On April 4, 2016, the security researcher James Kettle, reported an SSTI vulnerability in the Angular template used by Uber. This vulnerability was exploited by James Kettle using an XSS attack. Let's check out the vulnerability.
James Kettle found the vulnerability in the developer.uber.com URL. To test it, he just sent a GET request using this URL:
https://developer.uber.com/docs/deep-linking?q=wrtz%7B%7B7*7%7D%7D
The payload entered in the q variable shows in the result the string wrtz49.
With this, James Kettle confirmed the vulnerability. Now, to exploit it, he entered the next XSS payload:
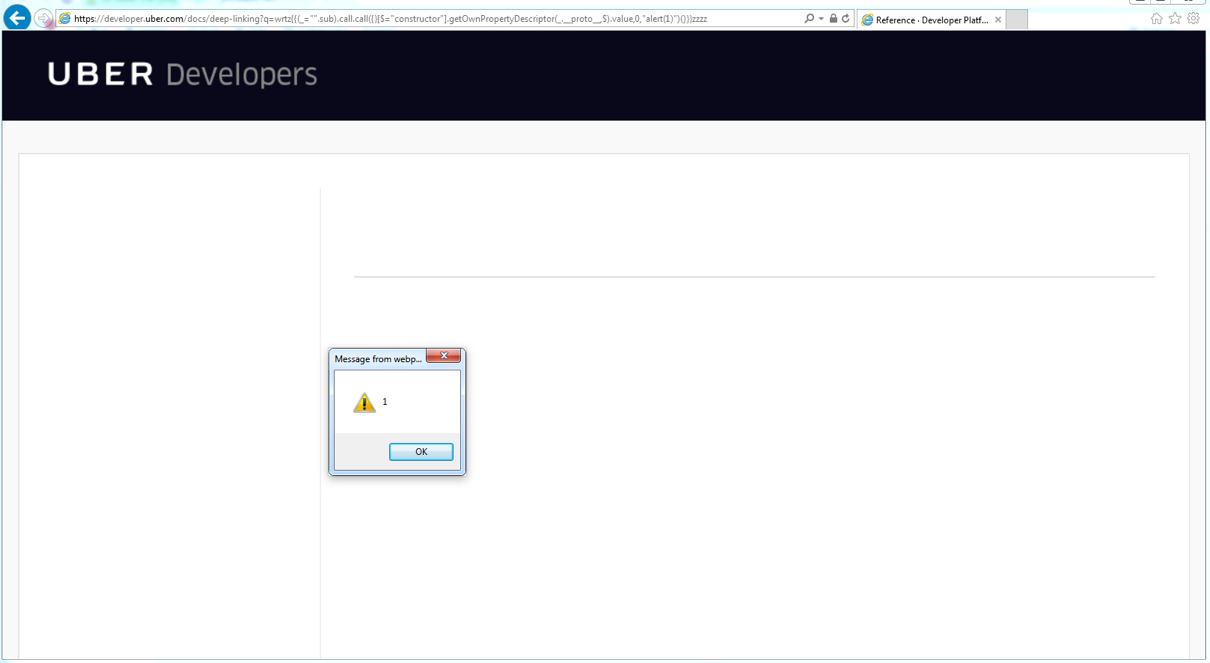
https://developer.uber.com/docs/deep-linking?q=wrtz{{(_="".sub).call.call({}[$="constructor"].getOwnPropertyDescriptor(_.__proto__,$).value,0,"alert(1)")()}}zzzz
The result is that the application showed a pop-up with the alert(1) JavaScript function being executed:
If you want to read more about this bug, checkout the next link: https://hackerone.com/reports/125027.
