Chapter 7
BCH Codes
7.1 INTRODUCTION
A large class of powerful random-error-correcting cyclic codes had been formed by BCH codes that made remarkable generalization of the Hamming codes for multiple error correction. BCH codes were invented in 1959 by Alexis Hocquenghem, and independently in 1960 by Raj Chandra Bose and Dwijendra Kumar Ray-Chaudhuri. Thus the code has been named as BCH (Bose Chaudhuri Hocquenghem) code. The cyclic structure of this code was observed and subsequently generalization of binary BCH codes to codes of pm symbols (p is a prime) was done. However, in this chapter, the discussion will be confined to mainly binary BCH codes.
7.2 PRIMITIVE ELEMENTS
For any positive integers m (m ≥ 3) and t (t < 2m – 1), there exist a BCH code with following parameters.
Block length: |
n = 2m – 1 |
Number of parity-check digits: |
n – k ≤ mt |
Minimum distance: |
dmin ≥ 2t + 1 |
These features imply that this code is capable of correcting any combination of t or few numbers of errors in a block code n = 2m – 1 digits and hence it is called t-error-correcting BCH code. The generator polynomial of this code is specified in terms of its roots from Galois field GF(2m). If α is the primitive element of GF(2m), then the generator polynomial g(x) of t-error-correcting BCH code of length 2m – 1 is the lowest degree polynomial with the roots as α, α2, α3, ..., α2t and also the conjugates of them [i.e., g(αi) = 0, for 1≤ i ≤ 2t]. If Φi(x) has the root as αi, g(x) is least common multiple of Φ1(x), Φ2(x),…, Φ2t(x), i.e.,
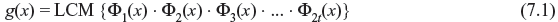
If i is even integer, this can be expressed as i = k2l, where k is odd integer and l ≥ 1. Then αi has a conjugate αk, and hence αi and αk have same polynomial. Therefore, g(x) may be expressed as follows:
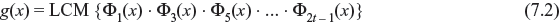
As the degree of each polynomial is m or less, the degree of g(x) is at most mt. From Eq. (7.2), the single-error-correcting code may be generated by g(x) = Φ1(x).
Example 7.1: For n = 7 and k = 4, t = 1, this means single-error-correcting code may be generated. Similarly, for n = 15 and k = 11, t = 1 or this is also a single-error-correcting code. For n = 15, double error correction and 3-error correction can be achieved with k = 7 and k = 5, respectively.
7.3 MINIMAL POLYNOMIALS
If Φ(x) is the polynomial with the coefficients from Galois field GF(2m), which is irreducible, it is called minimal polynomial. It has the degree ≤m and it divides x2m + x. For example, the minimal polynomials of γ = α7 in GF(24) is ɸ(x) = 1 + x3 +x4.
Minimal polynomials are obtained by solving the equation
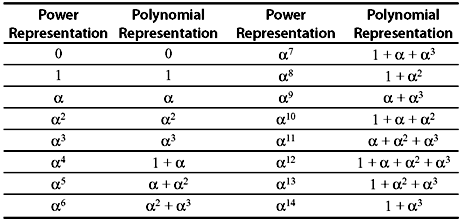
where x is substituted by γ = α7 and m = 4 for GF(24). The minimal polynomials generated by p(x) = x4 + x + 1 are given at Table 7.1.
Table 7.1 Minimal Polynomials in GF (24) Generated by p(x) = x3 + x + 1
| Conjugate Roots | Minimal Polynomials |
|---|---|
0 |
x |
1 |
x + 1 |
α, α2, α4, α8 |
x4 + x + 1 |
α3, α6, α9, α12 |
x4 + x3 + x2 + x + 1 |
α5, α10 |
x2 + x + 1 |
α7, α11, α13, α14 |
x4 + x3 + 1 |
7.4 GENERATOR POLYNOMIALS
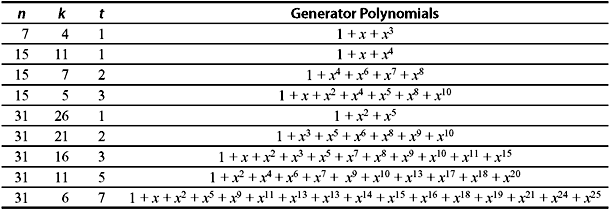
Using the minimal polynomials, Galois field of any order may be constructed and generator polynomials may be selected according to error-correction capability. A t-error-correcting BCH code, polynomial of code length of n = 2m – 1 may be generated where each code polynomial has the roots α, α2, α3, …, α2t and their conjugates. Now if v(x) is the code polynomial from GF(2), it is divisible by the minimal polynomials Φ1(x), Φ2(x), …, Φ2t(x). Therefore, v(x) is also divisible by their least common multiple or generator polynomial g(x), where g(x) = LCM {Φ1(x) · Φ2(x) · Φ3(x) … Φ2t(x)}. A list of generator polynomial of binary BCH codes of block length up to 25 – 1 is given in Table 7.2.
Table 7.2 Generator Polynomials of BCH Code
If t-error-correcting code polynomial v(x) = v0 + v1x + v2x2 + … + vn _ 1xn – 1 of code length 2m – 1 has the root αi, then
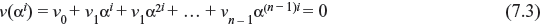
If we consider a matrix H consisting of the primitive elements that are the roots of the code vector as follows:
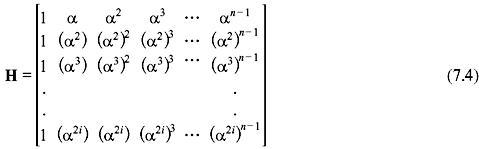
As v is a code vector, then v · HT = 0. (7.5)
The BCH code with minimum distance at least d0 has no more than m(d0 – 1) parity-check digits and capable of correcting (d0 – 1)/2 or fewer errors. The lower bound on minimum distance is called the BCH bound.
A list of primitive elements for minimal polynomials for 1< m ≤ 6 is given in Table 7.3.
Table 7.3 Primitive Elements of Minimal Polynomials
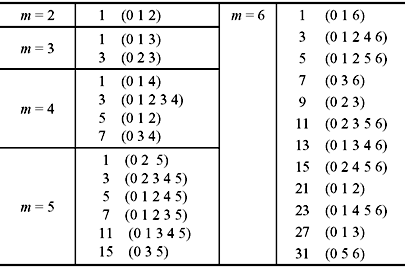
Example 7.2: If α be the primitive element of Galois field GF(24), with 1 + α + α4 = 0, the minimal polynomials are
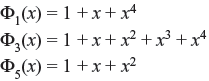
Double-error-correction BCH code of length n = 24 – 1 = 15 is generated by
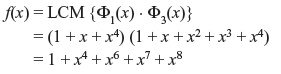
Thus, this code is (15, 7) cyclic code of dmin = 5.
Similarly, triple-error-correcting (15, 5) code with dmin = 7 may be generated by the generator polynomial
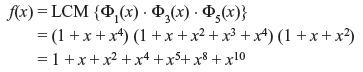
7.5 DECODING OF BCH CODES
Let us consider that the transmitted code vector v(x) = v0 + v1x + v2x2 + … + vn _ 1xn – 1 is received as r(x) = r0 + r1x + r2x2 + … + r n _ 1xn – 1. If e(x) is error introduced then
Syndrome vector can be calculated as
where H is given in Eq. (7.4). The ith component of syndrome is Si = r(αi), i.e., for 1≤ i ≤ 2t
It may be noticed that syndrome components are the elements in the field GF(2m). Dividing r(x) by the minimal polynomial Φi(x) of αi, we have r(x) = ai(x)Φi(x) + bi(x), where bi(x) is the remainder with degree less than that of Φi(x). Now Φi(αi) = 0, therefore
Thus the syndrome components may be obtained by evaluating bi(x) with x = αi. Since αi is the root of each code polynomial and v(αi) = 0, from Eqs. (7.6) and (7.9), for 1 ≤ i ≤ 2t, we may relate the syndrome components with the error pattern as follows:
It may be noticed that syndrome components Si depend on error pattern. Suppose there exists p number of errors in error pattern e(x) at locations xj1, xj2, ..., xjp, we may write
where 0 < j1 < j2 < ... < jp < n. From Eq. (7.10), we may derive the following set of equations for Si.
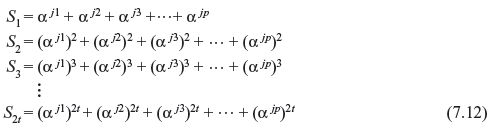
In the above set of equations, the roots αj1, αj2, αj3, ..., αjp are unknown. Solving these equations we may find the error locations. Any method for solving these equations is a decoding algorithm for BCH codes.
For convenience, αjl is substituted by β1, such that αj1 = βl for 0 < l < n. The elements βl are called the error location numbers. Eq. (7.12) may be rewritten as follows:
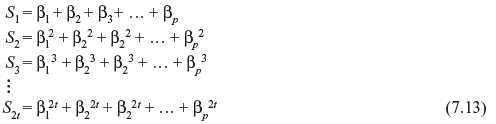
The above set of equations are symmetric functions of β1, β2, β3, …, βp, which are known as power-sum symmetric functions. Let us consider the following polynomial.
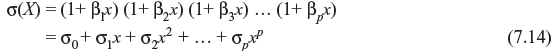
The roots of σ(x) are ![]() which are the inverse of the error location numbers, and therefore σ(x) is called as error location polynomial. σ0, σ1, σ2, ..., σp are the elementary symmetric functions of β1, β2, β3, ..., βp. The coefficients of σ(x) can be computed as per following relations.
which are the inverse of the error location numbers, and therefore σ(x) is called as error location polynomial. σ0, σ1, σ2, ..., σp are the elementary symmetric functions of β1, β2, β3, ..., βp. The coefficients of σ(x) can be computed as per following relations.
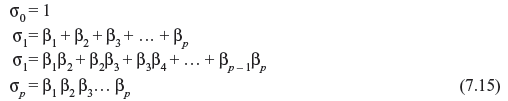
The σ0, σ1, σ2, ..., σp are known as the elementary symmetric functions of β1, β2, β3, ..., βp. From Eqs. (7.13) and (7.15), we can relate the syndrome components by following Newton’s identities.
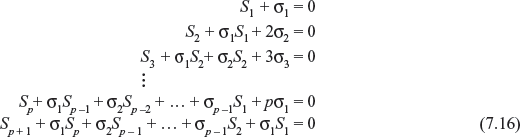
Solving the above equations for the elementary functions σ0, σ1, σ2, ..., σp, we may find out the error locations β1, β2, β3, ..., βp. Eq. (7.16) may have many solutions. However, the solution that yields σ(x) of minimal degree is to be considered for determining the error pattern. If p ≤ t, σ(x) will give the actual error pattern e(x). Therefore, the error correction procedure for BCH codes may be described as follows:
- Computation of syndromes from the received polynomial r(x).
- Determining of error location polynomial σ(x) from syndrome components S1, S2, S3, ..., S2t.
- Finding the roots of σ(x) to determine the error location numbers β1, β2, β3, ..., βp and correction of errors in r(x).
Finding the error location polynomial σ(x) is most complicated and can be achieved by iterative process. The first step is to search a minimum degree polynomial σ(1)(x) whose coefficients satisfy the first Newton’s identity of Eq. (7.16). In the next step, coefficients of σ(1)(x) are tested to satisfy the second Newton’s identity of Eq. (7.16). If this satisfies, then σ(2)(x) = σ(1)(x). If the coefficients of σ(1)(x) do not satisfy the second Newton’s identity, a correction term is added to σ(1)(x) to form σ(2)(x) such that σ(2)(x) has minimum degree and satisfies second Newton’s identity. Next σ(2)(x) is to be tested for third Newton’s identity equation. This iteration process is to be continued till all the Newton’s identity equations are tested and finally the error location polynomial will be obtained after 2tth iteration such that σ(x) = σ(2t)(x).
Let the minimal degree polynomial at the μth step of iteration whose coefficients satisfy the first μ Newton’s identity equations be
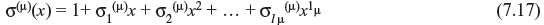
To determine σ(μ + 1)(x), we compute the following.
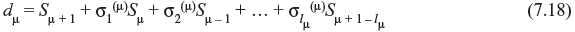
The quantity dμ is called μth discrepancy. If dμ = 0, the coefficients of σ(μ)(x) satisfy the (μ + 1)th Newton’s identity and σ(μ + 1)(x) = σ(μ)(x). If dμ ≠ 0, a correction term is to be added as stated earlier. To find the correction term, we have to consider the step prior to μth step, say ρth step, where ρth discrepancy dρ ≠ 0. If lρ is the degree of the polynomial σ(ρ)(x), where ρ – lρ has the largest value, then
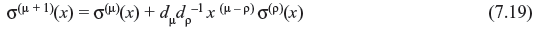
After completion of iterative method, the final error location polynomial σ(x) is determined. Now the error location numbers can be found simply by substituting 1, α, α2, ..., αn – 1 (n = 2m – 1) into σ(x) and subsequently the error pattern e(x) may be obtained. Therefore, the decoding process is to be performed on a bit-by-bit basis.
Example 7.3: Consider the (15, 5) triple-error-correcting BCH code in Galois field GF(24) such that 1 + α + α4 = 0. Assume that the code vector v = (000000000000000) has been received as r = (000101000000100).
Therefore,
The minimal polynomials of α, α2, and α4 are identical and
The minimal polynomials for α3 and α6 are
The minimal polynomial for α5 is Φ5(x) = 1 + x + x2
Dividing r(x) by above minimal polynomials, we obtain the remainders as follows:
Substituting α, α2, α4 in b1(x), α3, α4 in b3(x), and α5 in b5(x), we obtain the syndrome components as S1 = S2 = S4 = 1, S3 = 1 + α6 + α9 = α10, S6 = 1 + α12 + α18 = α5, and S5 = α10. These results are obtained from the polynomial representations of the elements of GF(24) as in Table 7.4.
Table 7.4 Polynomial Representation of Elements of GF(24)
To find the error location polynomial, the iterative method as described above is used. The steps and results of iterative process are indicated in Table 7.5. To begin the iterative process, for the first row, we assume μ = –1. Therefore, from Eqs. (7.17) and (7.18), σ(μ = –1)(x) = 1, dμ = –1 = 1 and lµ is the degree of σ(μ)(x).
For the next row μ = 0, σ(μ = 0)(x) = σ(μ = –1)(x) = 1 as dμ= –1 = 0. Now dμ = 0 = S1 = 1 from Eq. (7.18). Thus, the iterative process continues to develop till μ = 2t. The algorithm maintained is as follows:
- If d μ = 0, σ(μ + 1)(x) = σ(μ)(x) and 1μ + 1 = lμ.
- If dμ ≠ 0, another row to be found prior to μth, say ρth, such that ρ – lρ is maximum and dρ ≠ 0.
Then, σ(μ + 1)(x) is computed as from Eq. (7.19). In either case
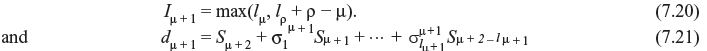
- If polynomial σ2t(x) in the last row has the degree greater than t, there are more than t errors that cannot be located.
Table 7.5 Iterative Process to Find the Error Location
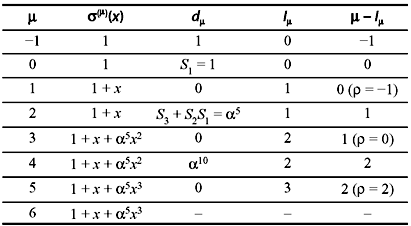
Thus, we obtain the error location polynomial
We can verify that α3, α10, and α12 are the roots of above error location polynomial σ(x). The inverse of these roots are α12, α5, and α3. Hence, the error pattern is e(x) = x3 + x5 + x12. Adding e(x) with r(x) we can recover errorless code vector.
7.6 IMPLEMENTATION OF GALOIS FIELD
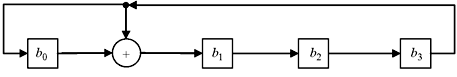
As discussed above, decoding of BCH codes requires computation using Galois field arithmetic that consists of mainly two operations—addition and multiplication. For addition operation, the resultant vector is the vector representation of the sum of the two field elements. The addition operation can be accomplished with circuit diagram shown in Figure 7.1.
Two elements are loaded in registers A(a0, a1, a2, a3) and B(b0, b1, b2, b3). Register A also serves as accumulator. The sum of two elements is available at the accumulator after applying triggering pulse to the adders.
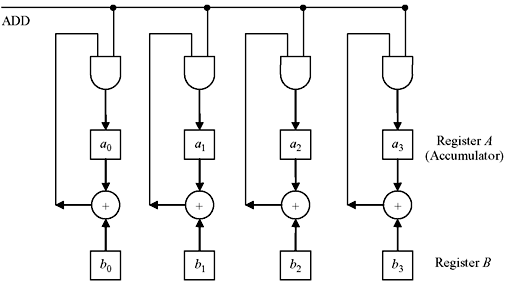
Figure 7.1 Schematic for Addition Operation
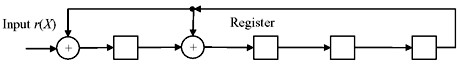
Figure 7.2 Multiplication Scheme of a Field Element with a Fixed Element
Multiplication of field element by a fixed element may be carried out using shift registers as shown at Figure 7.2. Let us consider the multiplication of field element B in GF(24) by primitive element α whose minimal polynomial is Φ(x) = 1 + x + x4. The element B can be expressed as a polynomial with respect to α as B = b0 + b1α + b2α2 + b3α3. Using the fact α4 = 1 + α, we obtain the equality, αΒ = b3 + (b0 + b3)α + b1α2 + b2α3, which can be realized by the circuit as shown in Figure 7.2.
Successive shifts of the shift register will generate the vector representation of successive powers of α according to the order in Galois field. If initially register is loaded with 1000, after 15th shift the register will contain 1000 again.
Now, let us consider the multiplication of two arbitrary field elements B and C, such that
The product BC may be written in the following form.
The steps of multiplication may be described as follows:
- Multiply c3B by α and add to c2B.
- Multiply (c3B)α + c2B by α and add to c1B.
- Multiply [(c3B)α + c2B)α + c1B by α and add to c0B.
Multiplication by α can be performed by the circuit as shown in Figure (7.2). Overall computation for the multiplication of two field elements B and C can be carried out by the schematic circuit diagram as shown in Figure (7.3). Here, the field elements B and C are loaded in the register B and register C, respectively. Register A is initially empty. After four simultaneous shifts of registers A and C, the desired product is available in register A.
The received vector r(x) may be computed in similar way. Figure 7.4 demonstrate the computation of r(αi), where α is the primitive element of GF(24).
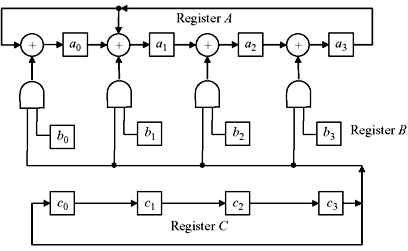
Figure 7.3 Multiplication Scheme for Two Field Elements
Figure 7.4 Computation of r(αi)
The received polynomial r(α) may be written as follows:
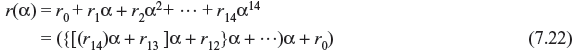
After 15th shift at shift register shown in Figure 7.4, the register will contain r(α) in vector form. It may be noted that the figures explained for implementation of Galois field are not unique. Various circuits may be realized according to operator polynomials.
7.7 IMPLEMENTATION OF ERROR CORRECTION
As discussed earlier, corrected data at the receiver end require syndrome computation, error location polynomial search and error correction. These can be implemented either by digital hardware or by software programmed on a general purpose computer. The advantage of hardware implementation is faster computation; but software implementation is less expensive.
7.7.1 Syndrome Computation
Syndrome components S1, S2, ..., S2t for t-error correction BCH code may be obtained by substituting the field elements α, α2, ..., α2t into the received polynomials r(x).
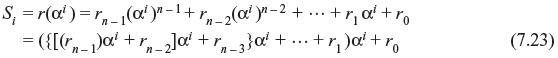
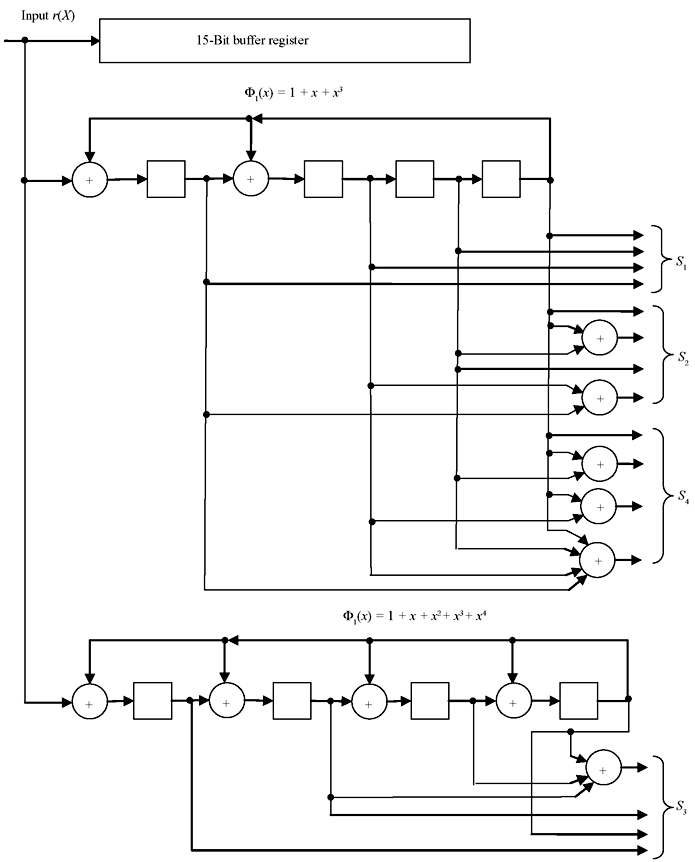
The computation consists of n – 1 additions and n – 1 multiplications which can be achieved by the hardware as described in Section 7.6. Since the generator polynomial is a product of at most t minimal polynomials, to form 2t syndrome components it requires at most t feedback shift registers, each containing at most m stages. It takes n clock cycles for complete computation. A syndrome computation circuit schematic for double-error-correcting (15, 7) BCH code is shown in Figure 7.5. As soon as the entire r(x) is received by the circuit, the 2t syndrome components are formed.
7.7.2 Computation of Error Location Polynomial
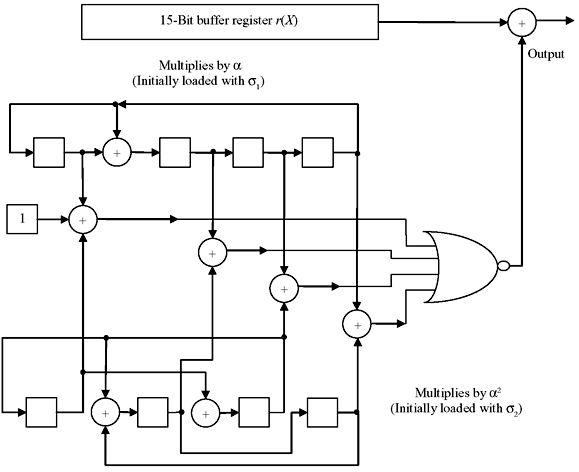
Since there are t numbers of error location polynomials σ(μ)(x) and t numbers of discrepancies dμ, computation of them requires 2t2 additions and 2t2 multiplications. Addition and multiplication circuits are already discussed which can be used to realize them. Figure 7.6 demonstrates Chein’s searching circuit, the schematic for finding the error locations.
Error location polynomial σ(x) of degree t is substituted by the field elements. Chein’s searching circuit consists of t multipliers for multiplying α, α2, ..., αt, respectively. Initially σ1, σ2, ..., σt are loaded into the registers of multipliers. After lth shift, these register will contain σ1αl, σ2α2l, ..., σtαtl. The sum 1 + σ1αl + σ2α2l + … + σtαtl is computed by m-input OR/NOR gate. If the sum is zero, the error location number is αn – 1. It requires n clock cycles to complete this step and k clock cycles to correct only the message bits.
Figure 7.5 Syndrome Computation Circuit for Double Error Correcting (15,7) BCH Code
Figure 7.6 Chein's Error Searching Circuit
7.8 NONBINARY BCH CODES
Apart from binary BCH codes, there exist nonbinary codes in Galois field. If p is a prime number and q is any power of p (q = pm), there are codes with symbols from the Galois field GF(q) which are called q-ary codes. The concepts and properties of q-ary codes are similar to binary code with little modification. An (n, k) linear code with symbols from GF(q) is a k-dimensional subspace of the vector space in GF(q). A q-ary (n, k) cyclic code is generated by a polynomial of degree n – k with coefficients from GF(q), which is a factor of xn – 1. Encoding and decoding of q-ary codes are similar to that of binary codes.
For any choice of positive integers s and t, there exists a q-ary BCH code of length n = qs – 1, which is capable of correcting any combination of t or fewer errors and requires no more than 2st parity-check digits. The generator polynomial g(x) of lowest degree with coefficients from GF(q) for a t-error-correcting q-ary BCH code, which has the roots α, α2, ..., α2t, may be generated from the minimal polynomials Φ1(x), Φ2(x), …, Φ2t(x), such that
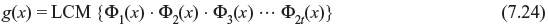
Each minimal polynomial has the degree s or less and hence the degree of g(x) is at most 2st and the number of parity-check digits of the code is no more than 2st. For q = 2, we obtain binary BCH code.
7.8.1 Reed-Solomon Code
Reed–Solomon code is one of the special subclass of q-ary BCH codes for which s = 1. A t-error-correcting Reed–Solomon code with primitive elements from GF(q) has the following parameters:
Block length: |
n = q – 1 |
Number of parity digits: |
n – k = 2t |
Minimum distance: |
dmin = 2t + 1 |
It may be noted that the length of this code is one less than the size of code symbols and minimum distance is one greater than the number of parity-check digits. For q = 2m with α as the primitive elements in GF(2m), the generator polynomial g(x) may be written as follows:
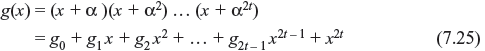
The code generated by g(x) is an (n, n – 2t) cyclic code consisting of the polynomials of degree n – 1 or less with coefficients from GF(2m) that are multiples of g(x). Encoding of this code is similar to the binary BCH code. If the message polynomial a(x) = a0 + a1x + a2x2 + ... + ak – 1 xk – 1 + ak xk is to be encoded, where k = n – 2t, remainder b(x) = b0 + b1x + b2x2 + ... + b2t – 1x2t – 1 is obtained dividing x2ta(x) by g(x). This can be accomplished by the schematic circuit as shown in Figure 7.7.
Here, the adders denotes the addition of two elements from GF(2m) and multipliers perform multiplication of field element from GF(2m) with a fixed element gi from the same field. Parity digits will be generated in the registers as soon as the message bits entered in the circuit.
Decoding of Reed–Solomon code is performed in similar process as described for binary BCH code. Decoding of this code consists of four steps: (1) computation of syndrome, (2) determining error location polynomial σ(x), (3) finding the error location numbers, and (4) evaluation of error values. The last step is not required in binary BCH code. If r(x), v(x), and e(x) are the received, transmitted, and error polynomials, respectively, then e(x) = r(x) – v(x). The syndrome components are obtained by substituting αi into received polynomial r(x) for i = 1, 2, 3, ..., 2t. Thus for αj1 = βl for 0 < l < p, we use Eq. (7.12) for q-ary BCH code and we have
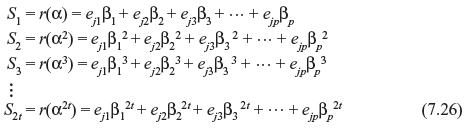
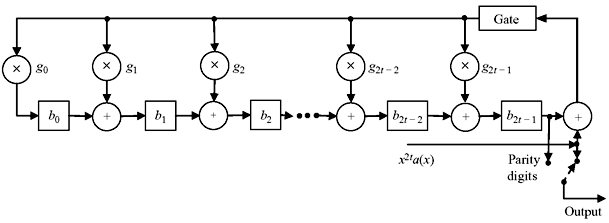
Figure 7.7 Encoding Scheme for Nonbinary BCH Code
The syndrome components Si can also be computed by dividing r(x) by x + αi, which results in the equality
The remainder bi is constant in GF(2m). Substituting αi in both sides of Eq. (7.27), we obtain Si = bi.
The error location polynomial is computed by iterative method, where
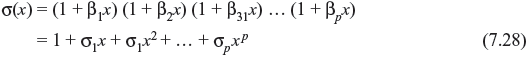
The error values can be determined by following computation. Let
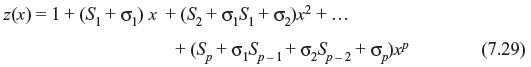
For i ≠ l, the error values at location βl = αjl is expressed as follows:

Example 7.4: Consider a triple-error-correcting Reed–Solomon code with symbols from GF(24). The generator polynomial of this code is
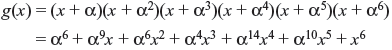
Let all-zero transmitted vector be received as r = (000α700α300000α400). Therefore, the received polynomial r(x) = α7x3 + α3x6 + α4x12. The syndrome components are calculated using Table 7.4 as follows:
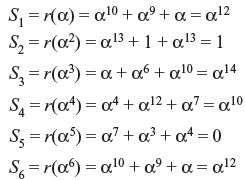
To find the error location polynomial σ(x), iterative process is used, steps of which is tabulated in Table 7.6. The error location polynomial thus is found to be σ(x) = 1 + α7x + α4x3 + α5x3. Substituting 1, α, α2, ..., α14 in σ(x), we find α3, α9, and α12 are the roots and hence the error locations are reciprocal of them as α12, α6, and α3. Now substituting the syndrome components in Eq. (7.29), we obtain that z(x) = 1 + α2x + x2 + α6x3. Using the error value relation as in Eq. (7.30), we obtain e3 = α7, e6 = α3, and e12 = α4. Thus, the error pattern is e(x) = α7x3 + α3x6 + α4x12. This is exactly similar to the error location as assumed. Decoding is complete by addition of received vector and error vector, i.e., r(x) + e(x) which is the desired data.
Table 7.6 Computation of Error Location Polynomial
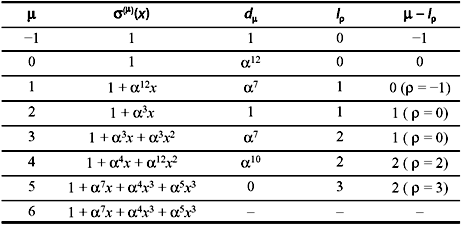
Reed–Solomon codes are very effective for correction of multiple burst errors.
7.9 WEIGHT DISTRIBUTION
The minimum distance of a linear code is the smallest weight of any nonzero code word, and is important because it directly affects the number of errors the code can correct. However, the minimum distance says nothing about the weights of other code words in the code; and hence, it is necessary to look at the weight distribution of the entire code. It turns out that the weight distribution of many types of codes, including Hamming and BCH codes, is asymptotically normal (i.e., it approaches the normal distribution for large codes of a given variety). If Ai is the number of code vectors of weight i in (n, k) linear code C, the numbers A1, A2, ., An are called the weight distribution of C. If C is used only for error detection on a binary symmetric channel (BSC), the probability of undetected errors can be computed from the weight distribution of C. Since an undetected error occurs only when the error pattern is identical to nonzero code vector of C, the probability of undetected error P(E) may be expressed as follows:

where p is the transition probability of the BSC. If the minimum distance of C is dmin, then A1 to Admin – 1 are zero. It has been observed that the probability of undetected error P(E) for a double-error-correcting BCH code of length 2m – 1 has the upper bound of 2–2m for p ≤ ½, where 2m is the number of parity digits of the code.
For t-error-correcting primitive BCH of length 2m – 1 with mt number of parity-check digits, where m is greater than certain constant m0(t), it has been observed that the weight distribution satisfies the following equalities:
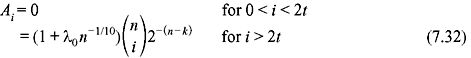
where n = 2m – 1 and λ0 is the upper bounded by a constant. From Eqs. (7.31) and (7.32), we obtain the expression for probability of undetected error P(E).
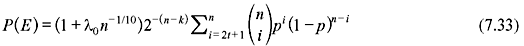
For ε = (2t + 1)/n and p < ε, the summation term of Eq. (7.33)
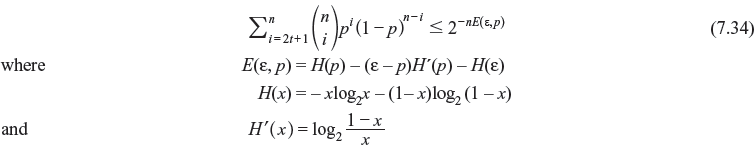
Therefore, for p < ε, the upper bound of P(E) is given as follows:
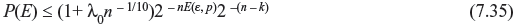
Similarly, for p > ε, since 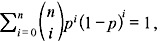 we have the upper bound of P(E) as follows:
we have the upper bound of P(E) as follows:

It may be noticed that probability of undetected error reduces exponentially with number of parity-check digits, n – k. Therefore, incorporation of sufficiently large number of parity digits results in reduction of probability of undetected errors. For nonbinary case, the weight distribution of t-error-correcting Reed–Solomon codes of length q – 1 with symbols from GF(q) is as follows:
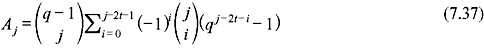
7.10 SOLVED PROBLEMS
Problem 7.1: Find the generator polynomial of a triple-error-correcting BCH code with block length n = 31 over GF(25).
Solution:
Block length: |
n = 2m – 1 = 31, m = 5 |
Error-correction capability |
t = 3 |
Number of parity-check digits: |
n – k ≤ mt = 5 × 3 = 15 |
Minimum distance: |
dmin ≥ 2t + 1 = 7 |
The minimal polynomials have the degree of less than or equal to 5 and they divide x25 + x or x32 + x. Triple-error-correcting BCH code of length 31 contains the lowest degree polynomial with the roots as α, α2, α3, ..., α6. The generator polynomial g(x) may be expressed as
As the degree of each polynomial is 5, the degree of g(x) is at most 15. From Table 7.3, the minimal polynomials are
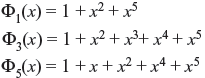
Therefore,
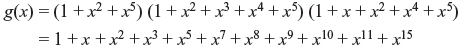
Problem 7.2: Find the parity-check matrix of a double-error-correcting (15, 4) BCH code.
Solution: For double-error-correcting (15, 4) BCH code the generator polynomial is Φ1(x) = 1 + x + x4 whose primitive element is α.
Then the parity-check matrix may be written as follows:
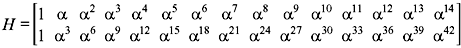
From the characteristics of primitive elements, we have α15 = α30 = 1, α18 = α33 = α3, α21 = α36 = α6, α24 = α39 = α9, and α42 = α12. Due to conjugate elements of α, the Eq. (7.4) is reduced to
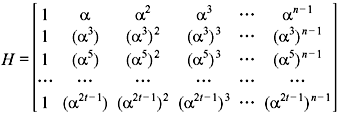
Using Table 7.4, the equivalent polynomial and its 4-tuple representation we obtain the following parity-check matrix.

Problem 7.3: Construct a double-error-correcting BCH code over GF(23).
Solution:
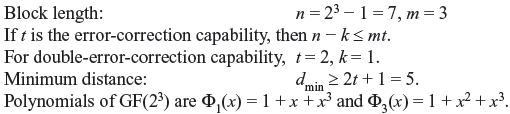
Double-error-correction code may be generated by the generator polynomial
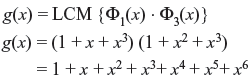
Problem 7.4: Construct the (15, 7) double-error-correcting BCH code and code word is C(x) = 1 + x4 + x6 + x7 + x8. Determine the outcome of a decoder when C(x) incurs the error pattern e(x) = 1 + x2 + x7.
Solution:
The generated code is (15, 7) and the minimal polynomials over GF(24)
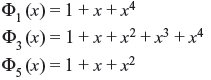
Double-error-correction BCH code is generated by the generator polynomial
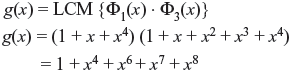
For the code word C(x) = 1 + x4 + x6 + x7 + x8 incurring error as e(x) = 1 + x2 + x7, the received vector r(x) = C(x) + e(x), i.e.,
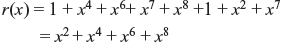
Therefore, the decoder output is x2 + x4 + x6 + x8.
Problem 7.5: Consider double-error-correcting code over GF(26) of the order of n = 21, where the element β = α3. Find the polynomial of minimum degree that has the roots β, β2, β3, and β4. Which BCH code may be developed?
Solution: The elements β, β2, and β4 have the same polynomial, Φ1(x) = 1 + x + x2 + x4 + x6.
The element β3 has the minimal polynomial Φ2(x) = 1 + x2 + x3.
Therefore, the generator polynomial of minimum degree is
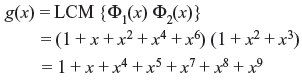
The above polynomial divides 1 + x21. As t = 2 and m = 6, k = n – mt = 9. Therefore, a (21, 9) BCH code may be generated.
Problem 7.6: Consider a triple-error-correcting binary BCH (15, 5) code with generator polynomial g(x) = 1 + x + x2 + x4 + x5 + x8 + x10. The received polynomial is r(x) = x3 + x5. Find the code word.
Solution: For t-error-correcting BCH code, the error location can be obtained by solving the following relation of syndrome matrix form.
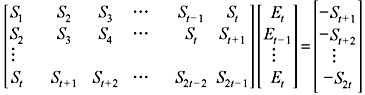
The syndromes are computed by substituting αi in the received polynomial r(x) = x3 + x5 for 1 ≤ i ≤ 2t, where t is error-correction capability. Using the Table 7.4, as t = 3, they are as follows:
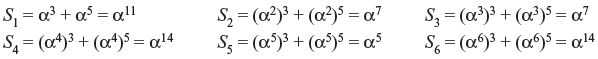
The syndrome matrix is obtained as below (number or rows and columns are limited to t = 3)
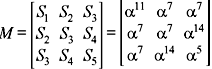
Det [M] = 0, which implies that there are fewer than three errors are present in the received vector. Next matrix has generated for t ≤ 2, which given as
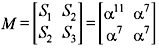
where Det [M] ≠ 0. Therefore, two errors have been occurred. Error location may be obtained from following matrix computation.

Solving the above equation, we obtain E2 = α8 and E1 = α11. Thus, error polynomial is e(x) = 1 + α11x + α8x2. This may be written as e(x) = (1 + α3x) (1 + α5x). Therefore, the error locations are at α3 and α5 or e(x) = x3 + x5. The code word may be computed as c(x) = r(x) + e(x) = x3 + x5 + x3 + x5 = 0. This means all-zero code word was sent.
MULTIPLE CHOICE QUESTIONS
- For m = 4, what is the block length of the BCH code?
- 16
- 15
- 16
- none of these
Ans. (b)
- What is the error-correction capability of a (15, 5) BCH code over GF(24)?
- 1
- 2
- 3
- 4
Ans. (c)
- If t is the error-correction capability of a BCH code what is the minimum distance of the code?
- 2t
- 2t + 1
- 2t – 1
- none of these
Ans. (b)
- For BCH code, if the received vector and computed error vector are r(x) and e(x), then the error-free code vector can be calculated as
- r(x) · e(x)
- r(x)/e(x)
- r(x) + e(x)
- none of these
Ans. (c)
- For (15, 5) BCH code, if the roots of error location polynomial α(x) are α2, α7, and α9, then error polynomial e(x) is
- x2 + x7 + x9
- x6 + x8 + x13
- x7 + x12 + x14
- none of these
Ans. (b)
- For a BCH code, if the minimal polynomials are Φi(x) (1 ≤ i ≤ 7), the generator polynomial g(x) of triple error correction is
- LCM{Ф1(x)Ф2(x)}
- LCM{Ф1(x)Ф3(x)}
- LCM{Ф1(x)Ф2(x)Ф3(x)}
- LCM{Ф1(x)Ф3(x)Ф5(x)}
Ans. (d)
- A BCH code over GF(26) can produce the code maximum error capability of
- 6
- 8
- 10
- 12
Ans. (c)
- A (63, 15) BCH code over GF(26) can produce the code maximum error capability of
- 6
- 8
- 10
- 12
Ans. (b)
REVIEW QUESTIONS
- Determine all generator polynomials for block length 31.
- Decode the BCH code of block length 3, if the received polynomials are r1(x) = x7 + x30 and r2(x) = 1 + x17 + x28.
- Prove that the syndrome components related as S2i = Si2.
- If a BCH code of length n = 2m – 1 has t-error-correcting capability and 2t + 1 is a factor of n, prove that the minimum distance of the code is exactly 2t + 1.
- Using p(x) = 1 + x2 + x5 devise a circuit that is capable of multiplying two elements in GF(25).
- Devise a syndrome computation circuit for a double-error-correcting (31, 21) BCH code.
- A t-error-correcting Reed–Solomon code of GF(2m) has the generator polynomial g(x) = (x + α)(x + α2)(x + α3) … (x + α2t).
Show that it has error-correction capability of 2t – 1, where α is the primitive element.
- Device a syndrome computation circuit for single-error Reed–Solomon code of block length 15 from field of GF(24).
- Find the generator polynomial of double-error-correcting Reed–Solomon code of block length 15 over GF(24). Decode the received polynomial r(x) = αx3 + α11x7.