This is a virus infection technique that we discussed in Chapter 4, ELF Virus Technology – Linux/Unix Viruses. The idea is that a virus or parasite can make room for its code by extending the text segment in reverse. The program header for the text segment will look strange if you know what you're looking for.
Let's take a look at an ELF 64-bit binary that has been infected with a virus that uses this parasite infection method:
readelf -l ./infected_host1
Elf file type is EXEC (Executable file)
Entry point 0x3c9040
There are 9 program headers, starting at offset 225344
Program Headers:
Type Offset VirtAddr PhysAddr
FileSiz MemSiz Flags Align
PHDR 0x0000000000037040 0x0000000000400040 0x0000000000400040
0x00000000000001f8 0x00000000000001f8 R E 8
INTERP 0x0000000000037238 0x0000000000400238 0x0000000000400238
0x000000000000001c 0x000000000000001c R 1
[Requesting program interpreter: /lib64/ld-linux-x86-64.so.2]
LOAD 0x0000000000000000 0x00000000003ff000 0x00000000003ff000
0x00000000000378e4 0x00000000000378e4 RWE 1000
LOAD 0x0000000000037e10 0x0000000000600e10 0x0000000000600e10
0x0000000000000248 0x0000000000000250 RW 1000
DYNAMIC 0x0000000000037e28 0x0000000000600e28 0x0000000000600e28
0x00000000000001d0 0x00000000000001d0 RW 8
NOTE 0x0000000000037254 0x0000000000400254 0x0000000000400254
0x0000000000000044 0x0000000000000044 R 4
GNU_EH_FRAME 0x0000000000037744 0x0000000000400744 0x0000000000400744
0x000000000000004c 0x000000000000004c R 4
GNU_STACK 0x0000000000037000 0x0000000000000000 0x0000000000000000
0x0000000000000000 0x0000000000000000 RW 10
GNU_RELRO 0x0000000000037e10 0x0000000000600e10 0x0000000000600e10
0x00000000000001f0 0x00000000000001f0 R 1On Linux x86_64, the default virtual address for the text segment is 0x400000. This is because the default linker script used by the linker says to do so. The program header table (marked by PHDR, as highlighted in the preceding) is 64 bytes into the file and will therefore have a virtual address of 0x400040. From looking at the program headers in the preceding output, we can see that the text segment (the first LOAD line) does not have the expected address; instead it is 0x3ff000. Yet the PHDR virtual address is still at 0x400040, which tells you that at one point so was the original text segment address, and that something strange is going on here. This is because the text segment was essentially extended backward, as we discussed in Chapter 4, ELF Virus Technology – Linux/Unix Viruses.
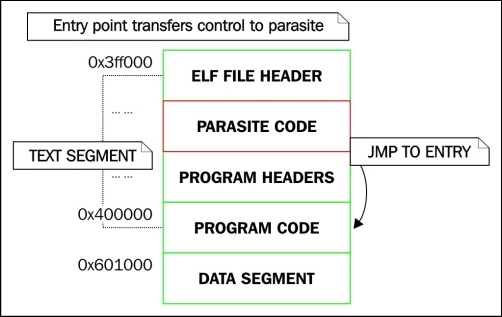
Illustration – Diagram showing a reverse-text-infected executable
The following is an ELF file header of reverse-text-infected executables:
$ readelf -h ./infected_host1 ELF Header: Magic: 7f 45 4c 46 02 01 01 00 00 00 00 00 00 00 00 00 Class: ELF64 Data: 2's complement, little endian Version: 1 (current) OS/ABI: UNIX - System V ABI Version: 0 Type: EXEC (Executable file) Machine: Advanced Micro Devices X86-64 Version: 0x1 Entry point address: 0x3ff040 Start of program headers: 225344 (bytes into file) Start of section headers: 0 (bytes into file) Flags: 0x0 Size of this header: 64 (bytes) Size of program headers: 56 (bytes) Number of program headers: 9 Size of section headers: 64 (bytes) Number of section headers: 0 Section header string table index: 0
I have highlighted everything in the ELF header that is questionable:
- Entry point points into parasite area
- Start of program headers should only be 64 bytes
- Section header table offset is 0, as in stripped
