This method is extremely powerful and, although easily detectable, is also relatively easy to implement and provides reliable code insertion. The idea is to convert the PT_NOTE segment to the PT_LOAD type and move its position to go after all of the other segments. Of course, you could also just create an entirely new segment by creating a PT_LOAD phdr entry, but since a program will still execute without a PT_NOTE segment, you might as well convert it to PT_LOAD. I have not personally implemented this technique for a virus, but I have designed a feature in Quenya v0.1 that allows you to add a new segment. I also did an analysis of the Retaliation Linux virus authored by Jpanic, which uses this method for infection:
http://www.bitlackeys.org/#retaliation.
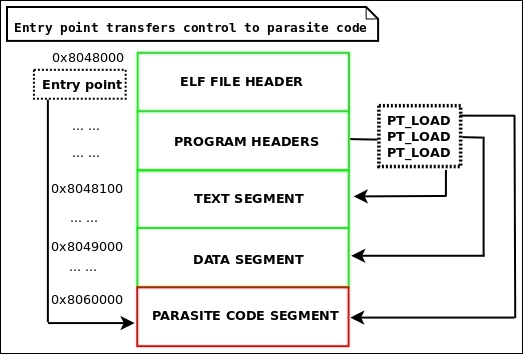
Figure 4.5: PT_LOAD infection
There are no strict rules about the PT_LOAD infection. As mentioned here, you may convert PT_NOTE into PT_LOAD or create an entirely new PT_LOAD phdr and segment.
- Locate the data segment
phdr:- Find the address where the data segment ends:
ds_end_addr = phdr->p_vaddr + p_memsz
- Find the file offset of the end of the data segment:
ds_end_off = phdr->p_offset + p_filesz
- Get the alignment size used for the loadable segment:
align_size = phdr->p_align
- Find the address where the data segment ends:
- Locate the
PT_NOTEphdr:- Convert phdr to PT_LOAD:
phdr->p_type = PT_LOAD;
- Assign it this starting address:
ds_end_addr + align_size
- Assign it a size to reflect the size of your parasite code:
phdr->p_filesz += parasite_size phdr->p_memsz += parasite_size
- Convert phdr to PT_LOAD:
- Use
ehdr->e_shoff += parasite_sizeto account for the new segment. - Insert the parasite code by writing a new binary to reflect the ELF header changes and new segment.
