Digital documents are something we all consume in one form or another. Malwares have been making use of this medium for a very long time indeed, and even more so given the popularity of software ebook readers and the PDF format, which is mainly used for targeted spear phishing and as an exploits vector. MS Office files are also very popular targets given that Windows has the largest market share and most of the users use these software. Some of the more popular tools are as follows:
- OfficeCat: This can be found at https://www.microsoft.com/enus/download/details.aspx?id=36852
- OfficeMalScanner: This can be found at http://www.reconstructer.org/code.html with the various options as follows and the output of the
scan mode.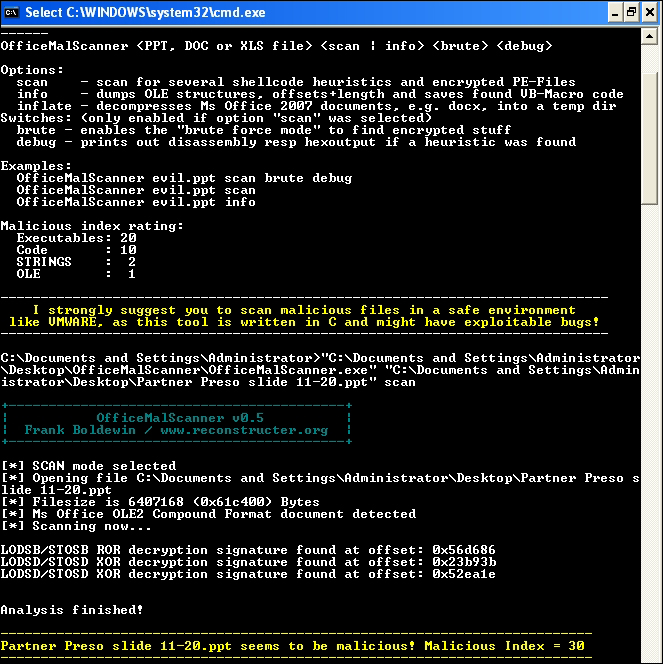
- OffVis: This can be found at https://www.microsoft.com/en-us/download/details.aspx?id=2096. As shown in the following image, it uses a hex view and a selection of parsers from the drop down menu that can aid in auditing of the MS Office documents:
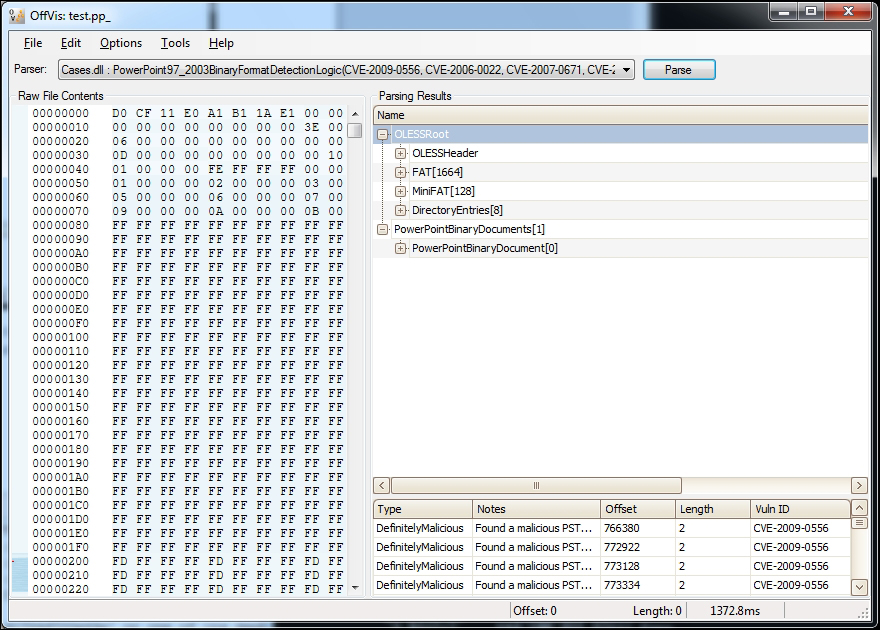
For PDF files, the extraction of Javascript, Flash content or executables is the main objective. After that, rest of the process is quite the same as regular Javascript deobfuscation, which can include exploits (including the popular heap spray) and shellcode packed inside it. A PDF document is composed of the file magic number or the signature
%PDF-1.1, followed by a hierarchy of objects replete with tags that categorize the objects, followed by an ending marker%%EOF. Some of the types are Boolean values, Number, Strings, Names, Arrays, Dictionaries, and Streams. - PDF Examiner: This can be found at https://github.com/mwtracker/pdfexaminer
- Wepawet: This can be found at http://wepawet.iseclab.org/
- PDF StreamDumper: This can be found at http://sandsprite.com/blogs/index.php?uid=7&pid=57
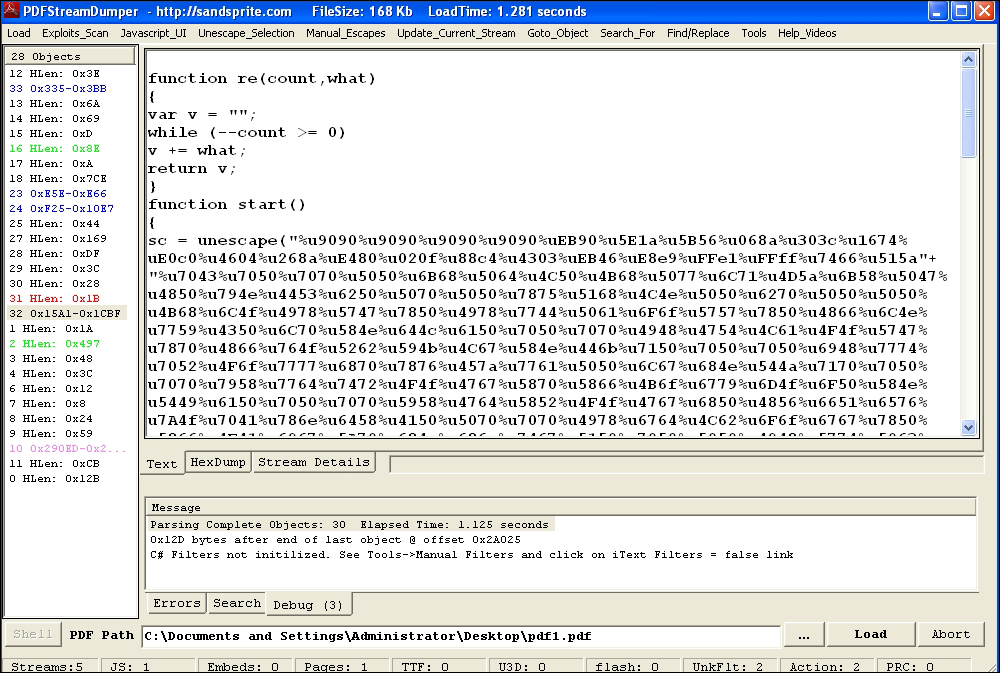
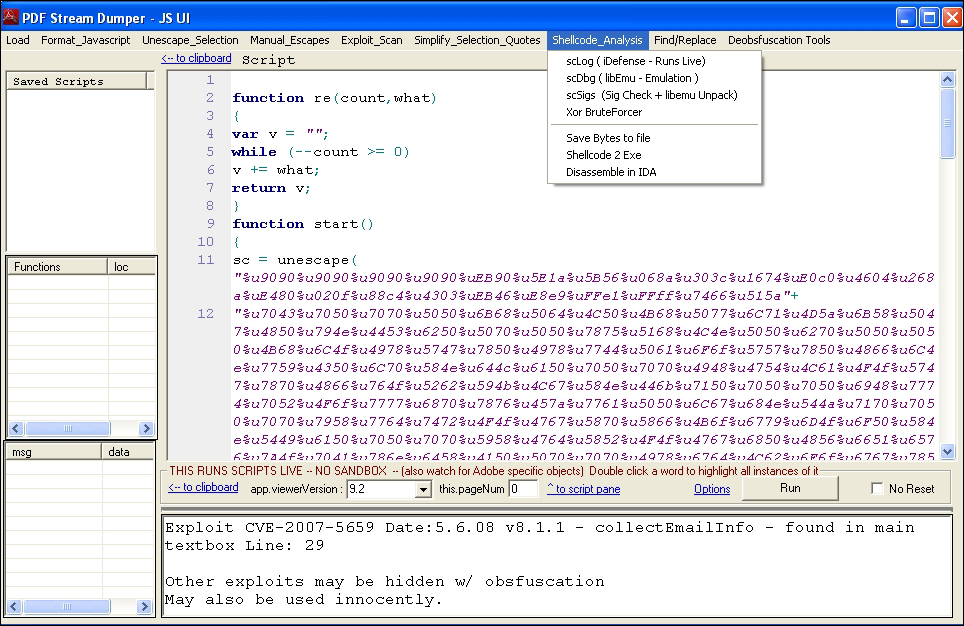
PDF StreamDumper also has a very capable and featured Javascript deobfuscation and analysis engine. The Javascript streams can be chosen from the object list at the left hand tab and initially perused with the text, hex, and object information tabs. The Javascript UI can then be invoked to commence analysis.
- SWF Decompiler: This can be found at http://www.eltima.com/products/flashdecompiler. It is one of the better products that can analyze upto ActionScript 3.0 and aid in Flash (
*.swf) files analysis.
