Chapter 1
Through Hacker's Eyes
There is no way to describe the feeling of approaching a computer system to download the data that your Trojan horse has been collecting for days. Your heart begins to race. You look over your shoulder out of instinct and start to have major second thoughts about proceeding. The computer terminal is unoccupied and sits directly in front of you.
Questions plague your thoughts: How many people are capable of finding the cleverly hidden Trojan? More importantly, does anyone in this room know it is there? You ease yourself down into the chair. Glancing to your right you see a student stare at his calculator with a perplexed look on his face. To your left a girl is laughing on her cell phone. If you could shrink yourself into nothing and crawl through the cracks in the machine you would gladly do so. But you are physical and there is nothing you can do about that now. The coast is clear. You reach for your floppy and insert it into the drive. Sheens of sweat glaze over your palms. Why? Because after all, you are returning to the scene of a crime.
Your crime.
Deep down, you rationalize your actions. There is no blood involved, no money is being stolen, and in the end no real harm is being done. . . or is there? The floppy drive begins to spin. In moments it will be over. In moments all of the login/password pairs will be on the disk and you will be hightailing it to your next class. Perspiration breaks out on your forehead but is easily dismissed with a waft of your hand. You navigate to the floppy drive and double-click on the game of Tetris. There is time for one quick game. The first block is 1 by 5, your favorite. If only they'd come down like that one after the other you'd have the game in the bag by laying them out horizontally. But it never works out that way. The law of probabilities won't allow it. A book hits the ground and you jump. A lanky-looking freshman picks it up. The title—Differential Equations: Theory and Applications. Smart guy. Most students are only studying multivariable calculus in their first year. Words begin to echo in the back of your mind: there has to be a better way, there has to be a better way.... An odd, misshapen block comes into view. You hate those. They make you lose Tetris every time. A whirring noise emanates from the drive and this time you know it is writing to the floppy. One more minute and your doctored up version of Tetris will have downloaded all of the passwords to the disk. Who'd ever guess this version of Tetris packed such a punch?
A four-sided cube comes down and you ease it over to the left-hand side of the screen. You love those shapes too. On the surface you are just playing a game. Your mouse button clicks and space bar presses are as innocuous as they come. But the real game you are playing is not so easy to see, and at times it feels like Russian roulette. Your thoughts wander to your password-snatching Trojan. The possibility that it was found and that silent sysadmin alarms are sounding in a nearby room is very, very real.
Something's wrong.
Something's not right; you can feel it in the air. The drive should have stopped spinning by now. Your heart goes still. Looking up, you catch a glimpse of a man you didn't notice before. He makes eye contact with you. Fighting the urge to flee, you quickly look back at your screen. You missed placing two blocks. You will not make high score. Your mind begins conjuring swear words without biblical precedent... it has never taken this long before.
The floppy drive finally stops whirring. You quit out of Tetris, eject the floppy, and reboot the machine. You leave the computer cluster and enter the hallway half expecting to be halted by university officials. But none are there. You think yourself silly. You think that there was no way it could have been found. But the reality is that you know all too well how to write a background process capable of catching you in the act and that is what makes you scared. Stepping outside the building, you breathe a sigh of relief in the midday sun. You made it this time, but maybe you were just lucky. Maybe it wasn't in the cards just yet. Like a junkie to drugs, you are drawn to these machines. They speak to you the way they speak to no one else. You put in your time. You paid your dues, and yet for some reason your vision is still shrouded in darkness. There is something they are not telling you. Perhaps it is something they don't even know. It is a question that nags at you like no other, and you sense that the answer lies hidden somewhere within the deepest recesses of your soul, somewhere out of sight and just beyond your grasp. There has to be a better way.
Shortly before sundown that same day...
The dull roar of thunder reverberates somewhere far off in the distance as menacing storm clouds roil in from the west. They exhibit all the signs of a true nor'easter and threaten to engulf the entire city of New Haven. You swear you just felt a drop of rain hit your left shoulder. Reaching down, you feel for the disk at your side. The floppy is still there, its presence reassured at the touch of a thumb. The data it contains is dear to you, and you'll be damned if you're gonna let a little H2O seep through your denim pocket and claim your catch of the day. So you decide to pick up the pace a bit.
The path you follow winds in and around, gently sloping downward as you go, eventually leading to a clearing that overlooks a stand of maples. The trees are enormous and have stood here for ages. At their center lies a lone apple tree. It is dwarfed by the older trees and is helplessly sheltered under a canopy of leaves. Having sensed your unexpected approach, a nearby squirrel dashes for the safety of a nearby tree. Before reaching the trunk, it fumbles over an apple and sends it rolling along the ground. The fruits around you give off a racy odor, a telltale reminder of the approaching change of season.
Had it not been for the disk, you would chance a brief pause underneath the eaves to contemplate greater things. Physics lectures always left you spellbound regarding the mysteries of the world. It was the dream of being struck in the head by a falling apple that guided you to this school in the first place, a dream that you summarily dismissed upon meeting your brilliant roommate. He is a National Merit scholar and received 1580 out of a possible 1600 on his SATs. The deduction was in the verbal section, and you always attributed it to his difficulty in comprehending the human condition. On many levels he is more machine than man, yet his inference engine is second to none. Physics is his second language and he speaks it fluently. You abandoned the idea of majoring in physics since the thought of taking the same classes as he was too much to bear, and since he had an uncanny ability to make you feel stupid without even trying. Answers to scientific problems just came naturally to him. Your hacking obsession combined with a thoroughly tenderized ego would do little to help you finish school.
A gust of wind billows through the trees. The limbs creak and sway in response, causing rain droplets to roll off their leaves. The water splashes onto your face and exposed arms, causing you to start. You realize that you had zoned out completely and had lost all track of time. Your eyes had stared off into space, fixated on some solitary trees, and subconsciously absorbed the surrounding scenery. You shrug in spite of yourself. No use in crying over spilled milk. Your true path has yet to be determined and there is no reason to worry about it now.
You shift the weight of your backpack to your other shoulder and leave the small wooded area behind. As always the students took Prospect Street back to Old Campus while you ventured along an overgrown yet shorter route, preferring to take the road less traveled. Hypotenuse action your roommate called it. Over time you discerned the shortest route between the Sloane Physics Lab and your dorm and it took you through more than one private yard, not to mention a vast cemetery. It saved you an innumerable number of backaches to be sure. Take aside any science student and you will hear the same tale of woe. The cumbersome textbooks are murderous to haul and the university couldn't place the science buildings at a more remote location if it tried.
The Payne Whitney Gymnasium looms ahead, shadowed by the black storm cover above. Were it not for the parked cars and street signs, the darkness could easily lead one to mistake it for a castle. Gulls from the nearby seashore circle above the parapets that line the rooftop. Some dive and soar, some pick up speed, and still others hover in place in blatant defiance of the wind. Nightfall descended prematurely on the city, and what had been just a few droplets of rain minutes before has turned into a veritable deluge. A small pack of students run through the stone archway at the base of the gym with newspapers outstretched overhead. The brunt of the storm is upon you and rainwater quickly seeps into every quarter. You break into a sprint down Tower Parkway in a last-ditch effort to keep your data dry.
The torrential rain pummels your body in sheets as you approach the backdoor of Morse College. You pass quietly into the building under cover of dusk and enter the underground labyrinth of steam tunnels and storage rooms. The humdrum of washers and dryers from a nearby laundry room fills your ears. You take a brief moment to wring what water you can from your clothing. After regaining your composure, you head down the narrow hallway and pass alongside the laundry room. It is empty and devoid of movement, save for a loose ball of lint circling beneath a ventilation shaft. You continue along the corridor towards the small staircase at its end, leaving a puddle of water with each passing step. A steam release valve hisses as you pass it by, only to be replaced by the distant clamor of trays and dishes. The student body has assembled in the Morse cafeteria for the high-quality food service afforded by the university. It is the early part of dinner hour and the thought of eating couldn't be further from your mind.
You fish the keys out of your pocket as you gain the steps to your floor. If your roommate is in he'll probably give you a hard time about tracking water inside, and rightfully so. You open the door and swing it wide, revealing the darkened room beyond. He's out, probably studying in the science library as usual. You pass through his room and into yours, opting to leave the lights out for fear of ruining the picturesque atmosphere. With the toil of the long trek behind, you ease your backpack to the ground and rest at the foot of your bed. You suspect that he'll be gone for the better part of the evening.
It is nights like these that you live for.
A momentary flash of lightning illuminates every darkened corner of the room. You are not alone. A woman stares at you from across your bed. Her eyes are as cold as ice and she has daggers at her sides, drawn at the ready. Li could lunge at you at any moment. It is perhaps one of H. R. Giger's most beautiful yet grotesque works of art ever, and you purchased the poster for twenty dollars at The Forbidden Planet in Manhattan.1
Is she man or machine? Does she need blood or electricity to survive? Perhaps she needs a bit of both. No one really knows of course, no one except H. R. Giger himself. But the purpose of the metal sheaths is clear. They were carefully designed to extract every last drop of blood for her consumption. Her face is paradoxical: it is clearly frozen in a state of suspended animation, yet her eyes are seeing and behind them she is actively calculating. Li has all the makings of perfection: the memory capacity and precision of a supercomputer, the ability to reason as humans do and perform modus ponens, yet exist free of fear and pain and want, with the life expectancy of a machine. There is a definite eeriness about her, for her eyelids are at half mast and she gives off the impression of total boredom, as if it is out of curiosity alone that she permits you to gaze upon her before taking your life.
After a time you get up and seat yourself at your computer, feeling her eyes penetrate deep into the back of your head as you do so. She has watched all of your feeble attempts at becoming one with the machine.
The disk is soaking wet. You pull it out and lay it down next to your keyboard. The writing on the label is smeared beyond recognition. A blow dryer simply will not do, and neither will a tissue since it can leave nasty scratches if sand gets in the way. It will require surgery to salvage it on such short order. You remove the sliding metal door causing a small metal spring to fly out and fall to the ground. The door is warped irreparably, but you will not be needing it again. The two plastic halves separate easily and you gingerly extract the silicon disk from its casing. It has water droplets all over it. They are not too big, but it's a good thing you didn't insert the disk into your drive. You take a dry towel from the bathroom and lay it out on the desk, carefully placing the thin silicon platter on top of it. The water will evaporate soon enough.
You draw your attention to your computer. The power is still off and the pen that you positioned carefully atop the keyboard has not moved. The upper end rests squarely between the “5” and “6” keys and the ballpoint end lies between the “c” and “v” keys. Had it not been aligned as such there would have been hell to pay, and the inquisition would have commenced with your roommate. You remove the pen and flip on the power switch. The desktop appears. The background art reads “Night City” haphazardly spray painted along a worn and weathered wall set beneath a neon sky. The steel rods from the reinforced concrete stand rusted and jagged along the top, making for rough passage should anyone try to reach the ruined building beyond. You dubbed the machine Night City in honor of the cyberpunk role-playing game that bears the same name.2
The protagonists in the cyberpunk genre are a truly admirable lot. They are high-tech lowlifes that challenge authority at every given opportunity, blend in with the crowd, and make commercial programmers look like toddlers playing with tinker toys. The sprawl is their home, a megalopolis formed from the eventual unification of Boston, New York, and Philadelphia. The cyberpunks live on the fringes of society and form a counterculture unto themselves. They know not of greed. They know not of rapacity, and they know not of hegemony. However, these things are not alien to them since they are contended with on a regular basis. They are technologists absolute and embrace mankind's tendency to both make its own problems and later overcome them: deplete the ozone then sell sun block; pollute the air then sell gas masks; trash this planet then move on to the next. It is in science and technology that they believe. Like renegade cowboys out of the Wild West, they serve their own needs in the largely lawless and uncontrollable digital realm. Yet they frequently perform valuable services for the common good, and play a crucial role in keeping the powers that be in check, thus preserving the freedoms that we take for granted. In the end their heroic acts are seldom if ever rewarded, let alone recognized. Such is the divine tragedy of the good hacker. When the megacorporations of the world and their puppet governments wrest control of our lives completely, when they see and hear and record every move we make, when they tell us how we should think and how we should act and what we should buy, who else will there be to turn to?
The terminate-and-stay-resident programs load one after another, creating a line of icons along the bottom of the screen. After the last one loads you reach around the left side of the machine and press the hardware debugging switch. Time to go manual. You type in a command to view the two bytes located at address 0x05DE1940. It contains 0x007E, just as it should. It read 0x007D when you left, implying that you are the only one who booted the machine since you went to class this morning. Your computer is running a number of custom-made Trojan horses, and this is the result of one of them. Every time the machine boots the Trojan increments the counter by one.
On one occasion you rebooted the machine and found that the value had been incremented by two. After a prompt interrogation of your roommate you learned that he had turned on your machine to see if you had some software he needed. When he was finished he turned the machine back off. Paranoia perhaps? Well, call it what you will. You regard it as a simple matter of dotting your i's and crossing your t's. Anyone who walks more than 10 feet inside Night City will set off one alarm or another. There are those who would search your machine, if not for your list of pilfered passwords, then for evidence regarding your other extracurricular activities. Trojans help solve this problem too. Any such person would only find ciphertexts and a machine so riddled with custom-made Trojans as to lead one to wonder why you hadn't written the operating system from the ground up in the first place.
There was no need to admonish your roommate for using your computer. You trusted him more than anyone else in the world with its contents. He had won your respect on the first day of school due to his raw intellect alone. There seemed to be no question he could not answer, no system of equations he could not solve. This applied to everything, from using Maxwell's equations to describe an electrical phenomena to figuring out how computer viruses worked. This had its downsides of course, since there is nothing more frustrating than knowing that whenever you got stuck on a homework problem, the oracle in the adjacent room could produce the answer in a matter of seconds.
The stage has been set. Soon the disk will be dry and you will be able to read its contents. You lean back in your chair and throw your hands behind your head. Ruminations of the previous lecture take over your thoughts. It was a class on the history of physics, and was taught by Professor Klein. He is one of the world's foremost authorities on the subject, and what adds greatly to his lectures is the fact that he even looks like Albert Einstein, although you'd be hard-pressed to get another classmate to admit it openly.
His lecture centered on Neils Bohr, the 1922 winner of the Nobel Prize in physics. It was awarded for his successful investigations on the structure of atoms and the radiation emanating from them. However, as Professor Klein explained, his contributions to mankind far exceeded his status as a Nobel laureate. He was arguably deserving of a peace prize as well for his heroic efforts at saving Jews from Nazi tyranny. Under threat of complete Nazi dictatorship, Bohr held science conferences to bring foreigners to his research institute. Behind the scenes these conferences were really job fairs in which Bohr assisted Jewish scientists to find sponsorship abroad. It was a time in which you were not permitted to leave the country without a foreign employer to work under.
One of the most interesting aspects of the lecture was what Bohr did when the Nazis took to the streets of Copenhagen. Bohr had been entrusted with the Nobel prizes of Max von Laue and James Franck who had remained in Germany. Their medals were successfully smuggled out of Germany at a time in which such exportations were considered to be capital crimes. The Nazis gathered any and all valuables to feed their war machine. The Nobel prizes remained at Bohr's institute for safekeeping, and as Professor Klein explained, Bohr began to worry considerably that the Nazis might take over the lab and find the medals. The recipient's names were engraved on them, and this would not have bode well for Laue and Franck had they fallen into enemy hands.
The thought of burying them was immediately ruled out for fear that they would be unearthed. George de Hevesy, a Nobel prize winner in chemistry, suggested that the medals be dissolved using a powerful acidic solution. They proceeded to precipitate the gold from acid and stored the medals in two separate unmarked jars. The Nazis ended up searching the lab and left the two jars containing the liquefied Nobel prizes alone. The jars were promptly sent to the royal mint in Stockholm to be recast as soon as the war was over [170]. It was a fascinating lecture and it was clear that this was a scientist's solution to a scientific problem.
You found any and all techniques that can be used to outsmart others fascinating, especially when it involved outsmarting evil tyranny. But how can this idea be extrapolated from the physical realm to the digital realm? You glance at the floppy drying next to you. How can we hide the Tetris Trojan from prying eyes? The way to do so is not clear at all. In the next instant a thought occurred to you. The salient aspect of the Bohr-Hevesy approach was that the gold was effectively melted to assume the same liquid form as the acid. The acid and gold were then intertwined at the atomic level, leading to an apparently worthless liquid. A separate process could later extract all of the Au atoms. This process could be repeated ad infinitum. How can a virus be seamlessly integrated into its host? One certainly cannot dissolve an assembly language virus. After all, this is the digital realm we are dealing with.
Given a high-level programming language J that can be decompiled, the solution is simple. Suppose that the host is written in J and suppose that the virus is written in J as well. The virus exists in compiled binary form, but totes around its J source code as well as a compiler and decompiler if needed. When the virus decides to infect a host, it decompiles the host. It then inserts its own viral source code into the host source code. The resulting infected source code is then compiled and saved, replacing the old program in the process. The virus ipso facto adheres to all of the compiler conventions of its host.3 Depending on what compilers are available, the virus could be made to conform to the register and calling conventions of a gnu J compiler, a Microsoft J compiler, a Borland J compiler, and so forth. This would make the virus more difficult to detect. Of course there is ample room for improvement. It would be nice to be able to infer and subsequently mimic the high-level language programming style of the host program. You glance over at the floppy lying next to you. It is finally dry. This research topic will have to wait for another rainy day.
What the disk needs now is a new home. You pull open the top drawer and pull out a previously dismantled floppy. It had been prepared for just such an occasion. You set about reassembling the disk in its new housing. Moments later it is ready. You insert it into the drive in eager anticipation. The resident operating system mounts the floppy without a hitch. The file system properties have to be adjusted on the password file since the file was designated as invisible. You copy it onto your hard drive and eject the disk. After double-clicking on the file you find that it has 143 login/password pairs.
Presto.
When left to their own devices people choose the funniest passwords imaginable. This holds especially true for college undergraduates:
Login: pc541
Password: JoeIsUg1y
Login: sr412
Password: Pee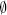 nMe
nMe
Login: ds912
Password: SnakeH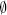 ℓe
ℓe
You double-click on your saved collection and enter the password that is needed to decrypt it. One second later the plaintext file opens up in a text editor. You copy and paste the newly obtained passwords to your master list. Your running total is now 655. Some of the passwords were obtained via your password-snatching Trojan; still others were obtained from brute-force dictionary attacks. The university system administrators were still making the mistake of letting the Unix passwd file be easily accessible.
It was a good catch given that your last visit to the Trojan was only a week before. However, the running total is not really 655. You earmarked several of these accounts as potential honeypots. The most suspicious of all is:
Login: Password
Password: Password
Every time a user logs into a university machine, the user is warned that any unauthorized use is a criminal act and a violation of U.S. law. These honeypots are a way of trapping rogue users since they are easily guessed and grant access to accounts that are under 24-hour surveillance. You surmise that at least 620 of the user accounts should be safe to play with.
Before calling it a day you run your coin-flipping program. You type in 655 and let it flip away, prepared to toss the coin again if it winds up on a honeypot. The result comes up 422. You cross-reference this with your master list and determine that it's probably not a honeypot account.
Login: edc42
Password: m4Tds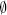 1
1
Tomorrow you shall be edc42 for a while.
* * * * *
The night is young as you step out of the house. In the distance, the Transco Tower stands silhouetted against the skyline. Like a municipal sentry it watches as the denizens of the city slowly make their way onto the streets. You smile in spite of yourself, for on this night you have something very special planned and you doubt that anyone has a vantage point good enough to see that the sequence of zeros and ones on the disk at your side is just a little unusual, a tad bit out of place, and in fact upon closer inspection downright insidious in nature.
You hop on your bike and pedal away from your home. Well, your home away from home is more aptly put. It has been over a year since you last visited your father, and the last time you were in Houston this new creation was little more than an idea on the drawing board. The city takes on a new hue as the headlights and 7-11 signs shed their evening glow. With not a cloud in the sky and no chance of rain, a new feeling begins to grow deep inside. This is the night. She will be free. You hope your due diligence will keep her alive. She will travel to strange lands and traverse hostile environments and will rely almost exclusively on what you taught her to do.
Turning a street corner you head out onto Westheimer. The traffic lights spread out as far as the eye can see, turning from red to green to yellow and back again in steady cadence. A small copy shop appears on the right. Looking inside you see a customer at a computer and a cashier looking off into space. Two people. No bustle. Not a chance. The last thing you need is a proprietor looking over your shoulder watching your every move. You pedal down an access road and jump a curb. Some more distance is necessary. Every mile counts. You traveled halfway across the country with her in tow, and it was important that you see her off safely.
A small shopping center comes into view. It is surprisingly full of cars. You swing into the lot and see a Burger King, a movie theater, a restaurant or two, and nestled in the middle of it all, an enticing-looking copy shop. Chaining your bike to the nearest pole, you scope the place out. Video cameras are mounted fore and aft, a convex mirror hangs over the computer area, there is no uniformed guard, and there is no tape measure along the side of the front door. Half a dozen customers are in line, and the copyists are buzzing around like worker bees. Drawing your attention to the computer area you see three people seated at computers, and another hovering over a color laser printer. It looks promising. In fact, it looks as promising as can be. Those machines don't stand a chance. You get up and walk into the establishment, just another face in the crowd, another customer needing to print out documents. You pass into the computer area and not a single person pays you notice.
As you seat yourself in front of a computer you try to recall how many times you washed the dishes after eating at a restaurant. Zero. Why? It's very simple really. It's not your responsibility. You pay for the food. You pay for the service. Cleaning up after yourself is not your responsibility. How silly would you look if you got up after paying, walked into the kitchen, and said “here, let me help you with those plates” to the employees? They would look at you sideways. Leaving your virus on this general-purpose computing machine is no different than this. The fact that others lack the cranial capacity to see the grime is not your fault. If it spoke to them the way it speaks to you then they'd be aware of her presence. But the privileged are few in number.
A message on the screen informs you of the rate: Ten cents per minute. The blinking caret asks you for your name. It is waiting. You give it one stochastically chosen from among the most frequent names in America: John. This machine is no longer for hire. It is temporarily yours, to do with as you will provided that it remains functional enough for the next customer. But most importantly, it must remain an intact vehicle for making the corporation money. That is what really matters in America. It will be so, you say to yourself, as you pull out the disk. It will be so.
You glance at the floppy in your hand and question once again your insatiable need to spread digital diseases. This is the wrong thing to do. Yet there is no helping your compulsion. You are diseased, but there is solace in the fact that your disease stems from the morally ruined society you live in. Greed begets punishment.
From idea in the back of your head, to scribbles on a drawing board, to mnemonics in an ASCII file, and on through the assembler your creation has traveled. You trained her on every antiviral program you could get your hands on. She bypasses them all. You click on the control panel and notice that the machine is running a virus shield. The shield consists of operating system hooks to file system interrupts that analyze their callers for suspicious behavior. Not a problem. Your virus already knows the location of the native interrupts needed to avoid the patches altogether. She has all the needed ROM addresses stored in her internal circularly linked list. You wonder how long it will be until she forgets them in lieu of newer ones, ones that have yet to be chosen by the computer manufacturer. You wonder if she will even live long enough to see that day. She is so clever, you think to yourself as you insert the disk, and fastidious too. She will never get a byte fatter than she already is.
A guy sitting down at the machine next to you looks over his printout. You make out a pie graph on it that seems to reference budgetary plans. While he is busy there making money you get busy running your infected version of Tetris. You spent well over a year designing her, calculating her cold-hearted offensive and defensive mechanisms.
... and now it is time to bring down the machine.
Seconds later a u-shaped block comes down the screen. Bingo. No system crashes and no antiviral warnings. She is free. She moved into her new home in the boot sector. But she has yet to leave her burrow and survey her surroundings. Experience has shown that crashes are not uncommon in these copy shops, so you hit the restart button knowing full well that the accounting software will not lose a second of billing time. As you eject the disk you look to the right and notice that the line has gotten even longer. The guy next to you signs out and heads to the back of the line to pay.
The machine boots up without a hitch. You see your name John on the start screen and click on the button labeled continue. Everything seems to be going smoothly. You take the liberty of running some of the resident programs: Photoshop, Microsoft Word, Acrobat reader, and a few text editors to boot. They all put on a few pounds. But who's going to notice? Infecting these programs manually is a good measure against any futile attempt to remove the virus. She's flying high, having beaten the heuristic scanners to the punch. She rerouted the interrupts first this time and will never be on the defensive on this particular machine ever again.
The clock in the lower right-hand corner of the screen reads “00:12.” Twelve minutes. That's only one dollar and twenty cents. It was worth it. You sign out and head to the back of the line. A lady at the front of the line is unhappy with her glossy printouts. They are sprawled out all over the counter and she is taking forever to resolve the issue. The people behind her are visibly agitated.
You contemplate the future of your creation. Will she survive? Your gut tells you that she will. She has to. She has so much going for her. But how will you know how she fares in her new world? She'll never write. She'll never call. If you're lucky you might even hap upon her some day. Even then she won't tell you anything. You won't know how many children she has, or how many children her children have, and so on.
The lady reaches for her purse and pulls out a checkbook. Unbelievable. And you thought it was the information age. She finally takes her bag of glossies and leaves, to the relief of all. The line moves silently forward.
The problem with your creation is that she is an open book. Anyone can read her and with any luck she'll be notorious enough that lots of people will. You could have trained her to tell you of her exploits, but it is not clear how this could have been done in such a way that she would tell you and you alone. Ideally you would like one of her offspring to tell you some of the names of the infected machines and the order in which they were infected. You contemplated using Intel CPU IDs and IP addresses as unique identifiers to record the path that she and her progeny takes. However, one obvious problem with this approach is that the data could easily take up too much space in the virus. The real problem is the sheer stupidity of it. You may as well hand the Feds a road map to your house and draw a target on your back since it would have the same effect. Even encrypting the path with 3DES and storing the key within the virus would do little to hide the path from trained eyes.
A less detailed approach would be to divulge only the number of infected machines instead of the names of the machines and the order in which they were infected. This could be accomplished by giving her two generation counters. The idea is simple. A counter i would be included in the virus that would initially be set to a randomly chosen value r. Each time a virus has a child it increments i in the child by 1. For example, if the first virus had 8 offspring then they would each contain i = r + 1. Each of their children would have i = r + 2 and so forth. Another counter j would store the cumulative number of children that each forefather had. The value j would initially be set to a random value s. After the original virus had a child it would store j = s + 1 in itself and in the child. After the original virus had a second child it would store j = s + 2 in itself and in the child. The purpose of using the random values r and s is to throw off antiviral experts as much as possible, since you know these random initial conditions and they don't.
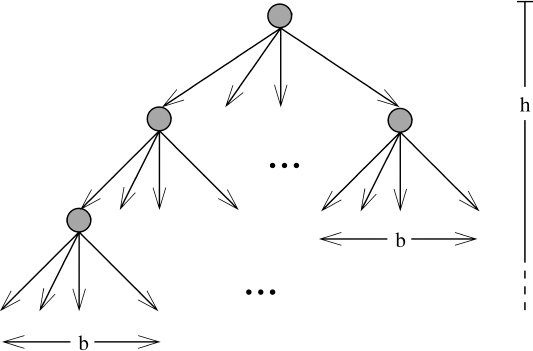
The idea was to try to obtain a future copy V of the virus. In it would be values for i and j. The distance from V to the root of the family tree is h = i − r. The average number of children per forefather of V is b = 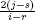 . So, a very rough estimate4 on the number of existing viruses is (bh+1 − 1)/(b − 1) (see Figure 1.1). This is the number of vertices in a complete tree in which each parent has b children. Although the accuracy of this mechanism is highly suspect,5 it would nonetheless be fun to obtain these values later on....
. So, a very rough estimate4 on the number of existing viruses is (bh+1 − 1)/(b − 1) (see Figure 1.1). This is the number of vertices in a complete tree in which each parent has b children. Although the accuracy of this mechanism is highly suspect,5 it would nonetheless be fun to obtain these values later on....
The person at the front of the line pays for some printouts and then motions towards the computer area. The cashier nods, says something unintelligible, and then points towards the computer you just left. The customer then walks over to it and sits down. For a moment you freeze. You didn't expect it to be used while you were still there. Suddenly the line seems way too long and your aggravation level rises a notch. It will be cool, you tell yourself. It's under control.
You thoroughly contemplated the pros and cons of including the counters while the virus was on the drawing board. The cons outweighed the pros. Like any viral outbreak the epicenter paints a strong picture of where and when the infections commenced. This was the reason you waited. This is the reason you are here in Houston. You shudder to think of the information you would give to antiviral analysts if you released it at school with the counters. The counter values would be low in the viral samples found on campus and the values would increase as the viruses moved further away, plus or minus the noise introduced by FTP transfers and the like. No, the decision not to include the counters was a good one. It would give the enemy even more information than it would give you.
The person in front of you pays the cashier and walks away. You approach the counter with cash in hand. The cashier pulls up some information on the computer and presses the screen once. A paper begins printing out. He hands the sheet to you. It reads your fake name, your alias du jour, John. He will get a good look at your face but there is no helping it. You pay the balance and take the receipt. As you head out the door you pause and glance back at the machine one more time. You silently bid her farewell, and pray that she will go forth and multiply.
Figure 1.1 Estimated number of viruses in the wild
While heading over to your bike, a familiar feeling comes over you in a wave. There must be a better way, you think to yourself. There has to be a better way.
Nine months later...
From within the darkened confines of your dorm room you sit and contemplate your creation for the thousandth time. Your drawing board is filled with pseudocode, directed graphs, and the names of pertinent operating system calls. Despite your efforts the battle you waged is not going as planned. Not at all. You push back on your easy chair, causing the padded leg rest to rise up to your legs. Throwing your hands behind your head, you stare at your war machine, split down the middle and dissected in gross detail to enable careful analysis. Your agent was sent off into the wild blue yonder with tools that now seem to be woefully inadequate, for not even a whisper of her exploits has found its way to your ears.
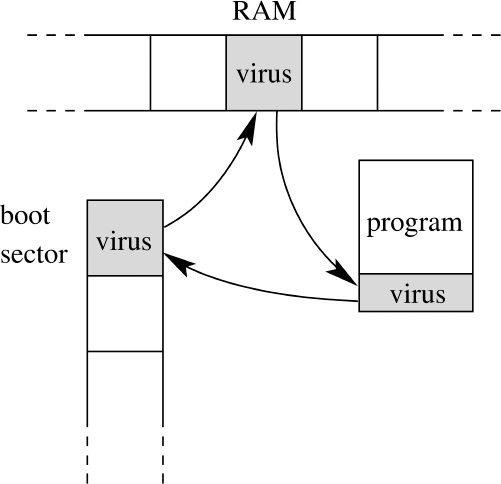
In many ways her design followed a tried-and-true methodology: she is a multipartite virus that, like several parasitic organisms, has three phases of existence (see Figure 1.2). She started out life in a deliberately infected executable. From there she migrated to the boot sector. While in the boot sector she copied herself into RAM. Finally, when in RAM she hunts down potential host applications and infects them, thus completing the lifecycle.
She was a prototype and nothing more, you think to yourself in a feeble attempt to dismiss her apparent shortcomings. A moment later, you feel ashamed for even thinking this. She's done nothing to warrant being belittled so. Perhaps separation anxiety was getting the best of you, for no matter how hard you tried you could not shake the feeling that part of you was missing.
You draw your attention to the top of the board and take note of the words “polymorphism engine no. 1.” She has no routines to modify her own byte representation but they've been in the making for some time. After an entire week of bug hunting you finally figured out why your first polymorphic version kept crashing with a bus error. It turns out that the CPU uses an instruction look-ahead cache and was executing the ciphertext when you thought it was executing the decrypted code. Even the assembly level debugger led you to believe that the CPU was executing the decrypted code correctly. Silly computer manufacturers, they should know that a program often likes to change itself while it runs. The solution? Flush the cache. There are a variety of ways to do that.
For a moment you feel an extreme urge to erase everything related to polymorphism on the board. In all likelihood polymorphism would not help her spread, since in cleartext form she already bypasses every antiviral program on the market. Making her polymorphic now would be like teaching her to run before she could walk. Deep down you know she can walk. She should be all over the place by now and should've been found.
To ensure that she would spread rapidly, she was designed to handle battleprogs and memory resident antiviral programs. Battleprogs is the term you use to refer to applications that perform integrity checks on their own code. These battle programs are written with the foresight that one day they may become infected by a virus or Trojan horse. Once an application is compiled, it can have integrity checking code built into it by the developer. One way of doing so is by attaching a beneficial Trojan horse to the program. This program may be structurally similar to malicious Trojans but serves to verify the integrity of the host. To create this beneficial Trojan the developer first computes a checksum on the compiled binary using a one-way function, for example. The input to the one-way function can be the body of the host concatenated with the integer representing the length of the host and the attached Trojan. The file length may be found by making an appropriate file system call. The resulting checksum is then stored within the beneficial Trojan.6 When the executable is run the Trojan gains control first. It then recomputes the checksum and compares the result to the checksum that stored within the Trojan. If they don't match then the Trojan assumes that the application has been tampered with and refuses to send control to the executable. The Trojan can also perform the checksum on the copy of the host that resides on the disk drive. The original executable along with the beneficial Trojan forms a battleprogram that acts as a whistleblower against unexpected changes.
Figure 1.2 3-Phase multipartite virus
Over time you encountered many battleprogs and taught her how to handle them. When she is in her memory resident form, she looks for currently running executables to infect. She only infects such programs immediately after they terminate. When she runs from within an executable, she infects the boot sector if it isn't already infected. Following that she removes herself from the host executable in memory and on disk. This way, when the host gets control, the host is in its pristine shrink-wrapped form. As a result, if it computes a checksum on itself then it will always match. It will match because the program is in fact no longer infected. You carefully measured the overhead of this approach, and it has proven to be unnoticeable to the naked eye. To implement generation counters on top of this, it would be necessary to have the counters only record the number of boot sector versions of the virus. This is necessary to avoid overinflating the counter values, since the virus copies itself to and deletes itself from executable programs.
The first rays of dawn pierce through the darkness of your dorm, passing over your head and onto the drawing board beyond. You get up and approach the window. The courtyard below is completely deserted. In a matter of hours dreary-eyed students will be bustling to class, and you will be a sleepless walking zombie among them.
You detest daybreak, for it is a pale reminder of yet another night spent working on your creation, another night not working on quantum mechanics or signal analysis homework. How you've managed to keep your GPA up given your hacking obsession is a mystery. No doubt part of it has to do with your electrical engineering study group. The four of you work on everything together, and when your collective minds are brought to bear on the written exercises, you usually fare quite well. The problem is, the Electrical Engineering department has compensated for such study groups by dishing out impossible assignments. Every problem set contains at least one problem that is so elusive that it leaves the entire group dumbfounded. Lately, your contributions to the problem-solving effort have been lacking, and it hasn't gone unnoticed. If you keep going at this rate one or two members of the group are certain to defect, thus bringing an end to your precious scholastic support network. It is expected that each person show up with at least two or three solutions to share, even if they are the solutions to the easiest exercises. This at least provides some measure of assurance that the answers are correct. Last night you didn't open a single textbook. They are sitting at the foot of your bed, ruefully neglected.
... your sickness is getting the best of you.
Besieged on all sides by feelings of guilt, you react in the only way you know how. You pull the curtains over the window so that the night may continue within. You head over to the drawing board and try to focus on the task at hand. The assembly code at the bottom of the board has recently been incorporated into the latest prototype and can therefore be spared. You pick up the eraser and wipe it away. Workspace is always necessary to solve problems. There is one thing that you know for sure could be hindering her attempts to replicate. It is a problem that has been a thorn in your side for over a year. You crack open a new can of soda and sit back down in your chair.
When your virus encounters a new computer model that hit the market after the virus was released and when the computer is running memory-resident antiviral software, your virus can't get in. The problem is that these programs patch critical operating system routines that your virus needs to call in order to replicate. The patched code analyzes the caller for suspicious features shared by many viruses, features that your virus has. When found, the antiviral software alerts the user to the presence of the virus. If the original operating system vectors are known, then the virus can bypass the antiviral patches entirely. But, on new machines these vectors are not known. Even though future operating system routines are based on previous ones, the vectors cannot be safely guessed. The computer manufacturer will inevitably debug, reorder, and add to the existing operating system routines, thereby mucking with all of the offsets.
Furthermore, manually incorporating all of the needed proprietary code into the virus and making calls directly to the IDE driver would make her look like the circus fat lady. No, there is no way to solve this problem adequately. But at least she knows her limitations. She knows when this situation arises, and she knows not to act. If there's one thing that these antiviral sentries lack it's the element of surprise, and she knows when they're watching. Your fielded avatar is designed to learn these needed interrupt addresses. If she chances upon an unguarded machine, she will teach herself the needed vectors. She will remember them henceforth and whence not in her circularly linked list of memory cells, only to be forgotten when the machine's era comes to pass.
You glance back at the newly created space on the drawing board and take a swig of the soda at your side. There might be a way, you think to yourself. But deep down your gut is telling you that this problem is different from the others. It doesn't feel the same. It is mired in operating system theory and specifics. On a more technical level there might be a solution, but it would most likely involve different assumptions regarding the internal workings of the operating system, and therefore assume a different underlying operating system altogether. In the end it would not help in constructing the real-world juggernaut you so desperately wanted to create.
You decide to put the problem on hold for the moment and head out to the local computer cluster. When you arrive you see two dreary-eyed students. One is engrossed in an AutoCAD program at the far end of the room and the other is waiting impatiently by the laser printer. He is clearly at the end of an all-nighter since he's in a robe and his hair is standing on end. You recall programming your creation once for three days straight. The last twelve hours were marked by hallucinations and tingling sensations and you didn't call it quits until you observed a stapler crawling towards you on your desk. Such has been the commitment you have made to her. You seat yourself at a terminal and log onto the network. The message of the day appears on the screen:
“MOTD — A computer virus has been discovered at several colleges and universities along the west coast . . . The CERT coordination center has issued a warning and a virus definition has been made available. We are asking all students and faculty to perform updated virus scans as soon as possible. The virus is set to activate on. . .”
Like visors on a horse your peripheral vision falls away until all you can see is the message. Blood accelerates through your veins and fear clenches your heart.
She has been found.
She has been found and not just at one place, but at several. You want to delete the message of the day. You want to erase it from every computer in the entire university. You want to delete the virus definition and take the advisory down from the CERT web site. It's all too real. You glance over your shoulder. The other two students are oblivious to your plight. Given the enormity of your discovery it seems hard to be believe that this could be so. Never before has the virus seemed as much like a disease as it did now, because unlike before, it cannot be stopped. It cannot be contained. It is out there and it will no longer heed your call.
It took a day to sink in, and yet another to stop worrying about SWAT teams and unmarked vans. Then a new feeling began to grow deep inside. There was no doubt about it now. She had been snatched up and spirited away to an antivirus lab. You envision her digital form lying bare on an operating table with her midsection sliced open, her insides succumbing to the machinations of skilled surgeons. With tools that bore and cut, she would be systematically dissected and learned. How utterly exposed and violated she must feel right now. Multitudes of her offspring were now destined to perish, for nothing of what she had would remain hidden. They will be caught dead in their tracks, quarantined, and ultimately destroyed. But she still has one major advantage; there is power in numbers. Her replication will be exponential and this alone will secure her a place in the digital food chain. She may even reign supreme, for a time, on the proving grounds that is information warfare.
Deep down you know that she will multiply while this operating system version, and possibly the next one remain on the market. You nostalgically recall a game of cat and mouse you played with her while she was growing up. She initiated the game, of course, and it lasted for weeks. For some reason the computer in your dorm began showing a slow but marked degradation in CPU performance. It wasn't anything that could be quantified at first. But something just didn't feel right. The machine's speech was sort of slurred. After a while the pause between sentences became unbearable and your suspicions codified into a hypothesis: You were the victim of a virus yourself. The thought was both embarrassing and at the same time exhilarating.
The more you thought about it the more sense it made, and so you downloaded all of the latest virus definitions. The number of infected programs on your machine came up nil after the virus scans. Hmmmm. Something else then, you thought to yourself. You decided to pull out the microscope and tweezers and analyze the assembler that you used to assemble your virus. Your mouth nearly dropped to the floor when you noticed not one but five viruses hitching a ride at the end of the binary. They were all earlier prototypes of your virus. Over time the assembly language alterations had affected her offsets, and she managed to slip past you as a result. She replicated right under your very nose and you of all people were none the wiser. She had truly become a thing of beauty.
As a result of her escapade, you revised your software development practice to include a stiff regimen of custom antivirus scans. It was a simple task to come up with virus definitions for your own creations to prevent this from happening again. It was ironic how useful the antiviral software turned out to be in the virus software development process.
Overall it was a valuable lesson she taught you. The day the cat-and-mouse game ended was the day in which she started showing her true colors. The machine ran at full speed and she spread with a virulence heretofore never seen. Her ability to slow the machine to a standstill without being noticed by trained eyes was testament to her readiness to leave the nest, and she did very well for herself in the end.
* * * * *
One sunny afternoon in a small office in midtown Manhattan three employees meet to discuss the progress of a software development project that is lagging behind schedule. It could have been virtually any software company in any city and the situation would be the same, only the names would change. . . .
A young, somewhat disheveled software developer shifts uncomfortably in his chair with a look of utter consternation on his face.
“So you want us to rewrite the entire system so that all of the commands are in ASCII,” announced the programmer aposematically.
“That is correct, Brian,” replied the man at the head of the table. “Something might go wrong with the client/server software and they may want to have a look at it. After all, it is theirs. They paid for it.”
It was an asinine explanation for making such a major last-minute change to software that is already functional. There is no way in the world the client would find and read the obscure log file. The three of you are more likely to be hit by a meteor during this very meeting. Brian shoots a glance at you from across the table and you nod knowingly.
“But if the messages are in ASCII then they will be five times larger than necessary,” you reply.
Rajeev casually glances at his Rolex, implying that he has better things to do than argue with his software developers. He folds his hands in front of him and considers carefully his response. You have only been at the company a short while and deserve a better answer than this. He turns to address you.
“I know this, of course. I have developed software in the past as well. What is important is that we have an intelligible audit log of our system. If something goes wrong we may have to ask them to send us the log file,” said Rajeev in a matter-of-fact tone of voice.
His response this time was closer to the truth. Yet in the end there was no point in arguing with the managing director. The bottom line was that Rajeev cofounded the company, he won the contract, and you and Brian were here to fulfill the contract however he saw fit. Rajeev knew how to keep things running smoothly, despite the inevitable bumps in the road. The truth was that he wanted the commands for the protocol to be in ASCII for human resource reasons, not technical reasons. The companies' software development team was almost exclusively college interns. The average turnover rate for team members was only six to nine months. This was hardly enough time for a neophyte to learn the protocol and then extend it before leaving the company. By making the protocol messages ASCII instead of binary, the protocol could be learned, monitored, and debugged more easily.
“Okay, Rajeev,” you concede. “I'll make the necessary adjustments and replace the enumeration constants by ASCII strings by close of business Monday.”
The first two months on the job had been a crash course on software reality as opposed to software engineering as you knew it. The company cared more about your commenting style, indentation style, and variable and function naming style than anything else. It was as if everything you learned in school meant nothing, no research into using the best algorithms and no attention paid to running times. The only priority was to make the code readable, get it done on time, and try not to let it crash on the user.
Rajeev's cell phone rings and with a wave of his hand he brings the meeting to a close. You and Brian head back to your desks.
“Well, that went as expected,” said Brian.
You nod in agreement. The company had a way of taking a brainless task and making it even more so. But for the time being it is looking as if you might actually have something to look forward to. Last night you put the finishing touches on your latest piece of software and rolled it out, so to speak. It now resides on every machine in the company, and is ready to do your bidding. Like a djinni from a bottle the program is prepared to grant your every wish, no questions asked, and without failure. Only this djinni gives out more than three wishes.
Your job had been to develop the client/server suite from scratch. The server ran in the background and processed requests made by remote clients over the local area network. You fulfilled your end of the bargain, but found the final product to be woefully inadequate for your personal needs. After all, the server had little if any power over the machine it ran on and was not amenable to being camouflaged in any way, shape, or form. So, you took the liberty to develop your own client/server suite. The key difference being that your server is a Trojan horse that resides deep within the heart of the operating system. It sends and receives packets at a subterranean layer of the network protocol stack that is high enough to facilitate rapid software development, yet low enough to keep the Trojan's activities from drawing unwanted attention.
With only two other developers in the room you decide that it's as good a time as any to test-drive your new client/server suite. You eagerly fire up your client program. Your senses are piqued and through the corner of your eye you take note of what Brian is doing next to you. He is an avid object oriented programmer and can run circles around you when it comes to writing anything in excess of 20,000 lines. You've got to play it cool this time, you think to yourself, cool as school. These are no run-of-the-mill computer users about you. These are young and alert programmers and unlike the people in marketing you're always a bit skittish about messing with them.
You click on a button and row upon row of computers appear on the screen. They are interconnected by a twisting array of wires and are undulating with a servo-electronic pulse that can only come from something truly living. Graphical user interfaces always add an extra panaché to rogue software and are reminiscent of the imaginings of many cyberpunk novelists. Brian is too close to your machine to be a guinea pig so you decide to prey on Adrian instead. You move the mouse pointer over his machine and click on it. His machine slowly rises above the rest. Adrian has his back to you and his face is buried in a book. It will be his undoing.
Enter your command for this machine, oh great one:
For a fleeting moment you experience a burst of euphoria and power, but then just as quickly as it came on you lapse back into the reality of your peon status at the firm. If nothing else you'll get your kicks. You click on the button labeled “hardware interrupt.”
and which flavor of interrupt will you prefer, oh great one?:
1. key strokes
2. N system beeps
3. N deletes
4. eject CD
5. system reboot in 120 seconds
Cooing inwardly at your creation, you rub your hands together in eager anticipation. Your Trojan is about to test its wings. Glancing back over your shoulder, you see that Adrian's face is still buried in his book. It is unclear whether it's a trade book, a software manual, or one of those Japanese animés he's always reading. He is an exceptionally good programmer and to pull one over on him would be a major accomplishment. He's also a really great friend, but that is beside the point. You are currently engaged in an important military exercise and must not let yourself get sidetracked by unimportant details.
Knowing that Adrian may turn his attention back to his screen at any moment, you quickly decide to do option 1. He's currently editing the C source code to a massive program and you know that he wouldn't draw his attention away from his screen unless his program was syntactically correct. You also couldn't help but notice that his cursor was at the end of a statement in main().
A most excellent choice oh great one, and what string shall I conjure?:
You enter the text,
for(;;);
and hit the carriage return. The characters “for(;;);” spring to life on Adrian's screen. You immediately quit out of the client program. Unable to contain yourself, you proceed in the only way you know how to avoid entering into hysterics. You pick up a book, open it to a random page, and bite down hard on your free hand. Pain was the only way to contain the laughter growing inside. The server worked like a charm.
Using the reflection in the corner of your screen, you perceive the events behind you as they unfold. Adrian hits a few keys on the keyboard, drops the book to his side, sits back in his chair, and waits. He waits as it saves. He waits impatiently as it compiles. He then waits some more as it links. As usual, this alone takes so long that he shifts his position to hunch over the keyboard. He rolls his fingertips on the table in rapid succession and waits some more as it runs. He waits, and waits, and waits.
“Come on then!” Adrian shouts at his screen.
Adrian finally stood up and threw his book against the wall, cursing wildly at his screen. The entire ordeal promptly drew the attention of Brian, who asked him what his problem was. Adrian replied using every four-letter word imaginable that his machine was busted. He even threatened to throw it out the window. Fearing that Adrian might be a bit too tightly wound on this particular occasion, you decided to lend some moral support. You put on your best poker face, spun around in your chair, and expressed your deepest concern for Adrian's predicament.
Like it or not, Adrian was forced to experience the halting problem firsthand. The act of doing so left him quite undone. When Adrian finally found the infinite loop in his source code, the infinite loop that materialized out of literally nowhere, he simply stared at his screen and was unable to utter a single word.
After regaining his composure, Adrian set about trying to determine what had happened. He downloaded and ran the latest antiviral software. He called the help desk to see if the desktop group did anything to his machine. Despite being poorly versed in Intel assembly language, he downloaded a disassembler and tried his hand at analyzing the boot sector. But it was to no avail. In the end he simply could not discern from whence the offending loop came. Being pressed for time, he eventually abandoned the hunt altogether.
In all it cost the company an hour or two of Adrian's time, but the reparations that it made to your job motivation were without bound. You simply could not wait to go to work from that day on. Your djinni was capable of much, much more. It dutifully awaited the arrival packets from your client and processed them in due course. The network packets came in two varieties: data and code. The data packets caused the server to execute predefined commands such as the emulation of keystrokes, and the code packets were executed by the server verbatim. Every so often a truly creative prank would occur to you and the code packets sated your need to perform it on someone's machine immediately.
Yet this particular training drill was but the first of many. Sometime later a similar opportunity manifested itself and you accepted the call to action. Howls and hooting emanated from the marketing division and like a predator to prey your ears perked up....
You look over to Brian, your coworker and soon to be partner in crime.7
“It's bonehead again,” he says to you with that annoyed look in his eyes that can only come from one employee who knows that another is currently getting away with murder.
With Rajeev out smoothing over a client, Eddie took the liberty to play Quake again, as usual.
Eddie is one of those people everyone can do without. There is nothing particularly notable about his skill set and it is not clear exactly what his job responsibilities are. He is simply there. If nothing else Eddie is a master of keeping himself busy. He manages to find things to do day in and day out. Sooner or later every new hire learns not to cross swords with him since he has friends in high places and can make your job miserable at the drop of a dime.
Brian gets up and heads over to the marketing division and you follow him. A crowd of people is standing around Eddie's desk. His speakers are blaring techno-industrial and the blue-green glow of the game is reflected in his eyes. Eddie is consumed by his game. Joining the crowd of onlookers, you notice that he is wielding his favorite weapon, a shoulder-mounted railgun that fires depleted Uranium shells. He rounds a corner to find a battle droid directly in front of him. Before it can react Eddie fires his gun. In a flash of light the weapon sends a shell down the hallway, leaving a spiral of smoke in its wake. It slams into the droid with a horrific puncturing sound. The droid was caught off guard and is sent reeling into the far wall. Its armor plating is badly damaged, but it manages to get up on all fours. It will take another shot to bring it down. Eddie is doing quite well and in a matter of minutes he will beat his high score. It just so happens to be the highest score in the entire company. It's not like he doesn't have enough time to hone his skills or anything.
Smiling inwardly, you excuse yourself to go to the bathroom. As you head over to pick up the key to the men's room, you contemplate your premeditated act. He has it coming to him, you think to yourself. The guy rubbed your rhubarb the wrong way during your first week on the job, and now it's payback time. You pick up the key and head back to your desk. You load up your client program, enter a few commands, hit return, and then terminate the client: Two minutes and counting.
You head back out into the lobby and make sure to make eye contact with some of the people around Eddie's desk. It seems that while you were in the bathroom, Eddie's machine rebooted for reasons unknown. You had the pleasure of hearing every delicious detail about it from Brian, who was as perplexed as everyone else in the matter. For whatever reason the neurons in Eddie's brain never fired appropriately to make the connection that you were never around when the digital boogieman struck his machine. In his mind it was exactly this that exonerated you from his list of likely suspects.
On one occasion Eddie got so pissed he charged into the development room on a rampage to discover the identity of the digital boogieman. He was certain that one of the smart-mouthed developers was to blame. He did it at lunch hour, immediately following yet another attack on his system. He moved meticulously from screen to screen, hoping that somehow despite his complete programming incompetence, he might be able to glean some incriminating piece of evidence. Like a promising lab rat, Eddie eventually learned to save his games often, particularly when he was about to make high score.
But, being the self-appointed sysadmin for your company was not always so easy. On one occasion Adrian came close to finding your Trojan horse server. Way too close. In a last-ditch effort to conceal the presence of your malware, you laid out a series of explanations to divert his search efforts. It succeeded, and Adrian ended up analyzing benign sections of the operating system.
In all, the client/server suite performed very reliably, but this did not prevent the overall series of occurrences from drawing the attention of upper management. In a rather bizarre turn of events, you were asked to investigate the suspicious string of events at a team meeting. Your were the resident security expert and so Rajeev figured you were the man for the job. He would probably reimage everyone's machine before outsourcing the problem to another company. Rajeev liked to save money that way. The irony of the request hit home and so you decided that you'd better cool down a little. You thought about it but could not get yourself to take down any of the rogue servers. So, you decided to simply maintain a lower profile instead. You disciplined yourself not to reboot Eddie's machine for the heck of it, but rather only rebooted it when he was asking for it.
The game suddenly came to a grinding halt when one day you found that you could no longer get to the desktop on Eddie's machine. Facing the screen, you looked at it in amazement. It had nothing on it save for a modal window that prompted you for a password. It seems that Eddie was trying anything and everything to keep the boogieman off his machine. Luckily Eddie's machine was free for you to use since your current task involved software testing, and it was important that the final product be compatible with Dell machines. Eddie had the misfortune of having the only Dell in the company.
Without arousing any suspicion, you sat at his desk during lunch hour and tried to break in. You tried everything you could think of but it was to no avail. The machine was locked down. The floppy you held and the Trojan it contained could not be executed, and you suffered an infuriating defeat. Before leaving for the day, you took the liberty to scour the shelves in marketing for the software that successfully thwarted your attacks. Sure enough, the offending product was located not five feet from Eddie's machine. It was a shrink-wrapped disk-locking program. You plucked it off the shelf and read the back of the box.
“with our patented technology... keeps unwanted intruders at bay, allowing your data to remain safe from modification and prying eyes.”
Raising a brow, you conceded that you fell squarely into the category of unwanted intruders. You placed the box back on the shelf and left work seething with animosity.
That night you contemplated the day's events. Having never played with a disk-locking program before, you were left to hypothesize how it worked. While pondering how such a program could render your efforts so ineffective you reached the stark conclusion that all attempts to break in would be futile.
The following simple design would be good enough to thwart all of your attacks. A small partition could be created on the hard drive next to the resident operating system. The partition would be populated with a small boot program that is capable of sending control to the resident operating system. The file system or critical portions thereof could be encrypted using a cipher like 3DES that uses Eddie's password as the key. His key would therefore be needed to decrypt it and the key would not be stored anywhere on the disk. Furthermore, a checksum C could be computed by running Eddie's password through a cryptographically strong one-way hash function. The value C would be stored internally in the new partition. When the computer reboots, the partition program would get control first. It would prompt you for the password, hash whatever you enter, and then compare the result to C. If they matched, it would then decrypt the file system using the password you supplied. If they didn't match, then it would tell you that the password was incorrect. When implemented properly you could stare at every single bit on the hard disk and still have no clue what Eddie's password is. The method effectively cripples the underlying file system and only when it is uncrippled is it possible to install rogue software.
Whether or not this is the way Eddie's program actually worked was immaterial. It did not change the fact that it could have been written this way. So, there is no reason in theory that you should be able to get back on his machine. It was bad enough that a shrewd sysadmin could easily track your activities when you ran the client. This is the same problem that you faced when you accessed the password-snatching Trojan back at school. What this situation spelled out was much worse. It meant that in order to hack into Eddie's machine it was not enough to be the world's greatest hacker. You had to be the world's greatest cryptanalyst.
In the end Eddie's machine succumbed to a Trojan horse attack that commenced from a floppy inserted into his machine while he was present. He was the one who did the honors by double-clicking on the infected program, and so he was the one who let you back into his machine. From then on the servers paid particular attention to all keystrokes that the users entered into their machines and the lockout never occurred again.
However, the final victory did nothing to ease the mental repercussions that ensued. The initial failure was bitterly tangible and wore on your ego. The fact that someone like Eddie with no understanding of computer security whatsoever could simply install an intelligently written program and lock you out was disheartening to say the least. The disk-locking program accomplished its directive, and accomplished it well.
This was not the first time that you had been denied access to a machine. Everyone has seen password screens without knowing a valid password to enter. What this situation implied was quite different. Here you had the entire hard disk at your disposal along with the technical savvy needed to analyze it and still you could not get in. No other situation you had ever encountered illuminated the true power of cryptography more than this. Crypto was not merely being used to prove Eddie's identity or conceal his data from your prying eyes. In this situation, crypto was being used to keep you from modifying Eddie's data in any meaningful way. For hours you dwelled on the issue and in the end, accepted defeat. Just how broad is this field that hampered your Trojan horse attack so? In what other ways can cryptography foil hacking attempts? In gaining an understanding of the cryptographic defense that foiled your attack, a Pandora's Box of possibilities was opened to you.
In those last few months on the job you infused your brethren with an inexplicable sense of hope in the workplace. It seemed that justice was in fact a thing of this world, and that the old saying “what goes around comes around” is true indeed. It's just that at your company, it seemed to come around a lot sooner for some reason. Being the good Samaritan that you are, you confided in Brian in your final week about the Ethernet client/server suite that you concocted. The torch was passed on to Brian to help make the company a more bearable place to work.
In the years that followed you heard through the grapevine that a database weenie joined the team. He had an affinity for music, and brought with him a CD collection that filled an entire wall. The tortured soul suffered from a mental condition that compelled him to listen to Kenny Rogers CDs over and over again. He quickly learned that the gods of the almighty CD-ROM did not share his taste in country-western, and they showed their wrath by ejecting his compact disks at every turn.
... and so began the quest, born of questions unanswered, to confirm intuitions and discover yet newer possibilities, a quest that would lead to a mathematician buried beneath tome and scroll in an ivory tower to the south wherein these words were inscribed... uimibfdscjuiebuspfxfjtjtg!
1The mesmerizing 56” × 80” original is entitled “Li II” and hangs in the Swiss Art Museum (see http://www.giger.com).
3One could argue that the decompilability of Java is a security weakness that does not exist in the C++ language, for example. A language that behaves akin to a cryptographic one-way function during compilation guards against this vulnerability.
4This is the sum of terms where the terms form a geometric progression.
5An active adversary could change the counters without killing the virus, and so forth.
6A problem arises when trying to design a Trojan that computes the checksum of the host concatenated with the Trojan itself. By storing the resulting hash value within the Trojan, the hash value that is computed will differ from the stored hash. When a typical hash function is used, there is little reason to suspect that a reasonable number of iterations will cause the hash to converge on a fixed-point.
7In a manner of speaking, of course.