
- We determine that the data is properly cleansed
- We analyze the data, as per the model requirement
- We extract features from the data and analyze the features again to measure the correlation, variance, and seasonality
- We will then fit a time series model to predict whether the current data is a part of a DDoS attack or not
The following diagram sums up the entire procedure: