Stack Memory 29
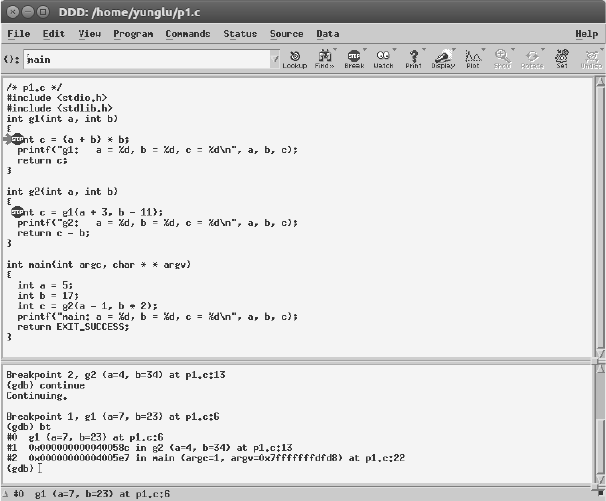
This command means “backtrace”. What do you see in the debugger?
(gdb) bt
#0 g1 (a=7, b=23) at p6.c:6
#1 0x0000000000400554 in g2 (a=4, b=34) at p6.c:13
#2 0x00000000004005b2 in main (argc=1, argv=0x7fffffffe4f8) at p1.c:22
The values of a and b are shown in the top frame. The beginning of each line shows the
frames (0, 1, and 2) of the call stack, corresponding to the functions g1, g2, and main. You
can use the f command to see different frames: for example, type
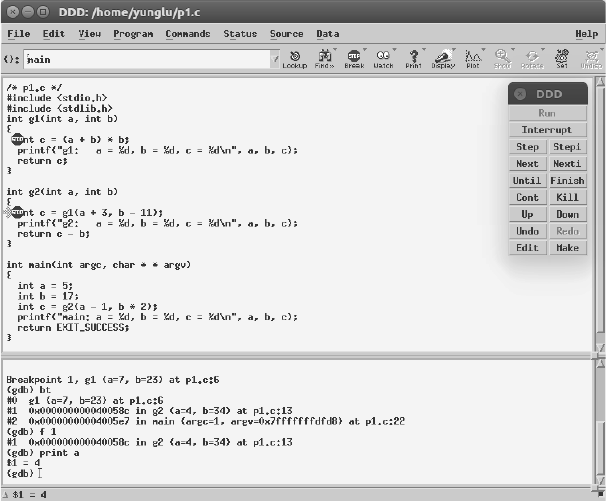
(gdb) f 1
to go to frame 1, i.e., the frame of function g2. The values of a and b can be displayed again.
What are their values? The digits after 0x are likely different on your computer; these are
the addresses. In g2’s frame, the values of a and b are different from the values in the top
frame. Fig. 2.6 to Fig. 2.9 show some screenshots of DDD.
FIGURE 2.6: Enter the commands at the bottom of DDD.
30 Intermediate C Programming
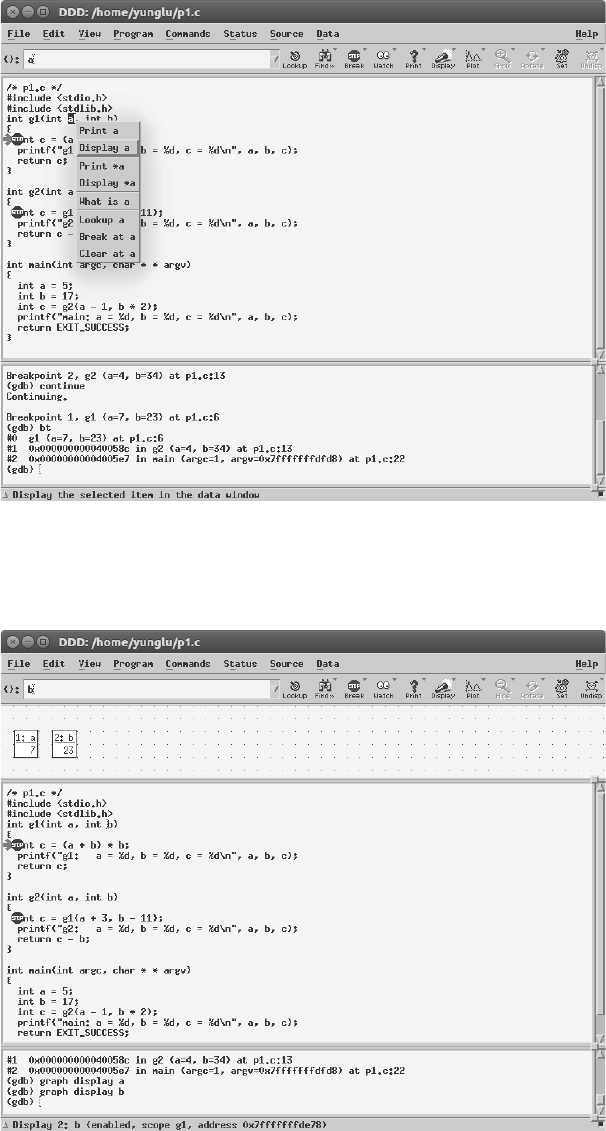
FIGURE 2.7: Use the mouse to select a inside g1. Click the right mouse button and select
“Display a”. Do the same for b.
FIGURE 2.8: The values of a and b in function g1 are shown.
Stack Memory 31
FIGURE 2.9: Use the f command to see different frames.
This page intentionally left blankThis page intentionally left blank
