- Title: Vulnerability with the way \ escaped characters in http://danlec.com style links are rendered
- Reported by: danelc
- Bounty rewarded: $5,000
- Web application URL: https://hackerone.com
- Description: Hackerone is a bug bounty and vulnerability co-ordination platform used by attackers to report vulnerabilities and bugs in web applications. It is a platform that hackers use to communicate the identified vulnerabilities to companies listed there. A typical Hackerone report has four fields:
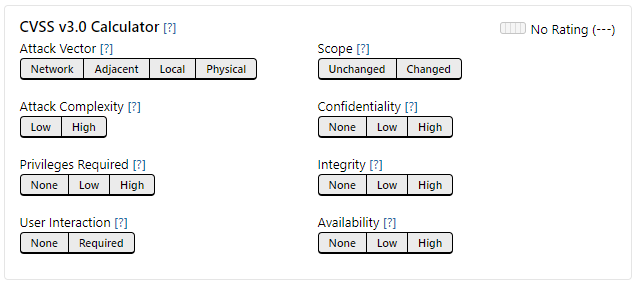
CVSS Score:
Title:
Description:
Impact:
This report is about was an XSS vulnerability identified in the parsing of /while posting links in the Hackerone reporting form description used by attackers to report vulnerabilities. It was a rather simple vulnerability that resulted in stored XSS in the Hackerone reports. The vulnerability existed due to the reason that / characters were being escaped in the reporting forms and a character string could be created to execute XSS attacks via the reporting form.
For instance, if a user pasted a text string such as <http://\<h1\>test\</h1\>>, it would be rendered as http://<h1>test</h1>, resulting in http://test.
This would allow any attacker to inject arbitrary code, such as malicious JavaScript, unauthorized image files, JS-based keyloggers, and performing open redirects. Some of the examples are given in the following sections.
