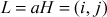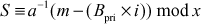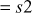Chapter 9
Elliptic Curve Cryptography
9.1 Introduction
In 1985, Victor Miller (IBM) and Neil Koblitz (University of Washington) invented elliptic curve cryptography (ECC), which comes under public-key cryptosystem. At the time of its invention, the ECC algorithm provided higher potential security than other cryptographic algorithms. However, the ECC also had a limitation that it required an enormous amount of execution time. In order to improve its performance, Certicom [1] focused and provided efforts on its implementation part. Later on several years of research, the first commercial toolkit was introduced by Certicom to enhance ECC and created it for practical use in a variety of applications. The ECC is a public-key cryptosystem which is basically derived from the algebraic construction of elliptic curves over finite domains. The ECC has many advantages compared to other cryptographic schemes such as RSA, Elgamal and Diffie–Hellman key exchange, etc. One of the major advantages is that it can provide the same degree of protection offered by other cryptography schemes with keys of smaller size. For example, the 160-bit key used in the ECC provides the same level of security as by the RSA with 1024-bit key. Likewise, the ECC with 224-bit key provides the same degree of protection provided by the RSA with 2048-bit key. Because, a small size key is used for proving high-level security in the ECC, it also takes less computation time for performing encryption and decryption operation. Moreover, it would minimize the storage complexity of processing with smaller size key values.
Similar to other public-key cryptosystem such as RSA and Elgamal, in ECC, each user selects a private key within a finite group from which a public key is computed. For computing the public key from private key, each user selects a base point, which is taken from the elliptic curve. The base point is a point in the curve which is similar to the generator used in other public-key cryptosystems such as Diffie–Hellman key exchange and Elgamal. When this base point is added with the private key, it is necessary to perform point addition and when it is multiplied with the private key it would perform point multiplication. Apart from that, in ECC-based algorithms, it is infeasible to recover the discrete logarithm of a random elliptic curve element from a publicly known base point. This problem is predicted as the ‘elliptic curve discrete log problem’ or ECDLP. The total security of ECC depends on the inability to find the multiplicand value from the given original and product points in a point multiplication.
9.2 ECC Arithmetic
The elliptic curves are described by cubic equations. An elliptic curve is a plane curve and it is defined by the equation as given below:
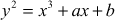
where a, b are the elliptic curve coefficients and x and y are the values of real numbers. The main characteristics of elliptic curve are summarized as follows:
- Elliptic curves obey the abelian group property.
• Abelian groups: An abelian group is a set, denoted by A, together with an operation denoted by •, any two elements a, b in the set A form another element denoted a • b. The symbol • corresponds to the binary operation. The set and operation, (A, •), require to satisfy the abelian group axioms:
– (A1) Closure: If a, b is in A, then the result of a • b is also in A.
– (A2) Associativity: The equation (a • b) • c = a • (b • c) holds for all a, b, c
 A
A– (A3) Identity element: For all elements a in A, there exists an element e in A, such that e • a = a • e = a.
– (A4) Inverse element: For each a in A, there exists an inverse element a′ in A such that a • a′ = a′ • a = e, where e is the identity element.
– (A5) Commutativity: a • b = b • a, for all a, b
 A.
A. - The point at infinity
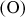 is acting as the identity element.
is acting as the identity element. - Each elliptic curve is symmetric about
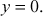
9.2.1 Elliptic Curve Operations
The main operations involved in the ECC are point addition and point multiplication. In point addition, the two adding points that lie on an elliptic curve result in a third point on the curve. From this definition, the point addition defines some rules for addition over an elliptic curve.
9.2.2 Geometric Description of Addition
A group can be described based on the set 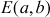 for exact values of a and b in the equation
for exact values of a and b in the equation 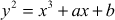 , which makes the following condition is satisfied:
, which makes the following condition is satisfied:
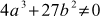
To describe the group, an addition operation must be defined which is denoted as +. The above equation is satisfied for the values of a and b for the set 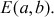 In geometric terms, the following rules are defined for addition over an elliptic curve.
In geometric terms, the following rules are defined for addition over an elliptic curve.
- The infinite point (O) can serve as the additive identity. Therefore,
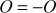 .
.
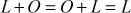 (Existence of an identity element)
(Existence of an identity element)where L is the point on the elliptic curve.
- If
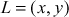 on the elliptic curve, then the negative of the point is represented as
on the elliptic curve, then the negative of the point is represented as 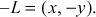 If these two points are connected by a vertical line, then
If these two points are connected by a vertical line, then
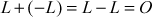 (Existence of inverses)
(Existence of inverses) 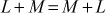 (Commutativity)
(Commutativity)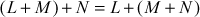 (Associativity)
(Associativity)- Point addition: If J and K are the two points with different coordinates on the elliptic curve, then the point addition between the two points can be performed by drawing a straight line between them which touches the third point R on the same elliptic curve. The reflection of R along the x-axis provides the result of
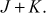 The point addition is illustrated in Figure 9.1.
The point addition is illustrated in Figure 9.1.
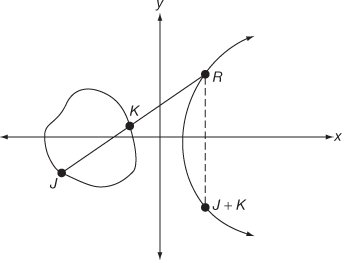
Figure 9.1 Illustration of point addition
- Point doubling: In point doubling, a tangent line is drawn to get the other point of intersection
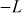 in the same elliptic curve. Point doubling is illustrated in Figure 9.2. Then
in the same elliptic curve. Point doubling is illustrated in Figure 9.2. Then 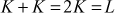
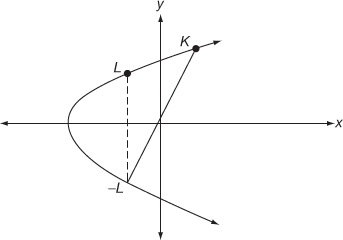
Figure 9.2 Illustration of point doubling
9.2.3 Arithmetic Description of Point Addition
Let us consider two distinct points 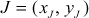 and
and 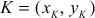 on the elliptic curve. The straight line
on the elliptic curve. The straight line 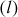 between them touches the third point
between them touches the third point 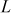 on the same elliptic curve. The reflection of
on the same elliptic curve. The reflection of 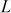 denoted as
denoted as 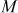 along the x-axis provides the result of
along the x-axis provides the result of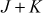 . The slope of the line
. The slope of the line 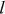 can be calculated as given below:
can be calculated as given below:
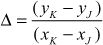
Therefore,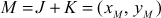
where,
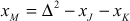
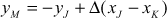
If the given two points are same 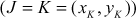 , then point doubling operation will be performed. The addition of two same points is called point doubling. For performing the point doubling operation,
, then point doubling operation will be performed. The addition of two same points is called point doubling. For performing the point doubling operation,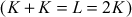 , the following equations are used. In the following equations, a new point
, the following equations are used. In the following equations, a new point 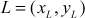 is computed based on calculating
is computed based on calculating 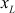 and
and 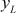 values.
values.
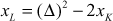
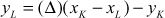
where,
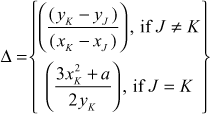
9.2.4 Point Multiplication
Point multiplication is performed by using both point addition and point doubling. In point addition, two distinct points are added to get a result of another point in the same elliptic curve. In point doubling, the same point is added to itself to get a result of another point in the same elliptic curve. In point multiplication, a scalar multiplication is performed between a value and a point. Let us consider a scalar value  which is multiplied with the base point
which is multiplied with the base point  in the elliptic curve to get a new point
in the elliptic curve to get a new point  on the same curve, i.e. to find
on the same curve, i.e. to find 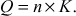
For example, If 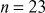 , then
, then 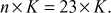 In this case, rather than multiplying the scalar value n with the base point
In this case, rather than multiplying the scalar value n with the base point 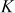 , point doubling and point addition operations are performed. In order to do that, the scalar value 23 is splitted into multiples of 2 to perform point doubling operation as shown below:
, point doubling and point addition operations are performed. In order to do that, the scalar value 23 is splitted into multiples of 2 to perform point doubling operation as shown below:
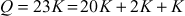
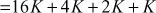
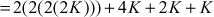
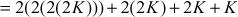
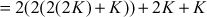
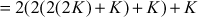
In the above example, point addition and point doubling are used to get the result of point multiplication 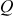 . The ECC is divided into two types, namely, prime curves and binary curves. Prime curves
. The ECC is divided into two types, namely, prime curves and binary curves. Prime curves 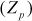 are very much useful for software-oriented applications, because it does not require extended bit-fiddling operation. Binary curves (GF(2n)) are more suitable for hardware application because it uses extended bit-fiddling operation. In this book, we have discussed about the prime curves (Zp)-based ECC.
are very much useful for software-oriented applications, because it does not require extended bit-fiddling operation. Binary curves (GF(2n)) are more suitable for hardware application because it uses extended bit-fiddling operation. In this book, we have discussed about the prime curves (Zp)-based ECC.
9.2.5 Elliptic Curve Over Zp
In ECC, the variables and coefficients of elliptic curve are limited to a finite field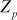 . For example, let us assume the elliptic curve
. For example, let us assume the elliptic curve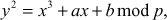 where
where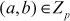 . In this curve, if
. In this curve, if 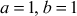 and
and 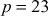 .Therefore, the curve becomes
.Therefore, the curve becomes 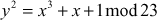 . In order to perform algebraic addition over the given elliptic curve that belongs to
. In order to perform algebraic addition over the given elliptic curve that belongs to 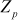 , let us consider two points on the elliptic curve
, let us consider two points on the elliptic curve 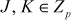 . The algebraic addition rules for elliptic curve over
. The algebraic addition rules for elliptic curve over 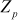 are summarized as follows:
are summarized as follows:
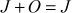
- If
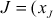 ,
, 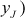 and
and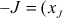 ,
, 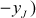 Then
Then 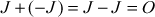
- If
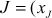 ,
, 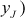 and
and 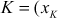 ,
, 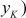 then
then 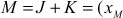 ,
, 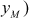 can be calculated as
can be calculated as
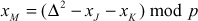
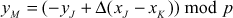
where
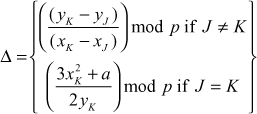
- Multiplication is done by performing repeated additions and point doubling operations. For example,
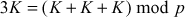 .
.
Example 9.1:
Let consider two different points 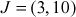 and
and 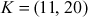 from the elliptic curve y2 = x3 + x + 1 mod 23. Perform the point addition between the two points
from the elliptic curve y2 = x3 + x + 1 mod 23. Perform the point addition between the two points 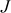 and
and 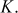
Solution
The slope between the two points can be calculated as
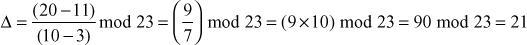
Let us consider 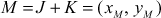 , then
, then
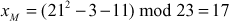
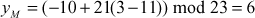
Therefore, 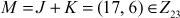 .
.
Suppose, If 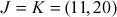 , then
, then  . In this case, point doubling operation as shown below:
. In this case, point doubling operation as shown below:
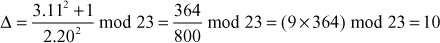
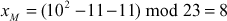
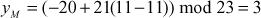
Therefore, 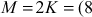 ,
, 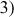
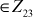 .
.
Example 9.2:
Let consider the elliptic curve 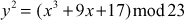 . Hence, this is the group which belongs to
. Hence, this is the group which belongs to 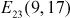 . Find the discrete logarithm
. Find the discrete logarithm  for the equation
for the equation 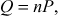 where
where 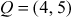 and
and 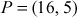 .
.
Solution
Let us assume that the intruder knows the values of 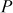 and
and 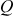 . Then, the intruder performs the brute-force method until the value of
. Then, the intruder performs the brute-force method until the value of 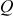 is reached to find the value of
is reached to find the value of  . The point addition and point doubling operations are used to perform brute-force method in the following manner.
. The point addition and point doubling operations are used to perform brute-force method in the following manner.
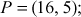
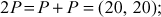
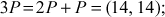
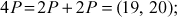
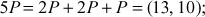
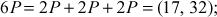
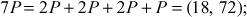
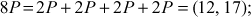
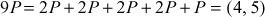
Here 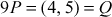 . Therefore, the value of the discrete logarithm
. Therefore, the value of the discrete logarithm  is 9. The brute force is infeasible to perform, if the value of
is 9. The brute force is infeasible to perform, if the value of  is so large.
is so large.
9.3 Diffie–Hellman Key Exchange using Elliptic Curves
The ECC is applied to Diffie–Hellman key exchange to resolve the vulnerability in key exchange problem. The following subsection gives an overall idea about Diffie–Hellman key exchange using elliptic curves.
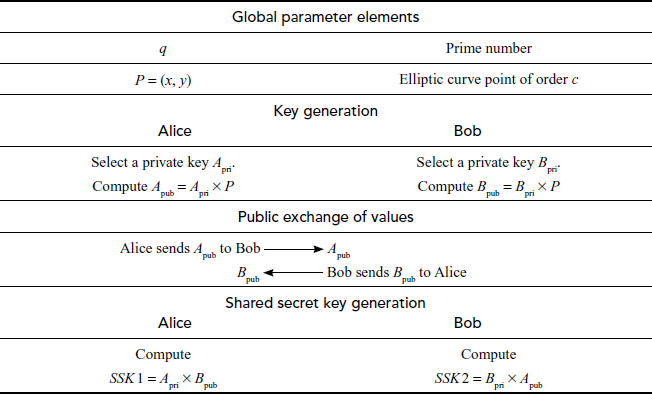
Step 1: Initially, Alice and Bob select an elliptic curve 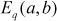 with parameters
with parameters 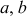 for a large prime number
for a large prime number 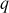 .
.
Step 2: Alice and Bob also select a base point P = (x, y) on the elliptic curve of order c such that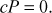 Here, c is the small positive integer. The value of
Here, c is the small positive integer. The value of 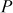 is known to all users in the system.
is known to all users in the system.
Step 3: Suppose Alice and Bob want to share a secret key. Alice selects a random integer 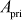 less than c which is considered as Alice’s private key. Alice does not disclose it to anyone. From this private key, Alice computes public key.
less than c which is considered as Alice’s private key. Alice does not disclose it to anyone. From this private key, Alice computes public key.
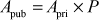
Step 4: Similarly, Bob selects a random integer 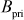 less than c independently which is Bob’s private key and does not disclose to anyone. Based on this, Bob also computes his public key.
less than c independently which is Bob’s private key and does not disclose to anyone. Based on this, Bob also computes his public key.
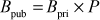
Step 5: These computed public key values are exchanged to each other. Alice transmits 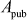 to Bob and Bob transmits
to Bob and Bob transmits 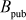 to Alice. Notice that the adversary Eve tries to view the values of
to Alice. Notice that the adversary Eve tries to view the values of 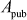 and
and 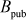 , since they are exchanged over the insecure communication channel.
, since they are exchanged over the insecure communication channel.
Step 6: From the public value (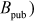 received from Bob, Alice can generate the shared secret key by using the following equation:
received from Bob, Alice can generate the shared secret key by using the following equation:
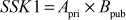
Step 7: Bob can also generate the shared secret key from
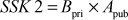
The values 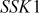 and
and 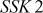 generated by Alice and Bob are really identical. This can be proved as given below:
generated by Alice and Bob are really identical. This can be proved as given below:
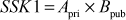
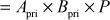
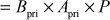
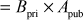 (by the rules of modular arithmetic)
(by the rules of modular arithmetic)
= 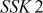
Figure 9.3 shows the diagrammatic representation of ECC-based Diffie–Hellman key exchange. Alice wishes to establish a secure communication link with Bob. Then, Alice and Bob choose distinct one-time private keys 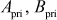 and then calculate
and then calculate 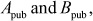 respectively. Alice sends
respectively. Alice sends 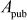 to Bob and Bob sends
to Bob and Bob sends 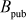 to Alice. Both Alice and Bob can calculate the shared secret key for communication. The summary of Diffie–Hellman key exchange using elliptic curves algorithm is shown in Table 9.1.
to Alice. Both Alice and Bob can calculate the shared secret key for communication. The summary of Diffie–Hellman key exchange using elliptic curves algorithm is shown in Table 9.1.
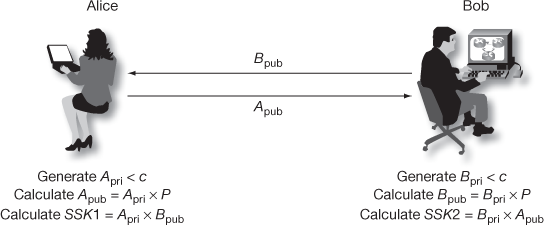
Figure 9.3 Diffie–Hellman key exchange using elliptic curves
Table 9.1 Summary of Diffie–Hellman key exchange algorithm using elliptic curves
9.4 Elgamal Cryptosystem using Elliptic Curves
The ECC-based Elgamal cryptosystem was described by Taher Elgamal in 1985. This cryptosystem is developed based on the ECC-based Diffie–Hellman key exchange algorithm. The ECC is applied to Elgamal cryptosystem to make the cryptosystem strong from vulnerabilities. This is consided to be strong because for larger key values it is infeasible to attack. ECC is also effective due to its shorter key length and higher efficiency on encryption and decryption [2]. The following subsection gives an overall idea about Elgamal cryptosystem using elliptic curves.
Step 1: Alice and Bob want to make secure communications with each other. Alice selects a message m to be communicated with Bob.
Step 2: Bob selects an elliptic curve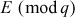 , where
, where 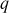 is a large prime number. In addition, Bob selects a base point
is a large prime number. In addition, Bob selects a base point 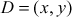 on the elliptic curve and a private key
on the elliptic curve and a private key 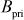 and then computes,
and then computes,
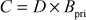
Step 3: Bob places 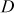 and
and 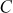 in the public directory and keeps the value
in the public directory and keeps the value 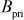 as secret.
as secret.
Step 4: Now, Alice selects a random integer  and then computes
and then computes
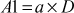
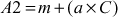
Step 5: Now, the pair 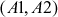 is sent to Bob. Bob decrypts the message
is sent to Bob. Bob decrypts the message 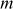 by computing
by computing
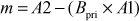
Proof of correctness:
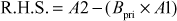
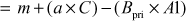 (Since,
(Since, 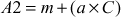 )
)
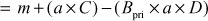 (Since,
(Since, 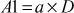 )
)
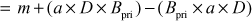 (Since
(Since 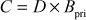 )
)
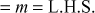
The steps involved in Elgamal cryptosystem which is based on the use of elliptic curves are depicted in Figure 9.4.
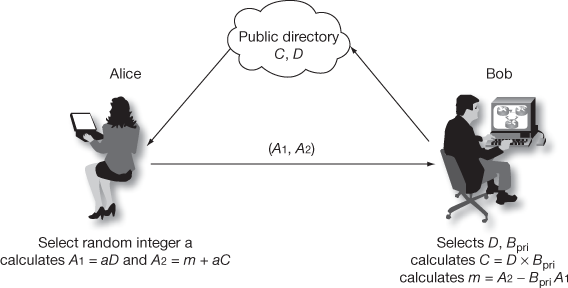
Figure 9.4 ECC-based Elgamal cryptosystem
Example 9.3:
Bob chooses an elliptic curve 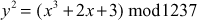 and
and 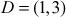 . He also chooses
. He also chooses 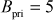 and then computes
and then computes 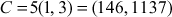 and publishes
and publishes 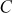 and
and 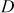 in the public directory. Alice desires to send the message
in the public directory. Alice desires to send the message 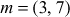 to Bob. Then Alice selects a random integer 3 and computes
to Bob. Then Alice selects a random integer 3 and computes
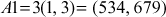
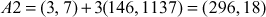
Now, the pair 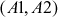 is sent to Bob. Bob decrypts the message m by computing
is sent to Bob. Bob decrypts the message m by computing
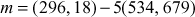
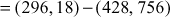
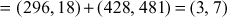
9.5 ECC-based Elgamal Digital Signature
The following subsection describes an overall idea about Elgamal digital signature using elliptic curves.
Step 1: Alice and Bob want to make communications with each other. Alice desires to send a message m to Bob and assumes that 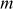 is an integer.
is an integer.
Step 2: Alice selects an elliptic curve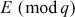 , where
, where 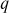 is a large prime number. If
is a large prime number. If 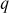 is not a large prime number, then
is not a large prime number, then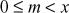 , where
, where  is the number of points on the elliptic curve E. Along with that, Alice selects a point
is the number of points on the elliptic curve E. Along with that, Alice selects a point 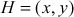 on the elliptic curve and a private key
on the elliptic curve and a private key 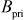 and then computes
and then computes
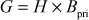
Step 3: Alice place G, H, x and the curve E in the public directory and keeps the value 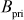 as secret.
as secret.
Step 4: Now, Alice wants to sign a message m. In order to do that, Alice selects a random integer a such that 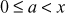
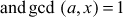 . After that, Alice computes the signature
. After that, Alice computes the signature 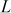 and
and 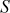 as given below:
as given below:
Step 5: Now, the signed message 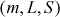 is sent to Bob. Bob verifies the signature S in the following way:
is sent to Bob. Bob verifies the signature S in the following way:
- Bob first gets the public information of Alice from the public directory.
- Then, computes
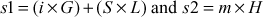
Proof of correctness:
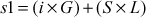
where, 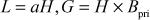 and
and 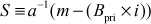
Therefore,
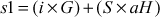
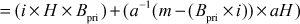
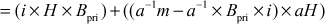
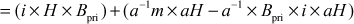
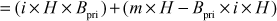
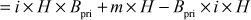
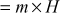
Since, 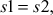 Bob declares the signature as a valid signature.
Bob declares the signature as a valid signature.
Key Terms
Abelian group
Elliptic curve cryptography
Elliptic curves
Point addition
Point doubling
Point multiplication
Summary
- Elliptic curve cryptography (ECC) is a public-key cryptography approach derived from the algebraic construction of elliptic curves over finite domains.
- The elliptic curves are described by cubic equations, Weierstrass equation are in the form of cubic equations for elliptic curves. The elliptic curve with standard form is represented as
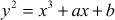 .
. - An abelian group is a set, denoted by A, together with an operation denoted by •, any two elements a, b in the set A form another element denoted a • b. The symbol • corresponds to the binary operation.
- In point addition, the two adding points that lie on an elliptic curve results in a third point on the curve.
- Point multiplication is performed by using both point addition and point doubling. In point addition, two distinct points are added to get a result of another point in the same elliptic curve.
- In point doubling the same point is added to itself to get a result of another point in the same elliptic curve.
Review Questions
- What is meant by elliptic curve cryptography?
- Define elliptic curves.
- Describe the five axioms of the abelian group.
- Explain elliptic curve-based Diffie–Hellman key exchange method in detail.
- Explain elliptic curve-based Elgamal cryptosystem in detail.
- Explain elliptic curve-based Elgamal digital signature method in detail.
- Explain point addition, point doubling, and point multiplication processes in detail.
References
- https://www.certicom.com/ecc
- Tzer-Long Chen, Yu-Fang Chung, Frank Y.S. Lin (2010), ‘An efficient date-constraint hierarchical key management scheme for mobile agents’, Experts Systems with Applications, 37: 7721–7728.