Ensure Burp and the OWASP BWA VM are running and that Burp is configured in the Firefox browser used to view OWASP BWA applications.
- From the OWASP BWA Landing page, click the link to the OWASP Mutillidae II application.
- Open the Firefox browser to access the home page of OWASP Mutillidae II (URL: http://<your_VM_assigned_IP_address>/mutillidae/). Make sure you are starting a fresh session of the Mutillidae application and not logged into it already:
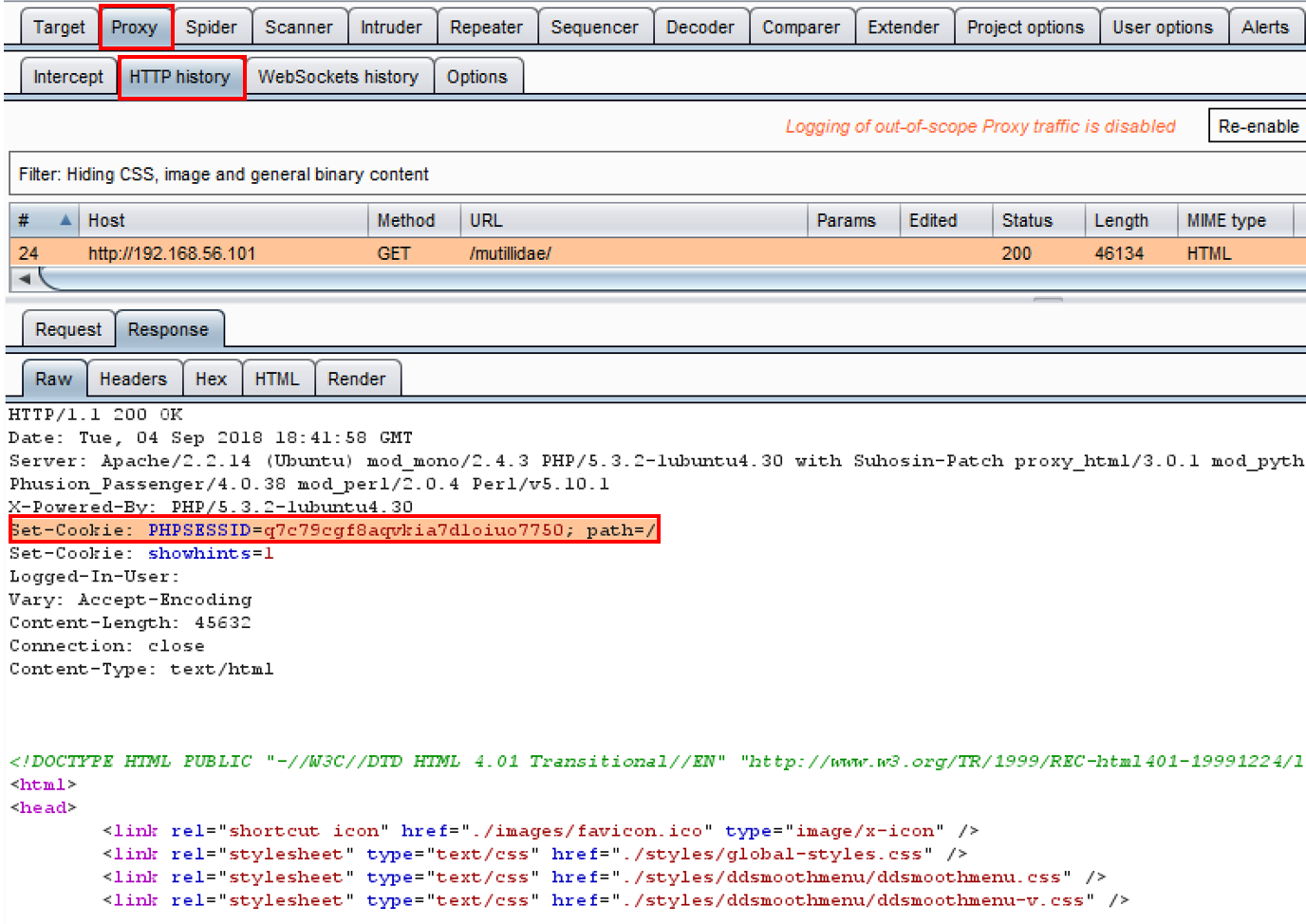
- Switch to the Proxy | HTTP History tab and select the request showing your initial browse to the Mutillidae home page.
- Look for the GET request and the associated response containing the Set-Cookie: assignments. Whenever you see this assignment, you can ensure you are getting a freshly created cookie for your session. Specifically, we are interested in the PHPSESSID cookie value:
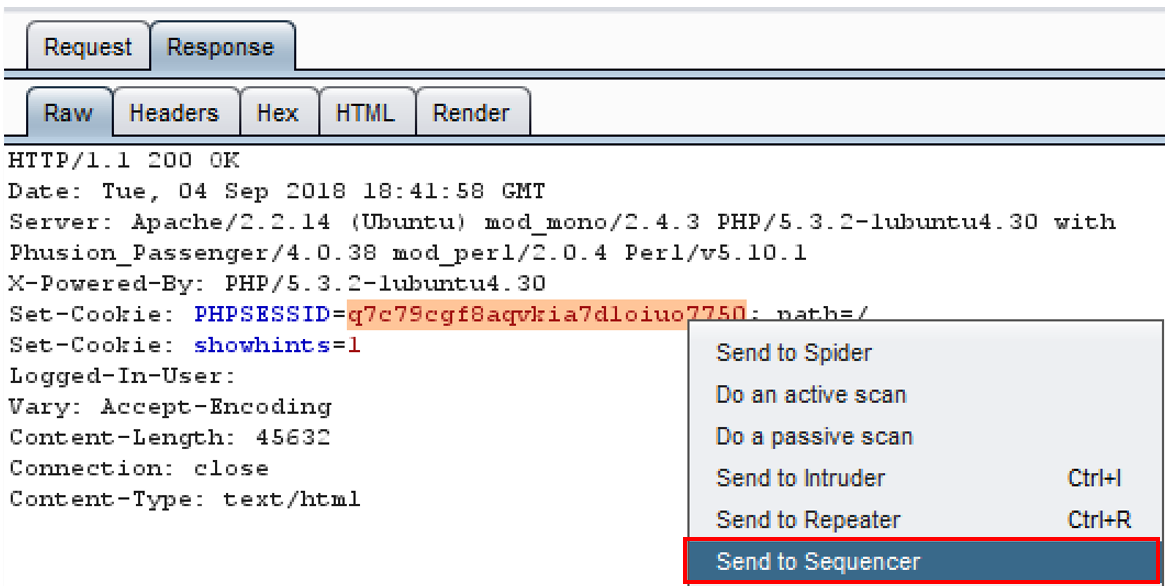
- Highlight the value of the of the PHPSESSID cookie, right-click, and select Send to Sequencer:
Sequencer is a tool within Burp designed to determine the strength or the quality of the randomness created within a session token.
- After sending the value of the PHPSESSID parameter over to Sequencer, you will see the value loaded in the Select Live Capture Request table.
- Before pressing the Start live capture button, scroll down to the Token Location Within Response section. In the Cookie dropdown list, select PHPSESSID=<captured session token value>:
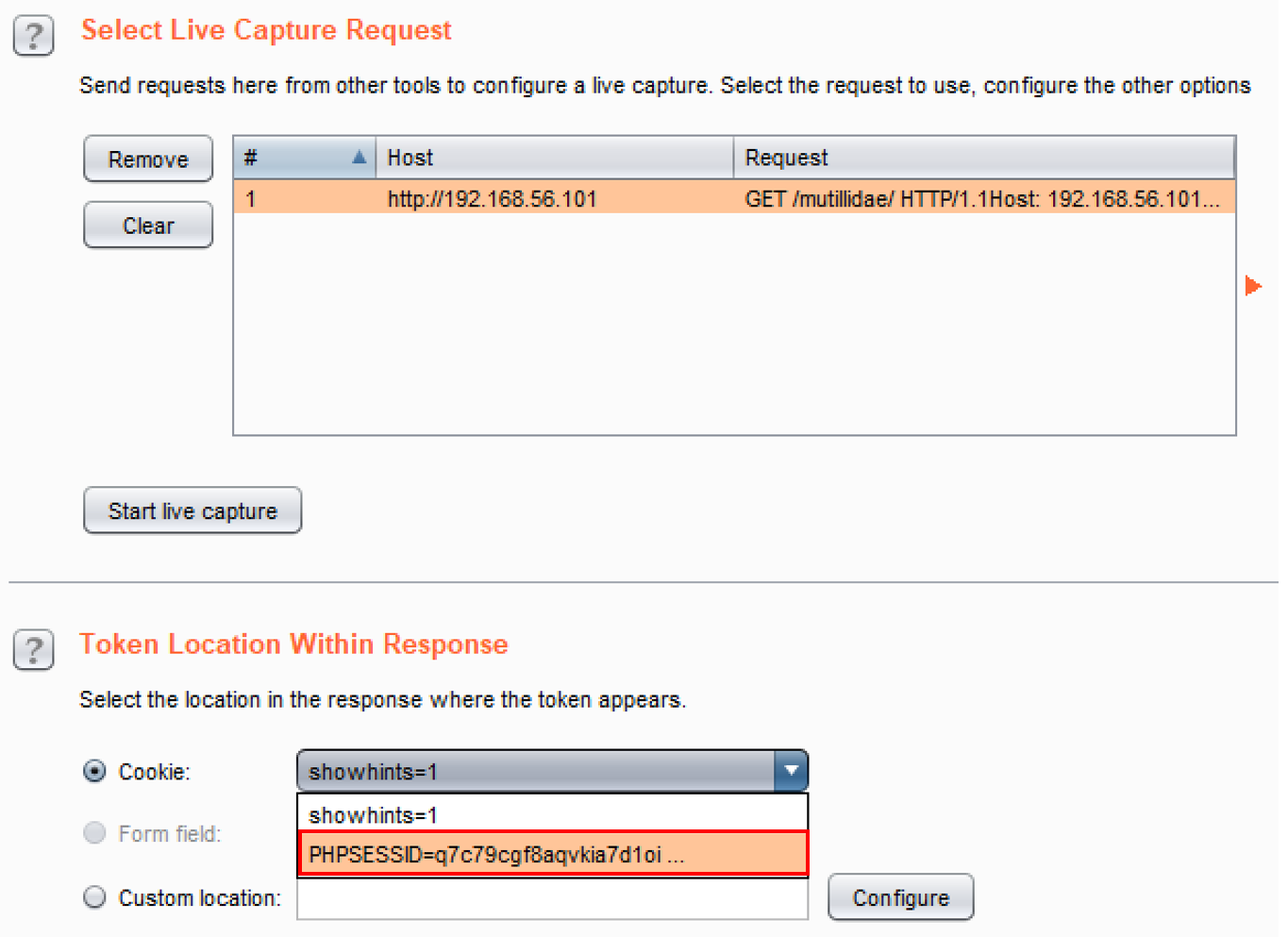
- Since we have the correct cookie value selected, we can begin the live capture process. Click the Start live capture button, and Burp will send multiple requests, extracting the PHPSESSID cookie out of each response. After each capture, Sequencer performs a statistical analysis of the level of randomness in each token.
- Allow the capture to gather and analyze at least 200 tokens, but feel free to let it run longer if you like:
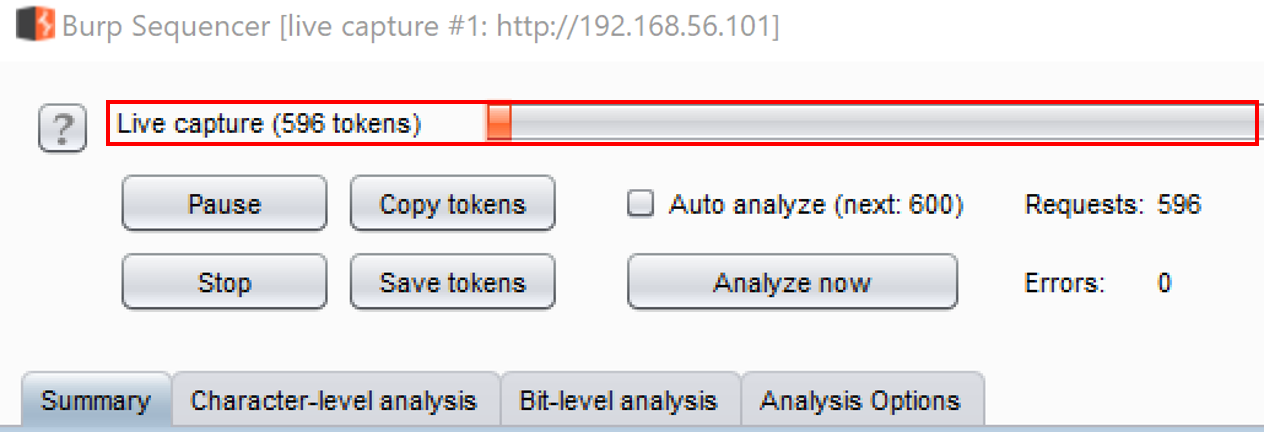
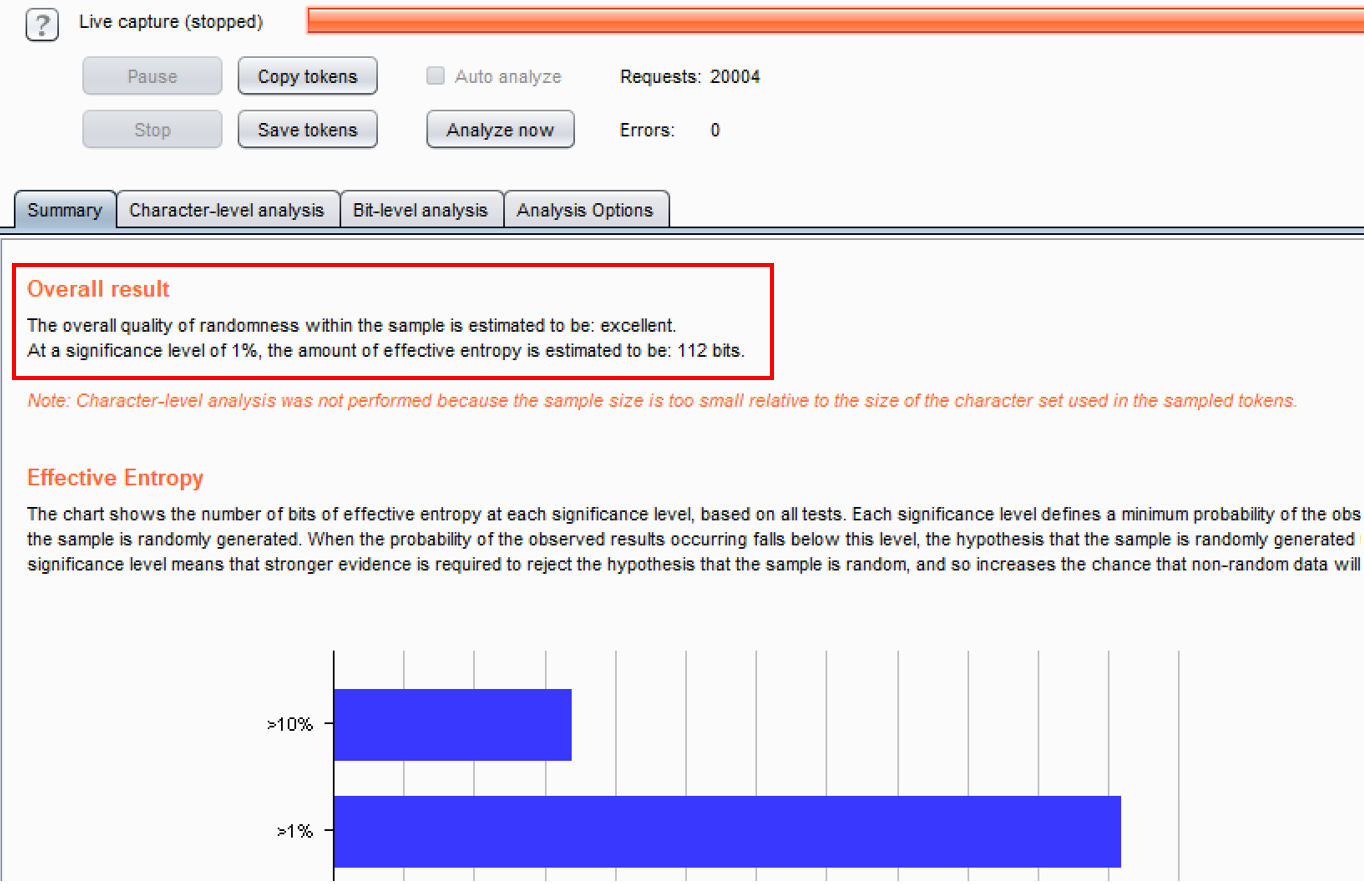
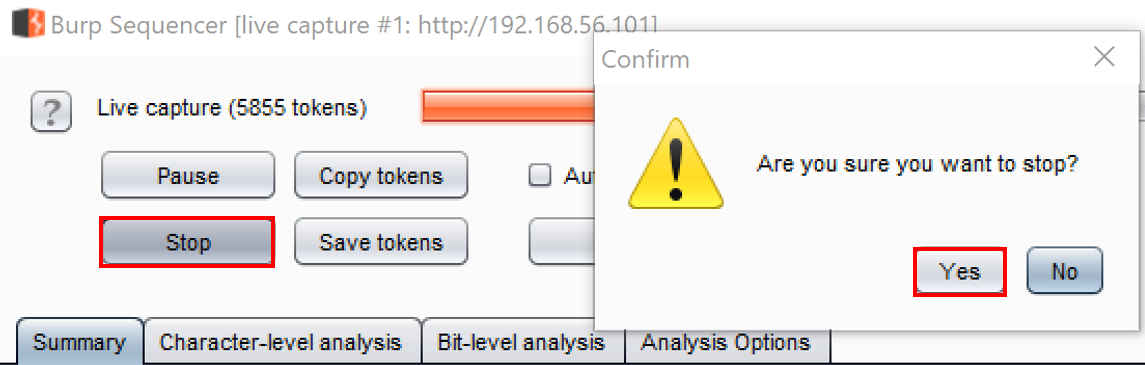
- Once you have at least 200 samples, click the Analyze now button. Whenever you are ready to stop the capturing process, press the Stop button and confirm Yes:
- After the analysis is complete, the output of Sequencer provides an overall result. In this case, the quality of randomness for the PHPSESSID session token is excellent. The amount of effective entropy is estimated to be 112 bits. From a web pentester perspective, these session tokens are very strong, so there is no vulnerability to report here. However, though there is no vulnerability present, it is good practice to perform such checks on session tokens: