This type of infection is relatively easy to detect. This type of infection was also discussed in Chapter 4, ELF Virus Technology – Linux/Unix Viruses. This technique relies on the fact that there is always going to be a minimum of 4,096 bytes between the text and the data segment because they are loaded into memory as two separate memory segments, and memory mappings are always page aligned.
On 64-bit systems, there is typically 0x200000 (2MB) free due to
PSE (Page size extension) pages. This means that a 64-bit ELF binary can be inserted with a 2MB parasite, which is much larger than what is typically needed for an injection space. With this type of infection, like any other, you can often identify the parasite location by examining the control flow.
With the lpv virus which I wrote in 2008, for instance, the entry point is modified to start execution at the parasite that is inserted using the text segment padding infection. If the executable that has been infected has a section header table, you will see that the entry point address resides in the range of the last section within the text segment. Let's take a look at a 32-bit ELF executable that has been infected using this technique.
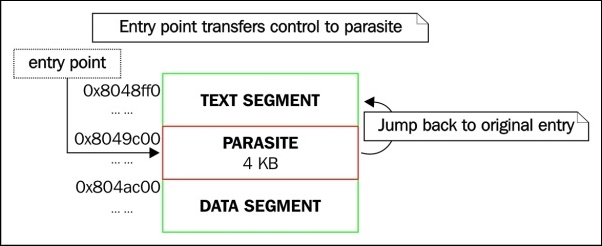
Illustration – Diagram showing a text segment padding infection
The following is an ELF file header of the lpv infected file:
$ readelf -h infected.lpv
ELF Header:
Magic: 7f 45 4c 46 01 01 01 00 00 00 00 00 00 00 00 00
Class: ELF32
Data: 2's complement, little endian
Version: 1 (current)
OS/ABI: UNIX - System V
ABI Version: 0
Type: EXEC (Executable file)
Machine: Intel 80386
Version: 0x1
Entry point address: 0x80485b8
Start of program headers: 52 (bytes into file)
Start of section headers: 8524 (bytes into file)
Flags: 0x0
Size of this header: 52 (bytes)
Size of program headers: 32 (bytes)
Number of program headers: 9
Size of section headers: 40 (bytes)
Number of section headers: 30
Section header string table index: 27Notice the entry point address, 0x80485b8. Does this address point somewhere inside the .text section? Let's take a peek at the section header table and find out.
The following is an ELF section headers of the lpv infected file:
$ readelf -S infected.lpv
There are 30 section headers, starting at offset 0x214c:
Section Headers:
[Nr] Name Type Addr Off
Size ES Flg Lk Inf Al
[ 0] NULL 00000000 000000
000000 00 0 0 0
[ 1] .interp PROGBITS 08048154 000154
000013 00 A 0 0 1
[ 2] .note.ABI-tag NOTE 08048168 000168
000020 00 A 0 0 4
[ 3] .note.gnu.build-i NOTE 08048188 000188
000024 00 A 0 0 4
[ 4] .gnu.hash GNU_HASH 080481ac 0001ac
000020 04 A 5 0 4
[ 5] .dynsym DYNSYM 080481cc 0001cc
000050 10 A 6 1 4
[ 6] .dynstr STRTAB 0804821c 00021c
00004a 00 A 0 0 1
[ 7] .gnu.version VERSYM 08048266 000266
00000a 02 A 5 0 2
[ 8] .gnu.version_r VERNEED 08048270 000270
000020 00 A 6 1 4
[ 9] .rel.dyn REL 08048290 000290
000008 08 A 5 0 4
[10] .rel.plt REL 08048298 000298
000018 08 A 5 12 4
[11] .init PROGBITS 080482b0 0002b0
000023 00 AX 0 0 4
[12] .plt PROGBITS 080482e0 0002e0
000040 04 AX 0 0 16
[13] .text PROGBITS 08048320 000320
000192 00 AX 0 0 16
[14] .fini PROGBITS 080484b4 0004b4
000014 00 AX 0 0 4
[15] .rodata PROGBITS 080484c8 0004c8
000014 00 A 0 0 4
[16] .eh_frame_hdr PROGBITS 080484dc 0004dc
00002c 00 A 0 0 4
[17] .eh_frame PROGBITS 08048508 000508
00083b 00 A 0 0 4
[18] .init_array INIT_ARRAY 08049f08 001f08
000004 00 WA 0 0 4
[19] .fini_array FINI_ARRAY 08049f0c 001f0c
000004 00 WA 0 0 4
[20] .jcr PROGBITS 08049f10 001f10
000004 00 WA 0 0 4
[21] .dynamic DYNAMIC 08049f14 001f14
0000e8 08 WA 6 0 4
[22] .got PROGBITS 08049ffc 001ffc
000004 04 WA 0 0 4
[23] .got.plt PROGBITS 0804a000 002000
000018 04 WA 0 0 4
[24] .data PROGBITS 0804a018 002018
000008 00 WA 0 0 4
[25] .bss NOBITS 0804a020 002020
000004 00 WA 0 0 1
[26] .comment PROGBITS 00000000 002020
000024 01 MS 0 0 1
[27] .shstrtab STRTAB 00000000 002044
000106 00 0 0 1
[28] .symtab SYMTAB 00000000 0025fc
000430 10 29 45 4
[29] .strtab STRTAB 00000000 002a2c
00024f 00 0 0 1The entry point address falls within the .eh_frame section that is the last section in the text segment. This is clearly not the .text section that is enough reason to become immediately suspicious, and because the .eh_frame section is the last section in the text segment (which you can verify by using readelf -l), we are able to deduce that this Virus infection is probably using a text segment padding infection.The following are ELF program headers of the lpv infected file:
$ readelf -l infected.lpv Elf file type is EXEC (Executable file) Entry point 0x80485b8 There are 9 program headers, starting at offset 52 Program Headers: Type Offset VirtAddr PhysAddr FileSiz MemSiz Flg Align PHDR 0x000034 0x08048034 0x08048034 0x00120 0x00120 R E 0x4 INTERP 0x000154 0x08048154 0x08048154 0x00013 0x00013 R 0x1 [Requesting program interpreter: /lib/ld-linux.so.2] LOAD 0x000000 0x08048000 0x08048000 0x00d43 0x00d43 R E 0x1000 LOAD 0x001f08 0x08049f08 0x08049f08 0x00118 0x0011c RW 0x1000 DYNAMIC 0x001f14 0x08049f14 0x08049f14 0x000e8 0x000e8 RW 0x4 NOTE 0x001168 0x08048168 0x08048168 0x00044 0x00044 R 0x4 GNU_EH_FRAME 0x0014dc 0x080484dc 0x080484dc 0x0002c 0x0002c R 0x4 GNU_STACK 0x001000 0x00000000 0x00000000 0x00000 0x00000 RW 0x10 GNU_RELRO 0x001f08 0x08049f08 0x08049f08 0x000f8 0x000f8 R 0x1 Section to Segment mapping: Segment Sections... 00 01 .interp 02 .interp .note.ABI-tag .note.gnu.build-id .gnu.hash .dynsym .dynstr .gnu.version .gnu.version_r .rel.dyn .rel.plt .init .plt .text .fini .rodata .eh_frame_hdr .eh_frame 03 .init_array .fini_array .jcr .dynamic .got .got.plt .data .bss 04 .dynamic 05 06 07 08 .init_array .fini_array .jcr .dynamic .got
Based on everything highlighted in the preceding program header output, you can see the program entry point, the text segment (the first LOAD program header), and the fact that .eh_frame is the last section in the text segment.
