Burp Scanner is a tool that automates the search for weaknesses within the runtime version of an application. Scanner attempts to find security vulnerabilities based on the behavior of the application.
Scanner will identify indicators that may lead to the identification of a security vulnerability. Burp Scanner is extremely reliable, however, it is the responsibility of the pentester to validate any findings prior to reporting.
There are two scanning modes available in Burp Scanner:
- Passive scanner: Analyzes traffic passing through the proxy listener. This is why its so important to properly configure your target scope so that you aren't scanning more than is necessary.
- Active scanner: Sends numerous requests that are tweaked from their original form. These request modifications are designed to trigger behavior that may indicate the presence of vulnerabilities (https://portswigger.net/kb/issues). Active scanner is focused on input-based bugs that may be present on the client and server side of the application.
Scanning tasks should occur after spidering is complete. Previously, we learned how Spider continues to crawl as new content is discovered. Similarly, passive scanning continues to identify vulnerabilities as the application is crawled.
Under the Options tab, a tester has the following options: Issue activity, Scan queue, Live scanning, Issue definitions, and Options:
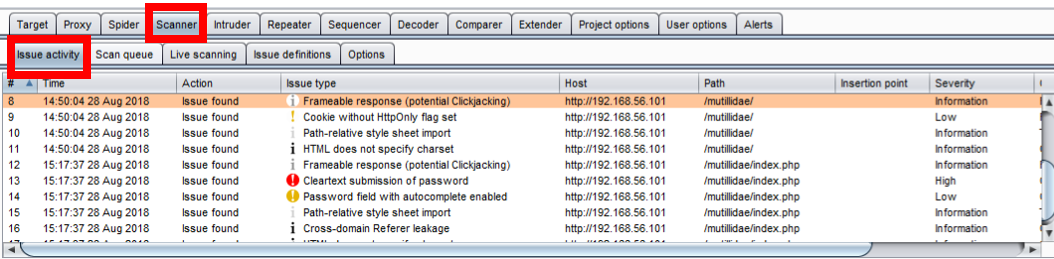
- Issue Activity: It displays all scanner findings in a tabular format; includes both passive and active scanner issues.:
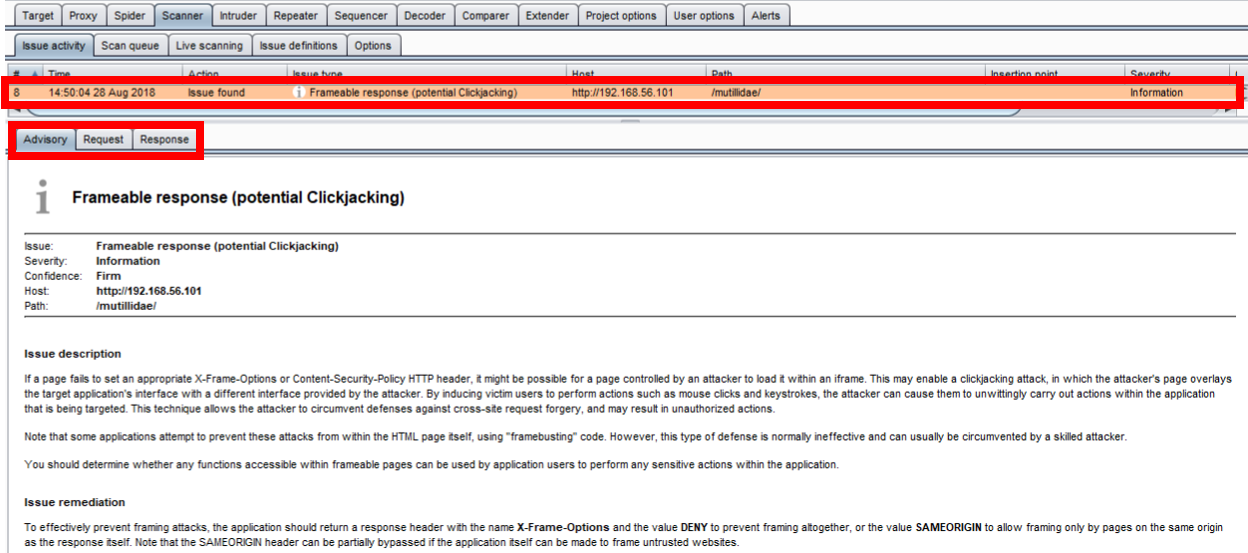
By selecting an issue in the table, the message details are displayed, including an advisory specific to the finding as well as message-editor details related to the request and response:
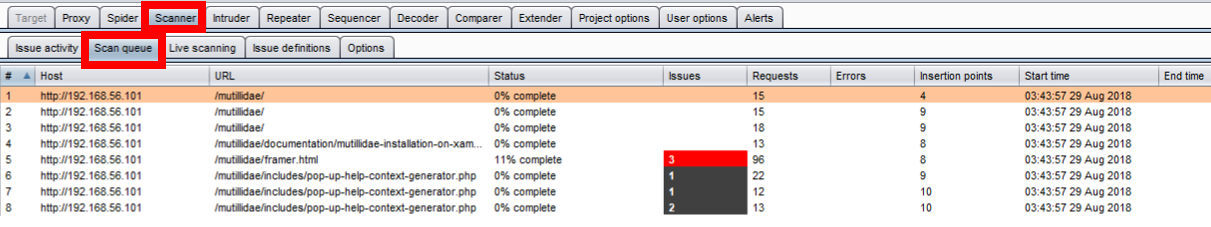
- Scan queue: Displays the status of active scanner running; provides a percentage of completion per number of threads running as well as number of requests sent, insertion points tested, start time, end time, targeted host, and URL attacked.
Scanner can be paused from the table by right-clicking and selecting Pause scanner; likewise, scanner can be resumed by right-clicking and selecting Resume Scanner. Items waiting in the scan queue can be cancelled as well:
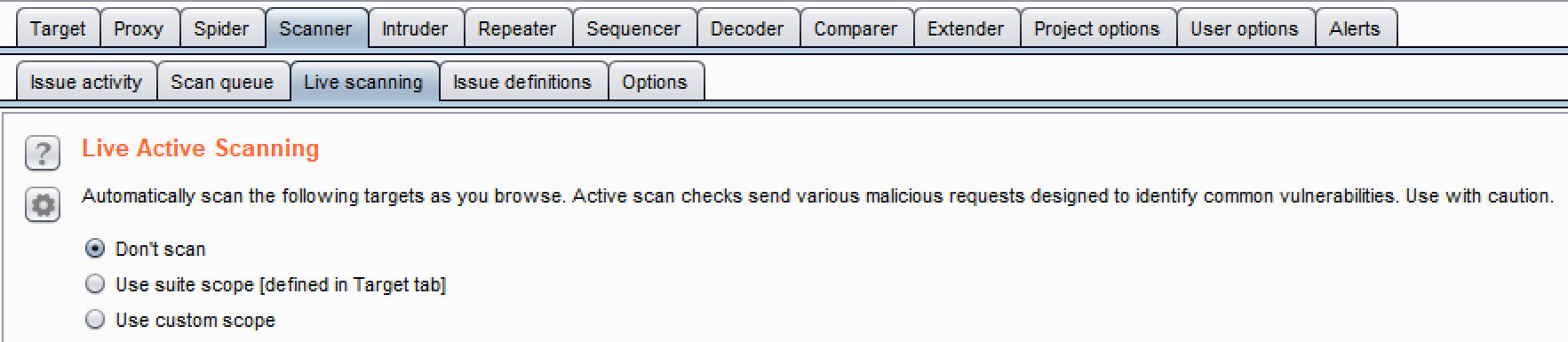
- Live Active Scanning: It allows customization when active scanner will perform scanning activities:
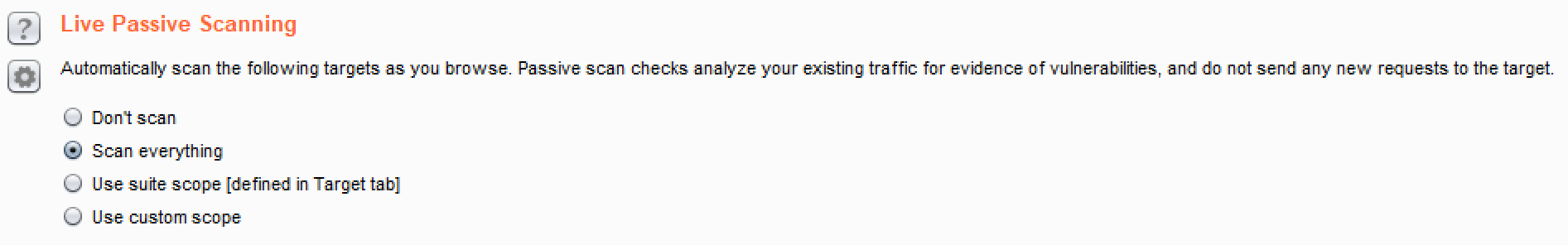
- Live Passive Scanning: It allows customization when passive scanner will perform scanning activities. By default, passive scanner is always on and scanning everything:
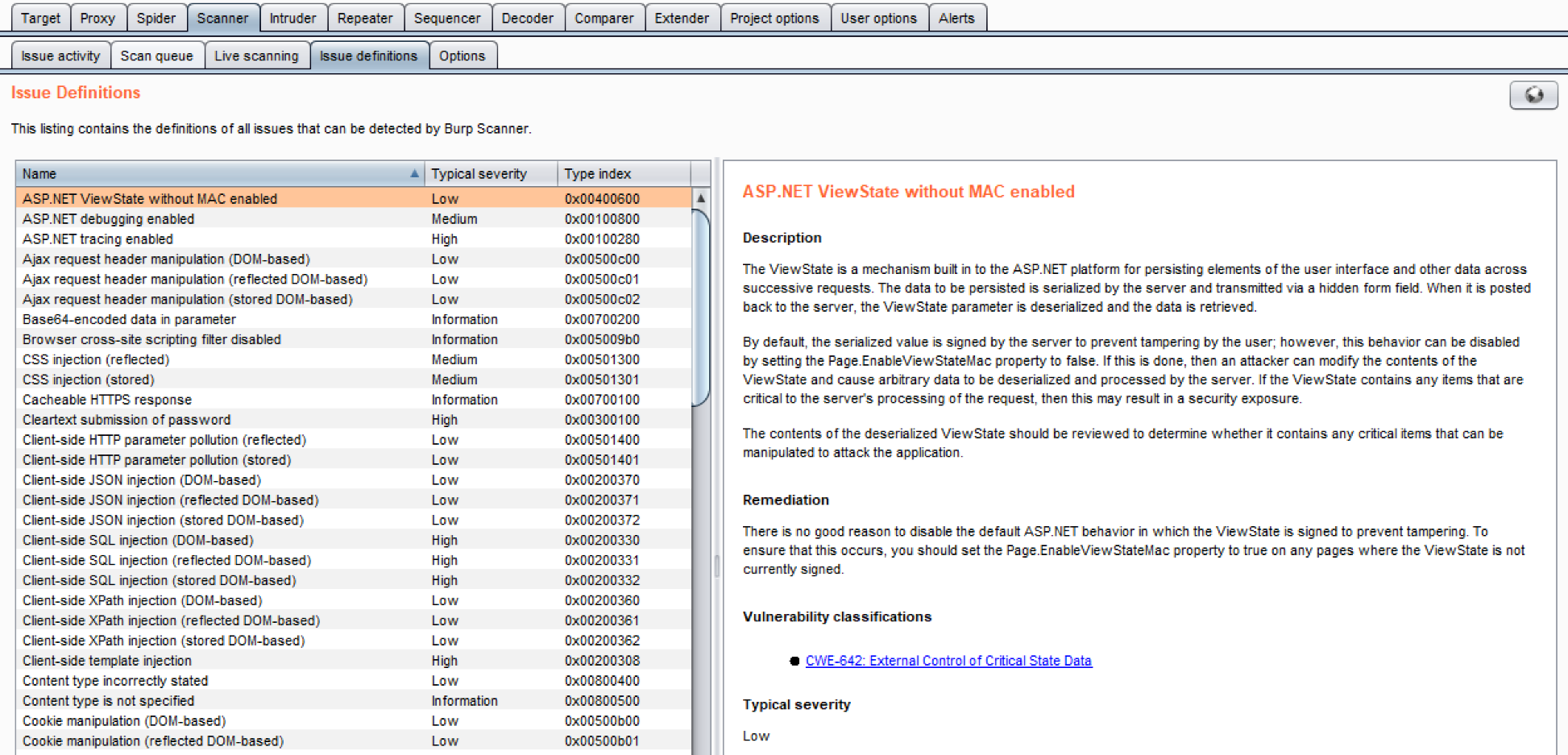
- Issue definitions: It displays definitions for all vulnerabilities known to Burp scanners (active and passive). The list can be expanded through extenders but, using Burp core, this is the exhaustive listing, which includes title, description text, remediation verbiage, references, and severity level:
- Options: Several sections are available, including Attack Insertion Points, Active Scanning Engine, Attack Scanning Optimization, and Static code analysis.
- Attack Insertion Points: It allows customization for Burp insertion points; an insertion point is a placeholder for payloads within different locations of a request. This is similar to the Intruder payload marker concept discussed in Chapter 2, Getting to Know the Burp Suite of Tools:
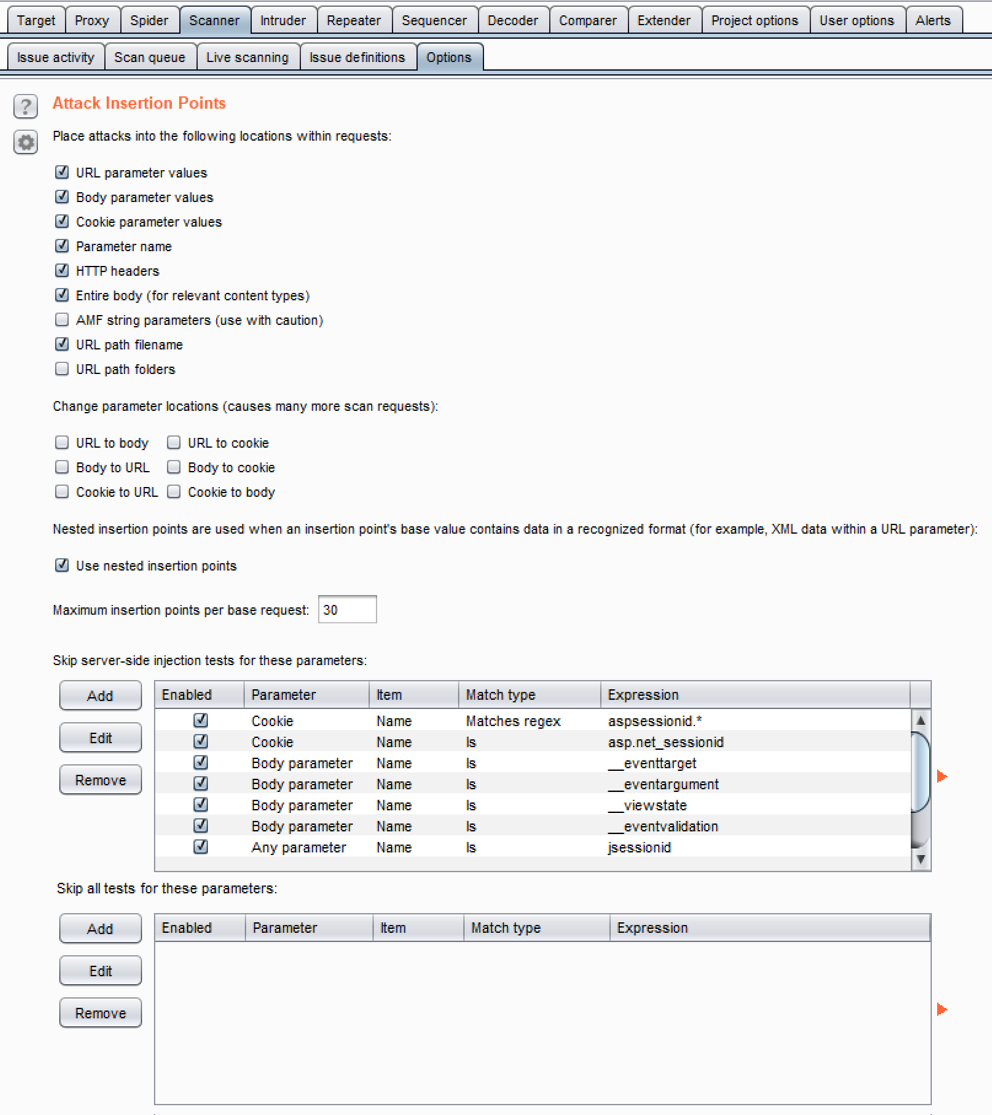
Recommendations here include adding the URL-to-body, Body-to-URL, cookie-to-URL, URL-to-cookie, body-to-cookie, and cookie-to-body insertion points when performing an assessment. This allows Burp to fuzz almost, if not all, available parameters in any given request.
-
- Active Scanning Engine: It provides the ability to configure the number of threads (for example, Concurrent request limit) scanner will run against the target application. This thread count, compounded with the permutations of insertion points, can create noise on the network and a possible DOS attack, depending upon the stability of the target application. Use caution and consider lowering the Concurrent request limit. The throttling of threads is available at this configuration section as well:
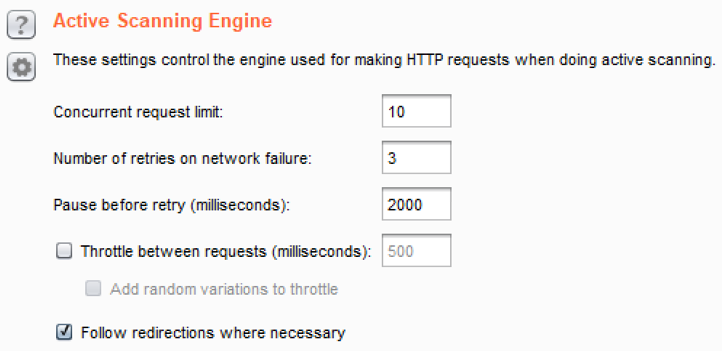
-
- Attack Scanning Optimization: It provides three settings for scan speed and scan accuracy.
- Available Scan speed settings include Normal, Fast, and Thorough. Fast makes fewer requests and checks derivations of issues. Thorough makes more requests and checks for derivations of issues. Normal is the medium setting between the other two choices. The recommendation for Scan speed is Thorough.
- Available Scan accuracy settings include Normal, Minimize false negatives, and Minimize false positives. Scan accuracy relates to the amount of evidence scanner requires before reporting an issue. The recommendation for Scan accuracy is Normal:
- Attack Scanning Optimization: It provides three settings for scan speed and scan accuracy.
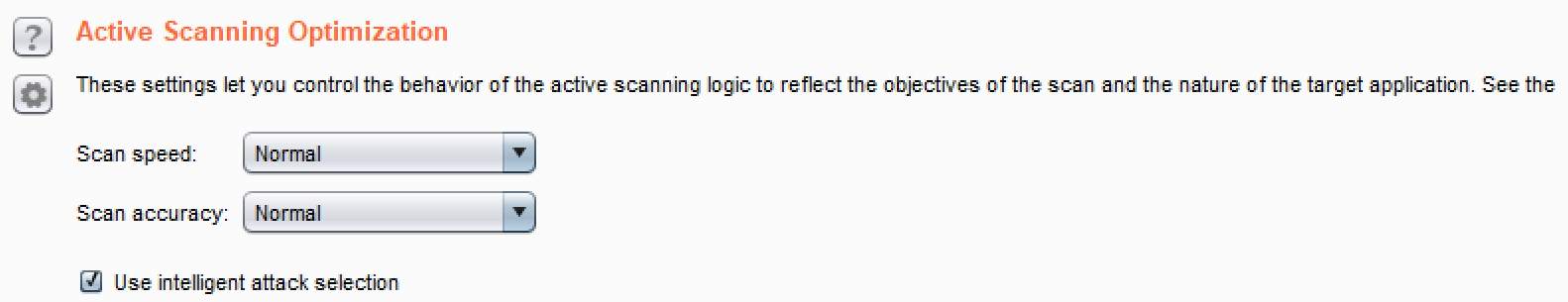
-
- Static Code Analysis: It provides the ability to perform static analysis of binary code. By default, this check is performed in active scanner:
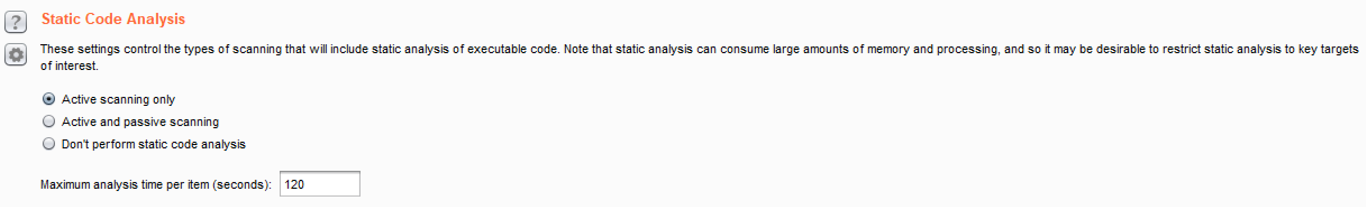
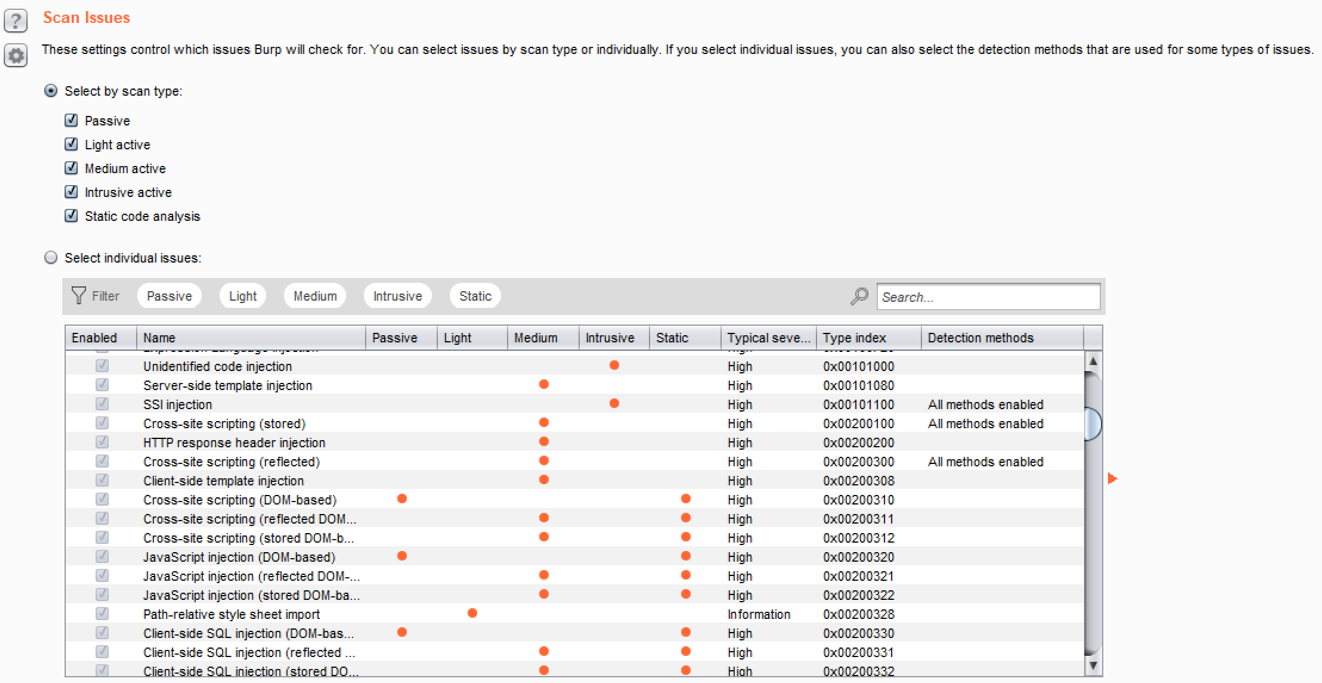
- Scan Issues: It provides the ability to set which vulnerabilities are tested and for which scanner (that is, passive or active). By default, all vulnerability checks are enabled: