Chapter 1
Cryptography
1.1 Overview of Cryptography
The term ‘cryptography’ is derived from two Greek words, namely crypto and graphy. In Greek language, crypto means secret and graphy means writing. Cryptography is the science of secret writing that provides various techniques to protect information that is present in an unreadable format. This unreadable format can be converted into readable format only by the intended recipients. Advanced cryptography provides various techniques based on number theoretic approach and computer science and hence advanced cryptography techniques are virtually unbreakable. This book discusses about various cryptographic and advanced cryptographic techniques. Cryptographic techniques and protocols are used in a wide range of applications such as secure electronic transactions, secure audio/video broadcasting and secure video conferences. In secure electronic transactions, cryptographic techniques are used to protect E-mail messages, credit card information and other sensitive information. In secure audio/video broadcasting, the service provider sends the requested audio/video data to subscribers in a secure way. Only the authorized subscribers are allowed to view the multimedia data. Similarly, it is used in video conferences to allow multi-party communication, where, one user speaks and the remaining users view the communicated data in a secure way.
These secure applications are heavily dependent on various cryptographic services, namely confidentiality, authentication and data integrity. Based on these cryptographic services, the cryptographic techniques and protocols are classified into four main regions and are as follows:
- Symmetric encryption: Symmetric encryption is an encryption technique in which identical cryptographic key is used for both encrypting and decrypting the information. This key, in practice, must be secret between the sender and the receiver to maintain the secrecy of the information.
- Asymmetric encryption: Asymmetric encryption is an encryption technique where two keys are used as a pair. Among these two keys, one key is used for encryption and the other key is used for decryption of information. In the pair of keys, if the sender uses any one key to encrypt a message, the receiver should use another key to decrypt the message.
- Data integrity techniques: These techniques are used to protect information from alteration during the transmission. Data integrity techniques assure to maintain the accuracy and consistency of information over its entire life cycle.
- Authentication protocols: These are designed based on the use of cryptographic techniques to authenticate the identity of the sender. These protocols allow only the valid users to access the resources located on a server.
Even though there are so many cryptographic techniques and protocols available in the literature for providing various security services, security threats are still prevalent. The security attack is an internal act that breaks the security procedures or guidelines, regulations and requirements during the transmission of information from the sender to the receiver. The following are some examples of security attacks:
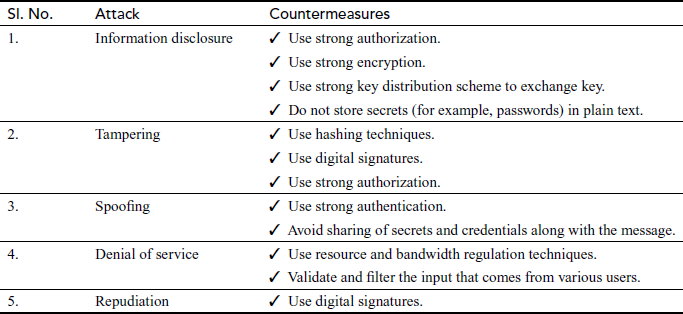
- The sensitive information transmitted from the sender to the receiver should be protected from disclosure. An intruder, who is unauthorized, can read the information by monitoring the transmission of information and capture a copy of information during its transmission. This attack is called information disclosure.
- When a higher authority transmits a message to user A (authorized receiver), another user B (intruder) may intercept the message and can modify the contents of the message. After modifying it, the user B can forward the message to user A, as if the message comes from the higher authority. This is called tampering attack.
- Instead of intercepting a message, user B can construct a message on its own desire and can transmit that message to user A as if it had come from the higher authority. The user A receives the message as it is coming from the higher authority. This is called spoofing attack.
- An intruder can send unwanted messages continuously to the destination and hence suppresses the communication channel between the sender and the receiver. This attack is called denial of service (DoS).
- User A sends a message to user C (authorized receiver). Later, user A can deny the message transmission that was sent to user C. Likewise, the recipient C can also deny the transmission that the message was not received. This attack is called repudiation.
Although there are many possible types of security attacks in the transmission network, network security has many countermeasures to detect, prevent and correct security violations during the transmission of information. Table 1.1 shows various countermeasures that are used to detect, prevent and correct these attacks.
Table 1.1 Attacks and countermeasures
1.2 Security Trends
Security is viewed as an important contest among hackers (who try to break the security) and security people (who provide security for the system). Therefore, it is desirable to know the emerging trends of security in order to be able to think about countermeasures and to avoid the hackers from breaking them. Security trends help to measure the security issues that are relevant to computer and networks. Based on the issues, we classify them into computer security and network security. Computer security is the process of protecting the computing systems and computer resources from unauthorized users. Similarly, network security is the process of protecting the network resources and transmitted information from unauthorized users. Computer security and network security are more essential for users who want to make their system free from hackers; otherwise the system would be compromised by hackers. The unprotected computer and communication link can be compromised by performing the following tasks within few seconds after connecting it to the Internet [1].
- The system is used to steal passwords and documentation keystrokes.
- The intruder may introduce attacks such as tampering attack, information disclosure attack, spoofing attack and DoS attack in the communication link.
- The system sends phishing and spam E-mails.
- The intruder can collect and send E-mail addresses and passwords.
- The intruder can access restricted personal information on your computer.
- The system distributes porn movies and child pornography illegal.
- The system can hide programs that introduce attacks on other computer systems.
- The intruder may slow down the entire network by generating large volumes of unnecessary traffic into the communication link.
Confidentiality, integrity and availability (CIA) are the three security trends that are used as heart of the network and computer security to protect computing systems, computer resources and network resources from unauthorized access, use, disclosure, disruption and modification [2]. Figure 1.1 shows CIA security trends.

Figure 1.1 CIA security trends
- Confidentiality: This term encompasses the following two interrelated concepts:
– Data confidentiality: It is a security service that protects the confidential information by preventing the unauthorized users from accessing it.
– Privacy: It promises that an individual is free from secret surveillance of personal information to be disclosed.
- Integrity: This term encompasses the following two interrelated concepts:
– Data integrity: It ensures that protected information is not changed by unauthorized users. The information and programs are modified only by the authorized entities.
– System integrity: It promises that a system performs its intended function without any degradation due to changes or disruptions in its internal or external environments.
- Availability: It assures that the system works in time to perform its designated or required function without denying the services to the authorized users.
The Challenges of Network and Computer Security
The following are the challenges of network and computer security:
- It is considered that confidentiality, authentication, non-repudiation and integrity are the major security requirements. But in practical cases, it is quite complex to meet those requirements.
- During the development of security mechanisms or algorithms for potential attacks, the attackers look at the problem in a totally different way and succeed by designing efficient attacks using an unexpected weakness in the mechanism.
- One of the necessary challenges is that the place in which the security mechanism is to be implemented is crucial. Moreover, the layer in which the security mechanism is to be implemented is also a critical challenge in order to increase the security level in the network applications.
- The secrecy of the transmitted information (e.g. an encryption key) depends on communication protocols. The behaviour of communication protocols may complicate for developing the security mechanisms. For example, proper functioning of the security mechanism requires time limits for data transmission. However, some of the protocols may introduce unpredictable delays and hence they would make time limits worthless.
- There is always a battle between a perpetrator who tries to find gaps and the designer who tries to fill the gaps in the computer and network security. The attacker always has a greater advantage to find a weakness, but the designer is required to find and eradicate all limitations to obtain perfect security.
- It is difficult to provide security requirements in today’s overloaded web environment.
1.3 The Open Systems Interconnection Security Architecture
As known earlier, the open systems interconnection (OSI) security architecture consists of seven layers, namely physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer. Among these seven layers, security is concerned only in the four layers namely, physical layer, network layer, transport layer and application layer. OSI security architecture is depicted in Figure 1.2. Application layer security mechanisms include electronic mail (S/MIME, PGP) security which is briefly explained in Chapter 13.
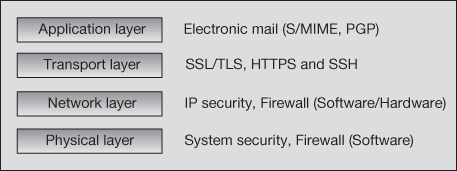
Web security is focused on the transport layer that concentrates on SSL/TLS, HTTPS and SSH. Chapter 14 gives the comprehensive explanation about the transport layer security. Network layer security includes IP security and firewall (hardware) which are briefly explained in Chapter 15. The system security focus on physical layer which includes malware identification and virus protection. The physical layer security is briefly explained in Chapter 16.
The OSI security architecture is used for organizing the work of providing security. The international telecommunication union (ITU) Telecommunication Standardization Sector (ITU-T) Recommendation X.800 is a United Nations-sponsored agency that defines a systematic approach of security architecture for OSI. Since this architecture was enlarged as an international standard, it is based on its structured definition of services and mechanisms. Computer and communication sellers have enlarged security features for their products and services. Security mechanisms, security services and security attacks are focussed in OSI security architecture and these are briefly explained as follows:
- Security mechanism: It is a process which is intended to detect, prevent and recover the stored/transmitted information from the security attack.
- Security service: It is a communication service that improves the security of the data processing systems and the information transfer as defined by ITU-T X.800 Recommendation. This service is designed to oppose security attacks, by using one or more security mechanisms.
- Security attack: It is the process of breaking or compromising the security of the stored/transmitted information without the knowledge of the sender and the receiver.
1.4 Security Attacks
The security attack is an attempt to break the security. There are two types of security attacks, namely passive attack and active attack. In passive attack, the attackers attempt to find out or use information from the system, without affecting the system resources. But in an active attack, an attacker tries to introduce unwanted data into the system as well as potentially change or modify the system resources or affect their operation.
1.4.1 Passive Attacks
In passive attacks, message transmissions are monitored by an adversary and thus the goal of the opponent is to acquire or learn information that is being sent in the network channel. Hence, it compromises confidentiality. There are two types of passive attacks. They are (1) release of message contents and (2) traffic analysis.
- Release of message contents
Figure 1.3 shows the process of release of message contents. In this attack, the sender sends sensitive or confidential information to the receiver. But an opponent captures the message and hence learns the contents of these transmissions. Hence, confidentiality of the sensitive or confidential information is compromised.
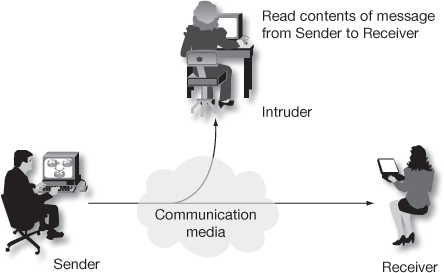
Figure 1.3 Release of message contents
- Traffic analysis
Figure 1.4 shows the process of traffic analysis. In this attack, the messages are encrypted and cannot be decrypted by the intruder. So if the intruder captures the message, then he/she cannot obtain the message from the transmission. Since the message is encrypted in the sender side, an intruder tries to observe the pattern of the message. From the observation, an intruder could find out the location and identity of the communicating parties and also observe the frequency and length of messages being transmitted. By using this information, an intruder can guess the nature of the communication between the sender and receiver that took place.
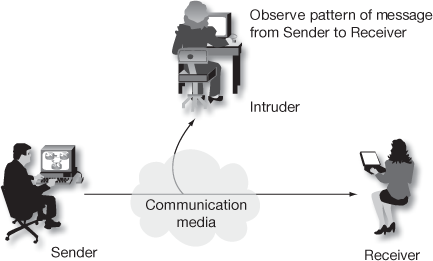
Figure 1.4 Traffic analysis
The detection of passive attacks is very hard compared to the detection of active attacks for the reason that they do not engage in the process of altering the transmitted data. Moreover, during the transmission of the messages, neither the sender nor the receiver knows that an intruder has read the messages in this attack. During transmission, passive attacks can be prevented by using strong encryption schemes. Therefore, it is better to prevent the passive attack rather than detecting it.
1.4.2 Active Attacks
Active attacks involve some modification of the system resources or the creation of false resources and hence affect their data transmission. So, active attacks compromise the integrity or availability feature. It can be subdivided into four categories: masquerade attack, replay attack, modification of messages attack and DoS attack.
- Masquerade attack
This attack takes place when one user pretends to be a different user to gain unauthorized access through legitimate access identification as shown in Figure 1.5. By using stolen passwords and logons, masquerade attacks can be performed.
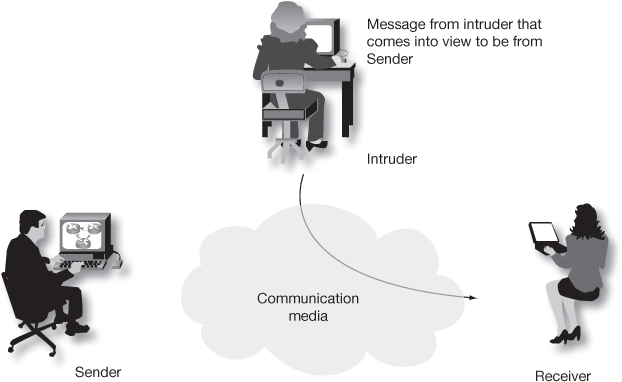
Figure 1.5 Masquerade attack
- Replay attack
Replay attack is also known as a playback attack in which a valid data is maliciously or fraudulently retransmitted or delayed to produce an unauthorized effect as shown in Figure 1.6.
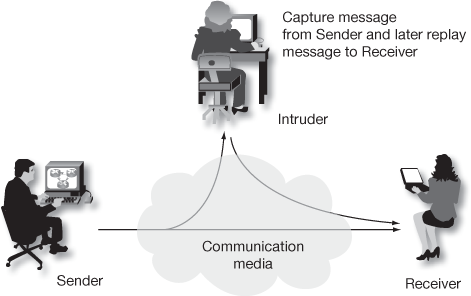
Figure 1.6 Replay attack
- Modification of messages attack
In this attack, an intruder either modifies or alters some portion of a legitimate message and hence it produces an unauthorized effect as depicted in Figure 1.7. For example, the sender sends a message ‘please transfer $5000 into my account 3048976’ to the receiver. This message can be captured by an intruder and modified as ‘please transfer $5000 in to my account 1234567’. After seeing this message, the receiver may transfer the amount $5000 in to the intruder’s account 1234567 who is not an intended user.
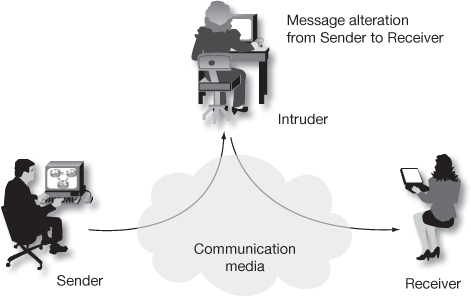
Figure 1.7 Modification of messages
- Denial of service attack
In this attack, an intruder may fix a specific target machine (server) and send some unwanted messages to that particular target machine in order to jam the communication media. Using this approach, the attackers formulate the network resources to be busy to its rightful users. This kind of attack is shown in Figure 1.8.
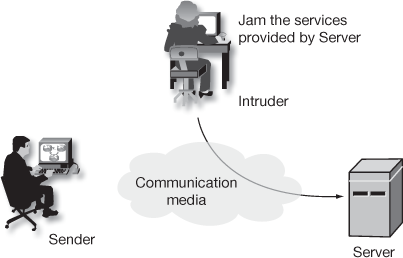
Figure 1.8 DoS attack
1.5 Security Services
Based on ITU-T X.800 Recommendation, security services are defined for the system resources and data transfers to provide a specific kind of protection. These services are also divided into five categories. Figure 1.9 shows the different categories of the security services [3].
Figure 1.9 Categories of security services
1.5.1 Authentication
Authentication is a process through which a system verifies the identity of an entity that wishes to access it. The private and public computer networks use logon passwords for performing authentication. Based on the knowledge of the password, it is assumed to promise that the user is authorized. In the initial process, each user assigns a self-declared password for registration. Hence, for each subsequent use, the user must be familiar with and apply the previously declared password. The main drawback in this system is that passwords are often stolen, accidentally disclosed or forgotten. So, digital signatures are used nowadays for authentication purposes. There are two specific types of authentication services defined in X.800:
- Peer entity authentication: In an association, if two entities are considered as peer entities, then they are in the same working environment or equivalent working environment of another system. Peer entity authentication is essential in two cases. The first case is the establishment of new connection, or at the time of initiating a secure data transfer. In peer entity authentication, the initiator of connection transfers authentication credentials such as passwords or signatures to another peer entity in order to avoid masquerade and replay attacks.
- Data origin authentication: In data origin authentication, the recipients are enabled to verify that messages are originated from the authenticated sender. However, data integrity is not ensured in this technique. This authentication technique is mainly used in E-mail systems.
1.5.2 Access Control
In network security, access control is a security service which has the ability to control the user access to the system resources located on a server. This service provides the access rights in which it maintains the information such as, who can access the system resources, under what conditions the user entities can access the system resources, and the list of the resources that the users are allowed to access.
1.5.3 Data Confidentiality
Confidentiality conceals the transmitted information from intruder’s passive attacks. An intruder may disclose the contents of transmitting information by applying passive attacks. Hence, the transmitted information should be protected when two users communicate with each other over a period of time. The other important feature of confidentiality is the protection of information from the traffic flow analysis. Otherwise, an intruder can observe the source and destination, frequency, length and different aspects of the activity on a correspondence channel.
1.5.4 Non-repudiation
Non-repudiation assures that the sender of the message cannot deny the transmitted message to the receiver in the case of dispute or query. Thus, the receiver can prove that the sender is the one who had actually sent the message. Similarly, the sender can also prove that the receiver has actually received the message.
1.5.5 Data Integrity
Data integrity is the process that ensures that the data transmitted from the sender to the receiver is not altered or modified by an intruder. It provides the correctness of the transmitted data since this service protects the transmitted data from alteration during communication.
Key Terms
Access control
Active attack
Authentication
Availability
Confidentiality
Data integrity
Denial of service
Intruder
Masquerade
Non-repudiation
Passive attack
Replay attack
Security attacks
Security services
Summary
- In network security, access control is a security service which has the ability to control the user access to the system resources located on a server.
- Active attacks involve some modification of the system resources or the creation of false resources and hence affect their data transmission.
- Authentication is a process through which a system verifies the identity of an entity that wishes to access it.
- Availability assures that the system works in time to perform its designated or required function without denying the services to the authorized users.
- Confidentiality conceals the transmitted information from intruder’s passive attacks.
- Data integrity is the process that ensures that the data transmitted from the sender to the receiver is not altered or modified by an intruder.
- Denial of service (DoS) is an attack in which an intruder may fix a specific target machine (server) and then may send some unwanted messages to that particular target machine in order to jam the communication media.
- Masquerade attack takes place when one user makes belief to be a different user to gain unauthorized access through legitimate access identification.
- Non-repudiation assures that the sender of the message cannot deny the transmitted message to the receiver in the case of dispute or query.
- In passive attacks, message transmissions are monitored by an adversary and thus the goal of the opponent is to acquire or learn information that is being sent in the network channel.
- Replay attack is also known as a playback attack in which a valid data is maliciously or fraudulently retransmitted or delayed to produce an unauthorized effect.
- The security attack is an attempt to break the security.
- Based on ITU-T X.800 Recommendation, security services is defined for the system resources and data transfers to provide a specific kind of protection.
Review questions
- What is meant by passive attack?
- What is meant by active attack?
- What is the difference between passive and active attacks?
- Give brief explanation about the OSI security architecture.
- List and briefly explain about different categories of the security services.
- List and briefly explain about various security attacks.
- What are the challenges of network and computer security?
- What is the difference between symmetric encryption and asymmetric encryption?
- Give some attacks and its corresponding countermeasures in cryptography.
References
- http://its.ucsc.edu/security/training/intro.html
- Committee on National Security Systems: National Information Assurance (IA) Glossary, CNSS Instruction No. 4009, 26 April 2010.
- Stallings, William (2007), Network Security Essentials: Applications and Standards (Upper Saddle River, NJ: Prentice Hall)– pp. 413.
